How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Last updated 03 abril 2025

In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.
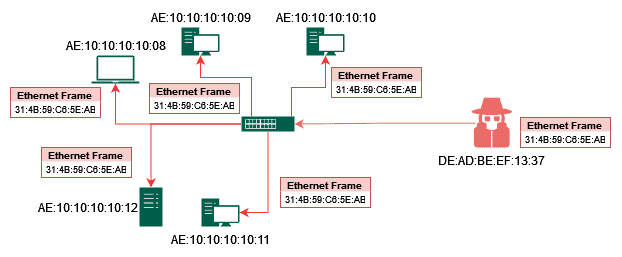
How MAC Flooding and Cloning Attacks Work?

Spoofing Attacks, Spoofing Vs Phishing
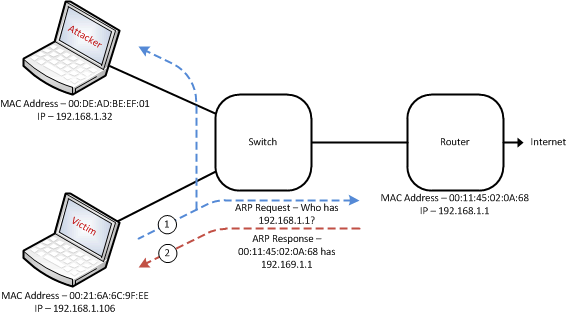
Man in the Middle (MITM) Attacks Explained: ARP Poisoining – ShortestPathFirst

MAC Address Spoofing for Bluetooth - The Security Buddy
What is a MAC address? How to find it and hide it
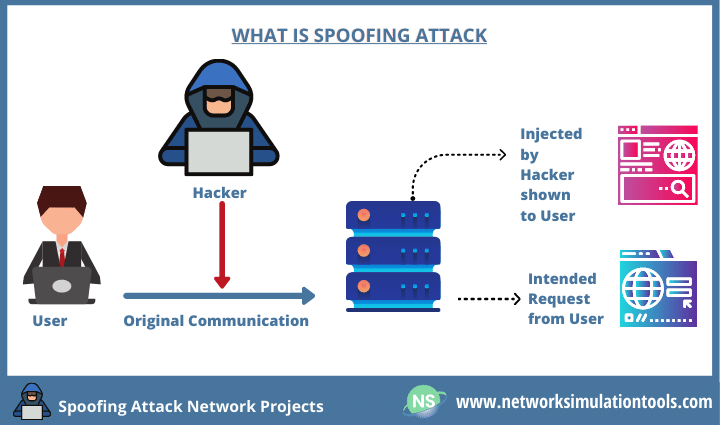
Spoofing attack Network Security Projects (Guidance)

MAC Flooding and Cloning - SY0-601 CompTIA Security+ : 1.4 - Professor Messer IT Certification Training Courses
MAC Spoofing: Understanding and Preventing Unauthorized Network Access - FasterCapital
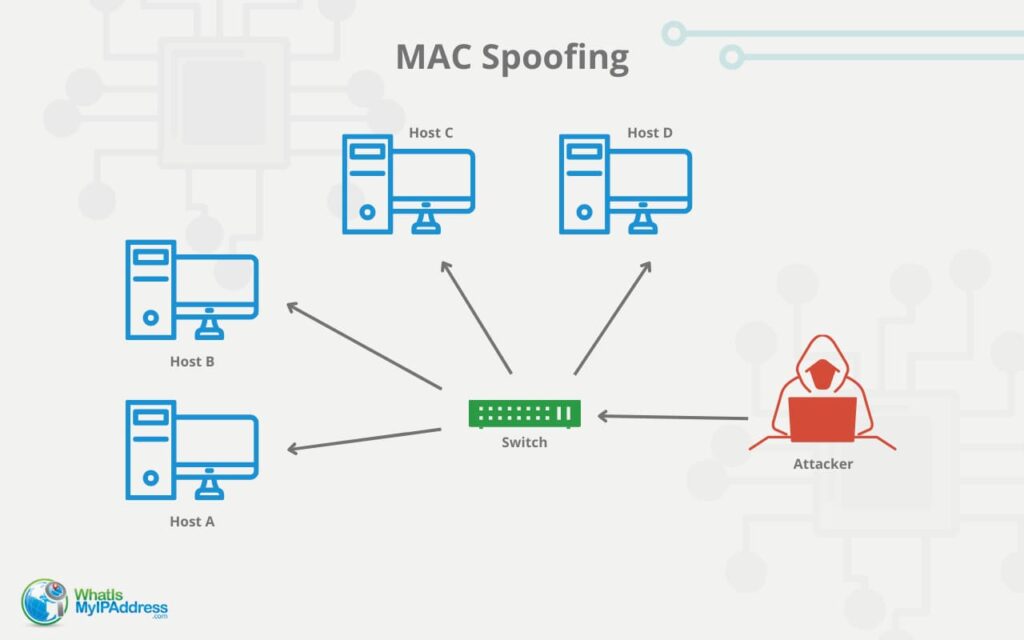
What is MAC Address Spoofing and How it Works
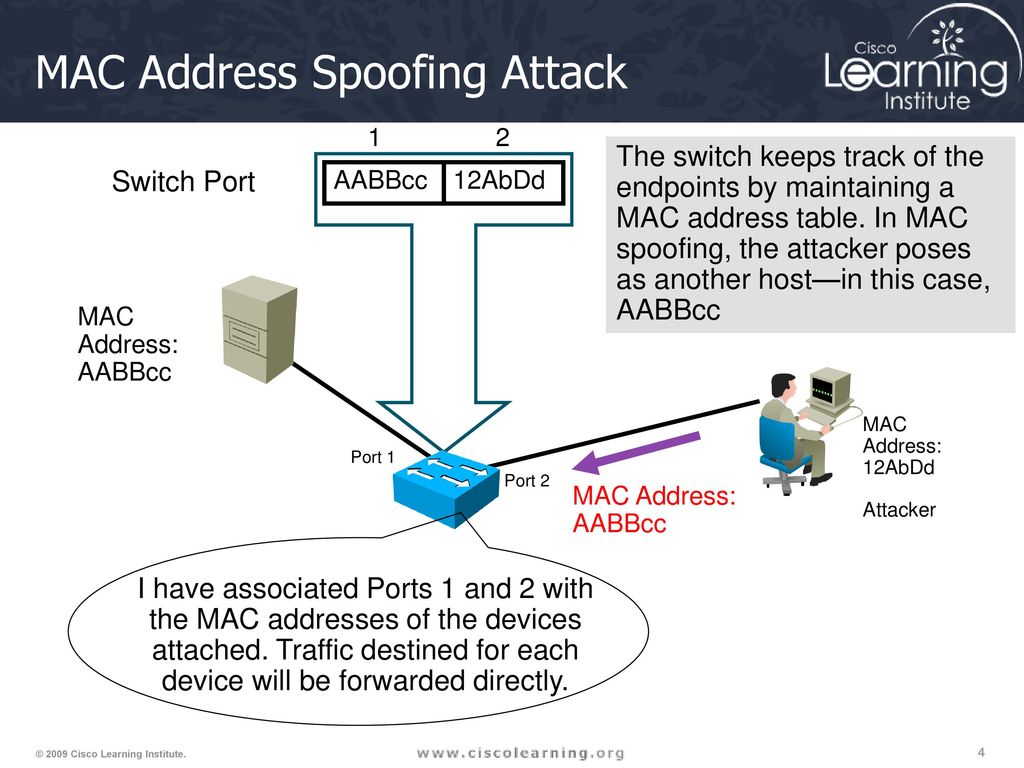
Chapter Six Securing the Local Area Network - ppt download
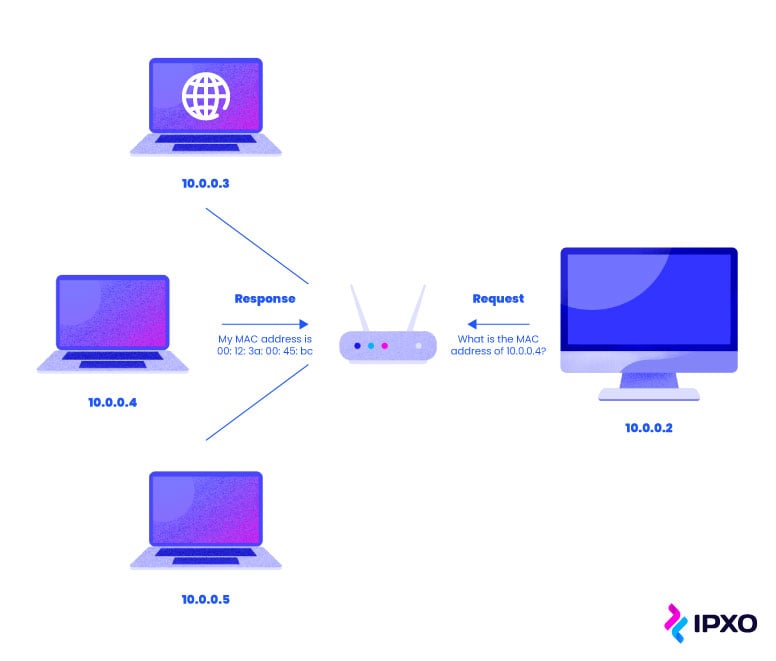
What Is Address Resolution Protocol? A Beginner's Guide to ARP - IPXO
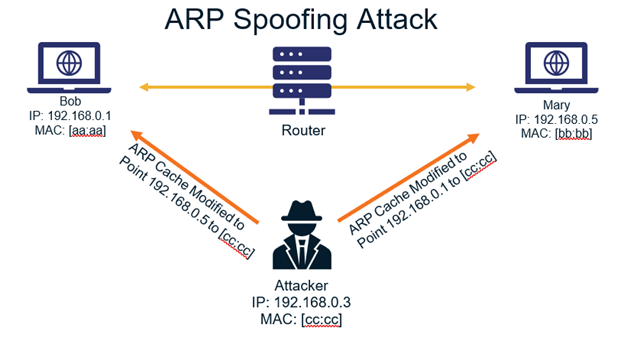
Everything You Need to Know About ARP Spoofing - Hashed Out by The SSL Store™

How To Prevent Spoofing Attacks and Understand the Main Types

How Man-in-the-Middle Attacks work
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG03 abril 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG03 abril 2025 -
 Spoofers Revealed03 abril 2025
Spoofers Revealed03 abril 2025 -
 Airline eCommerce Software & Digital Retailing Solutions03 abril 2025
Airline eCommerce Software & Digital Retailing Solutions03 abril 2025 -
 A comprehensive survey on radio frequency (RF) fingerprinting03 abril 2025
A comprehensive survey on radio frequency (RF) fingerprinting03 abril 2025 -
 CAIDA Catalog Search - A Collection of Scientific Research on the03 abril 2025
CAIDA Catalog Search - A Collection of Scientific Research on the03 abril 2025 -
 What Is Spoofing In Cybersecurity?03 abril 2025
What Is Spoofing In Cybersecurity?03 abril 2025 -
 Device Fingerprinting - SEON Docs03 abril 2025
Device Fingerprinting - SEON Docs03 abril 2025 -
 Protecting GPS From Spoofers Is Critical to the Future of03 abril 2025
Protecting GPS From Spoofers Is Critical to the Future of03 abril 2025 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation03 abril 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation03 abril 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools03 abril 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools03 abril 2025
você pode gostar
-
 Cinco formas de ver os filmes do Star Wars - MFC TOP 5 - My Family Cinema03 abril 2025
Cinco formas de ver os filmes do Star Wars - MFC TOP 5 - My Family Cinema03 abril 2025 -
Fairy Tail Opening 5 Sheet music for Flute (Solo)03 abril 2025
-
 Swoosh 360 Swimming Pool Basketball Hoop Set With Mega Ball Game- (Yellow/Blue)03 abril 2025
Swoosh 360 Swimming Pool Basketball Hoop Set With Mega Ball Game- (Yellow/Blue)03 abril 2025 -
 Fundação Copel (@FCopel) / X03 abril 2025
Fundação Copel (@FCopel) / X03 abril 2025 -
 Aventura, Florida, USA - September 20, 2019: Apple store in Aventura Mall on first day of officially started selling the iPhone 11, iPhone 11 Pro and Stock Photo - Alamy03 abril 2025
Aventura, Florida, USA - September 20, 2019: Apple store in Aventura Mall on first day of officially started selling the iPhone 11, iPhone 11 Pro and Stock Photo - Alamy03 abril 2025 -
 File:Piattaforme Doodle Jump.png - Wikimedia Commons03 abril 2025
File:Piattaforme Doodle Jump.png - Wikimedia Commons03 abril 2025 -
How to watch Attack On Titan: Final Season: Part 3 in Canada03 abril 2025
-
![512x - 32x] Chisel [MC1.6 - 1.7 & 1.12 & 1.16] - Community](https://hanfox.co.uk/other-mc/chisel/thaumcraft_preview.jpg) 512x - 32x] Chisel [MC1.6 - 1.7 & 1.12 & 1.16] - Community03 abril 2025
512x - 32x] Chisel [MC1.6 - 1.7 & 1.12 & 1.16] - Community03 abril 2025 -
 Palmeiras tem em Agustina e Thaís suas peças chaves na temporada03 abril 2025
Palmeiras tem em Agustina e Thaís suas peças chaves na temporada03 abril 2025 -
 For @googledevs #FanArtFriday I created a pseudo-3D version of the Chrome Dino Built with Zdog Greensock Stay coding! #webde…03 abril 2025
For @googledevs #FanArtFriday I created a pseudo-3D version of the Chrome Dino Built with Zdog Greensock Stay coding! #webde…03 abril 2025
