Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 27 março 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
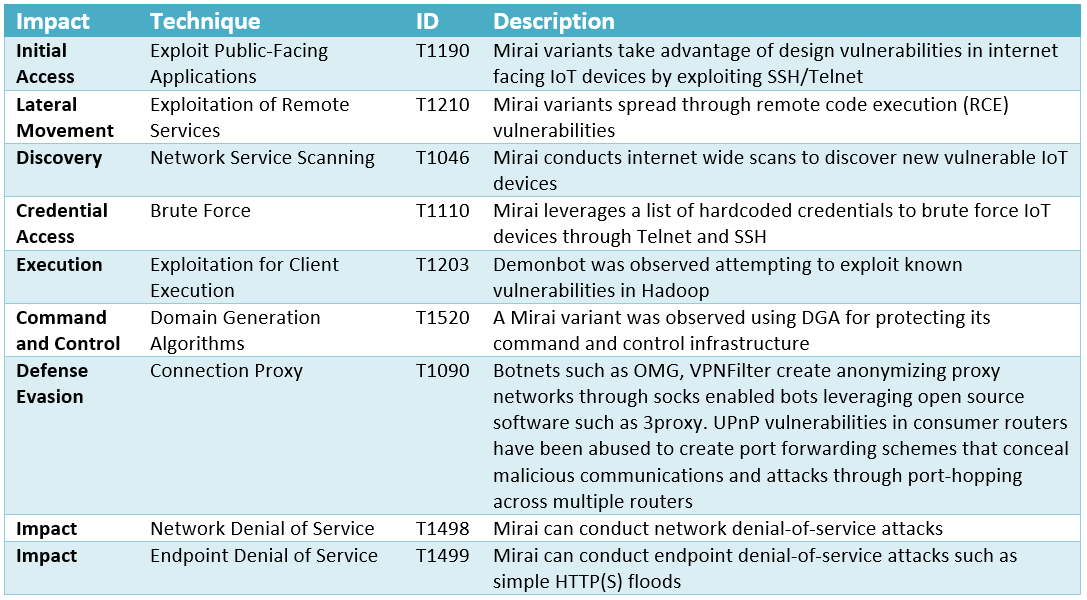
Tactics, Techniques and Procedures
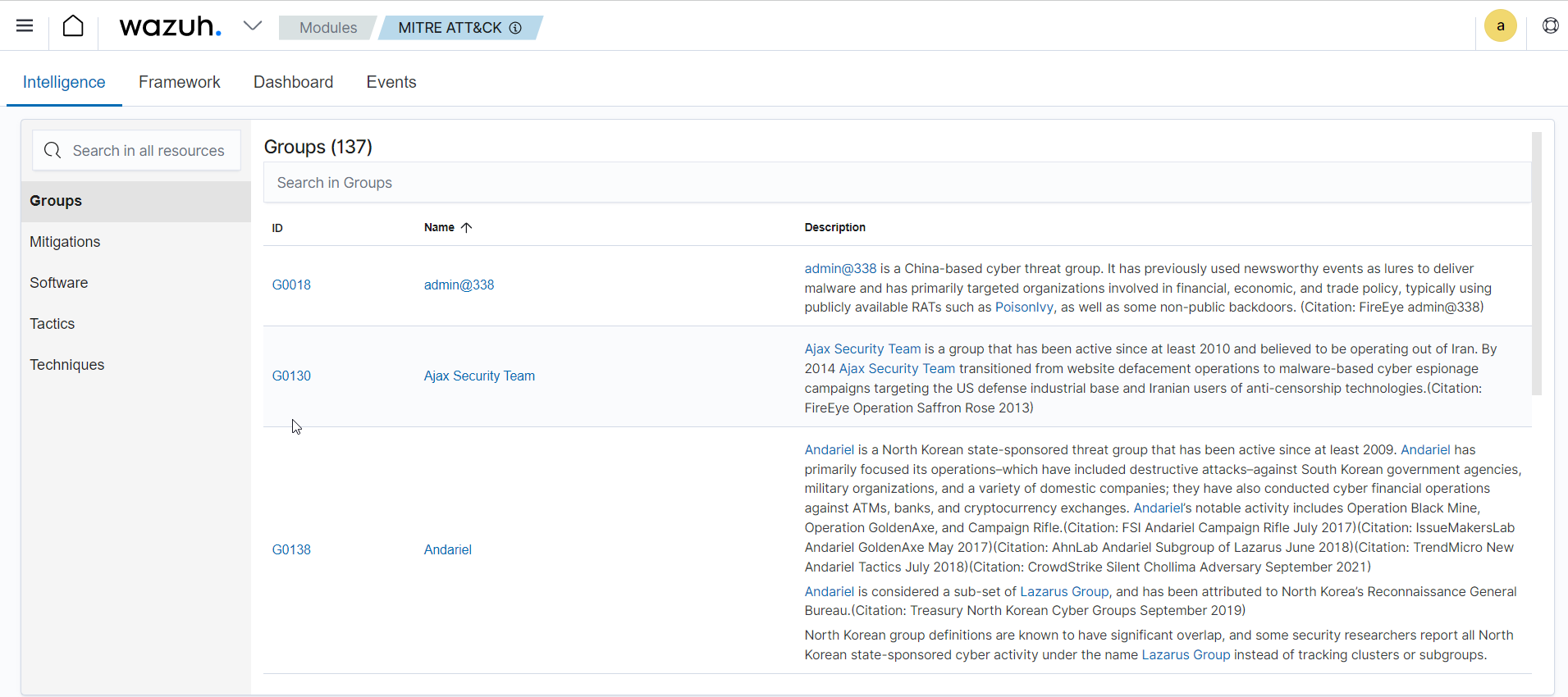
Enhancing detection with MITRE ATT&CK framework - Ruleset

Tactics, Techniques and Procedures (TTPs) to Augment Cyber Threat
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

Tactics, Techniques and Procedures of FireEye Red Team Tools
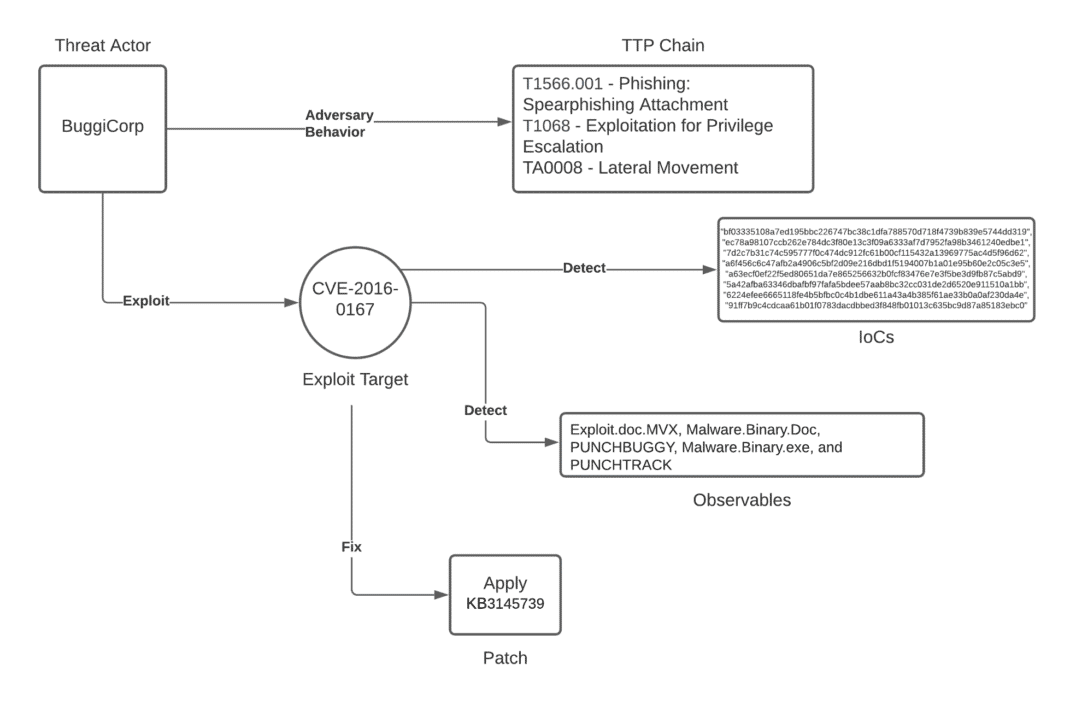
Unpacking the CVEs in the FireEye Breach - Start Here First
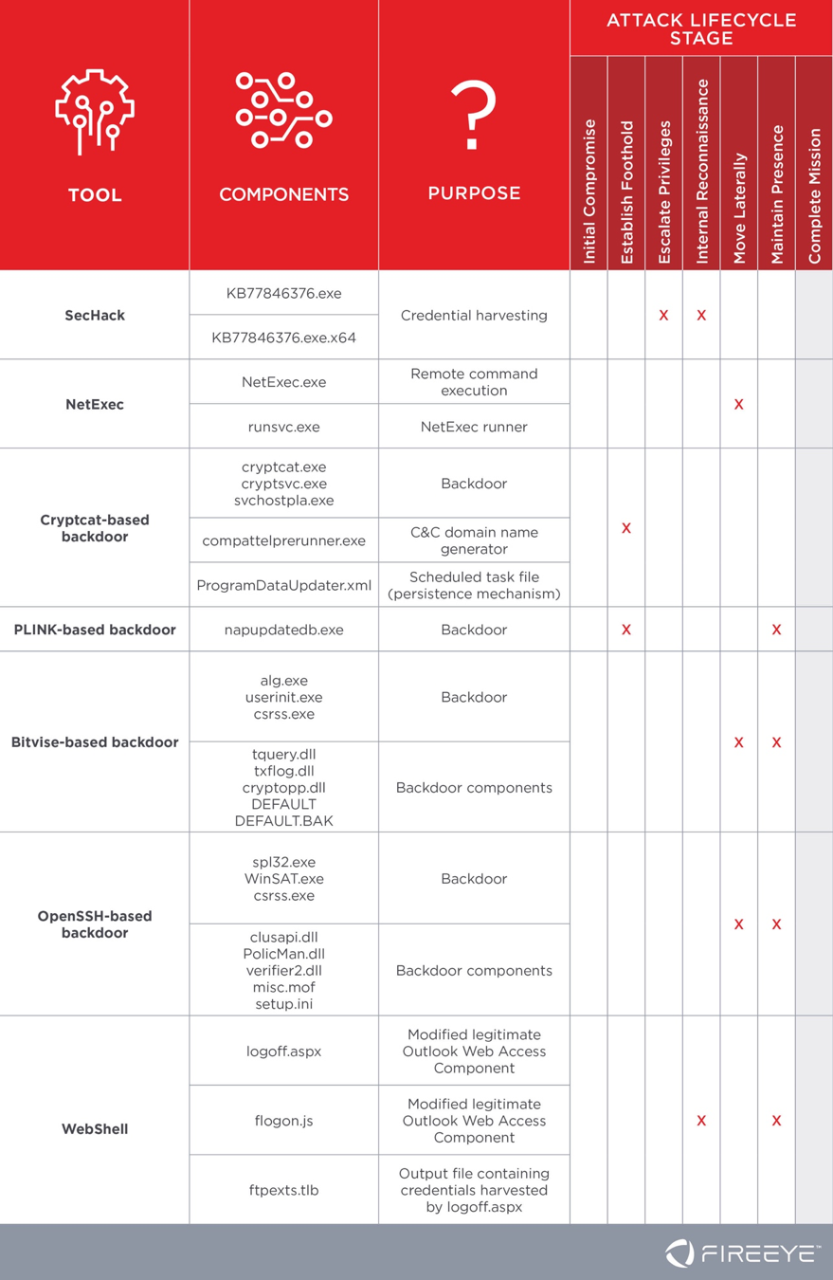
TRITON Actor TTP Profile, Custom Attack Tools, Detections, and
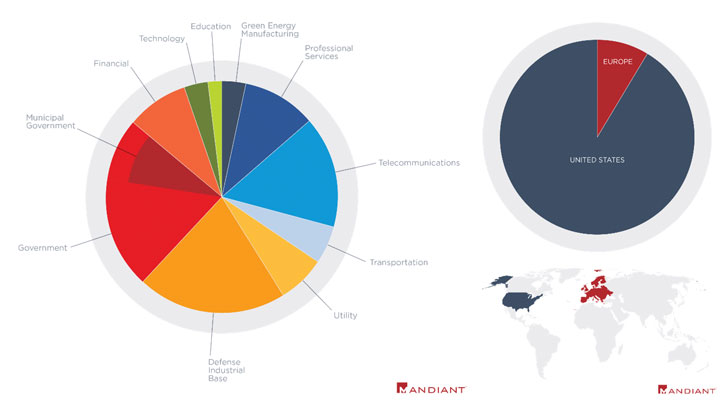
Chinese Cyber Espionage Hackers Continue to Target Pulse Secure

Threat Brief: FireEye Red Team Tool Breach
Recomendado para você
-
Bbc android iplayer download27 março 2025
-
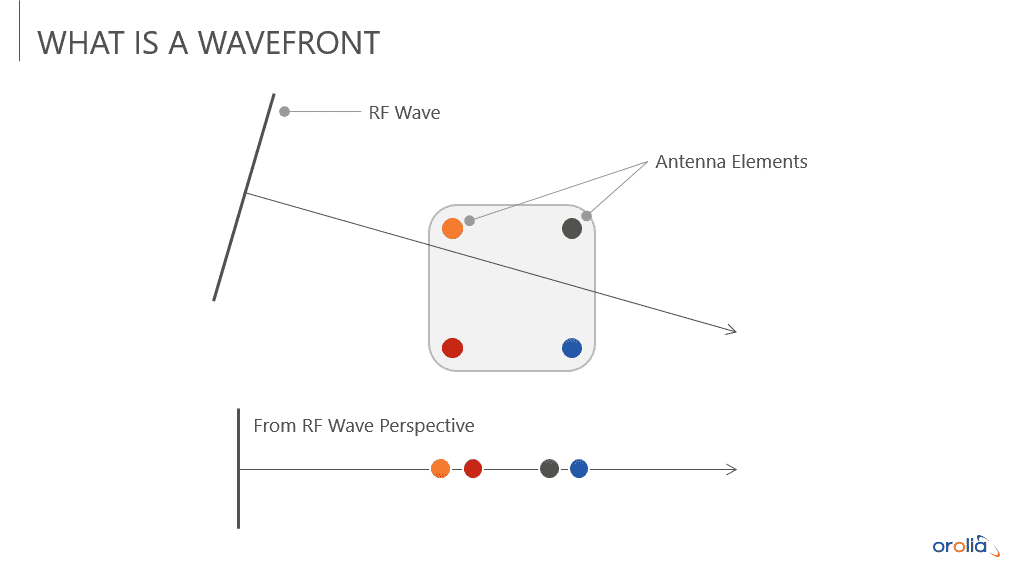 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing27 março 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing27 março 2025 -
Raj Echambadi on LinkedIn: Illinois Tech's CARNATIONS Receives $1027 março 2025
-
 Interfacing with CAST Navigation GNSS/INS Simulation Solutions27 março 2025
Interfacing with CAST Navigation GNSS/INS Simulation Solutions27 março 2025 -
Hack The Seas Village - AIS Spoofing Attacks and Some Tools - TIB27 março 2025
-
hwid-spoofer · GitHub Topics · GitHub27 março 2025
-
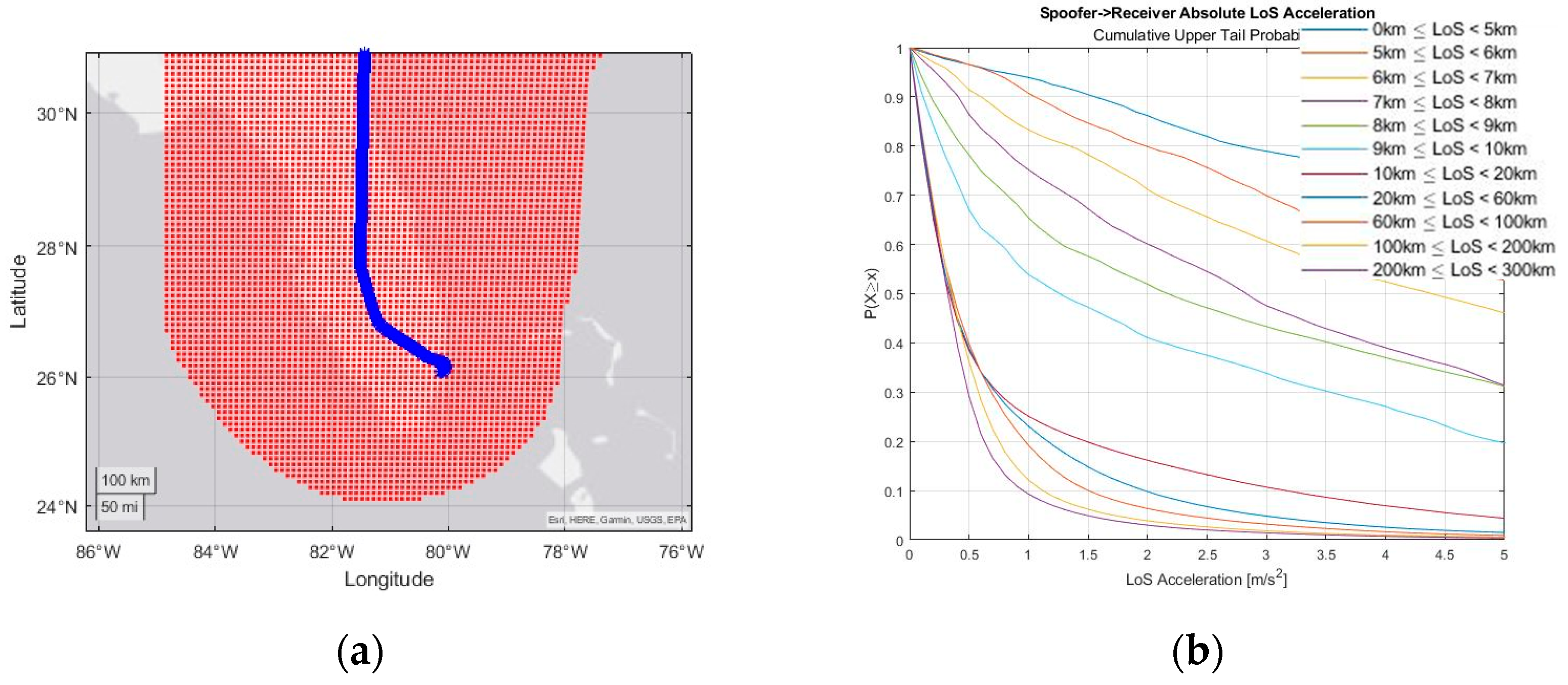 Engineering Proceedings, Free Full-Text27 março 2025
Engineering Proceedings, Free Full-Text27 março 2025 -
 DJ Max Fever - Wikipedia27 março 2025
DJ Max Fever - Wikipedia27 março 2025 -
Cracked Hwid Spoofer27 março 2025
-
 How Do MAC Spoofing Attacks Work?27 março 2025
How Do MAC Spoofing Attacks Work?27 março 2025
você pode gostar
-
 Cosmic Fear Garou vs Silver Surfer27 março 2025
Cosmic Fear Garou vs Silver Surfer27 março 2025 -
 Niko Bellic Fan Casting for GTA 427 março 2025
Niko Bellic Fan Casting for GTA 427 março 2025 -
 Link zelda altura, extra27 março 2025
Link zelda altura, extra27 março 2025 -
 Breath of the Wild 2' Still Has No Official Title 1001 Days Later27 março 2025
Breath of the Wild 2' Still Has No Official Title 1001 Days Later27 março 2025 -
 Kingsman: The Secret Service' Review - San Diego Comic-Con Unofficial Blog27 março 2025
Kingsman: The Secret Service' Review - San Diego Comic-Con Unofficial Blog27 março 2025 -
 Palavra Cantada - Bruxa Feia: Canción con letra27 março 2025
Palavra Cantada - Bruxa Feia: Canción con letra27 março 2025 -
 poki says dream has anime eyes|TikTok Search27 março 2025
poki says dream has anime eyes|TikTok Search27 março 2025 -
 Peridot Reacher, Kinsou no Vermeil Wiki27 março 2025
Peridot Reacher, Kinsou no Vermeil Wiki27 março 2025 -
 GAMES INSIDE - Elévon - Gestão do Crescimento27 março 2025
GAMES INSIDE - Elévon - Gestão do Crescimento27 março 2025 -
 TheRealShowspeedy, Roblox Wiki27 março 2025
TheRealShowspeedy, Roblox Wiki27 março 2025
