Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 18 abril 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
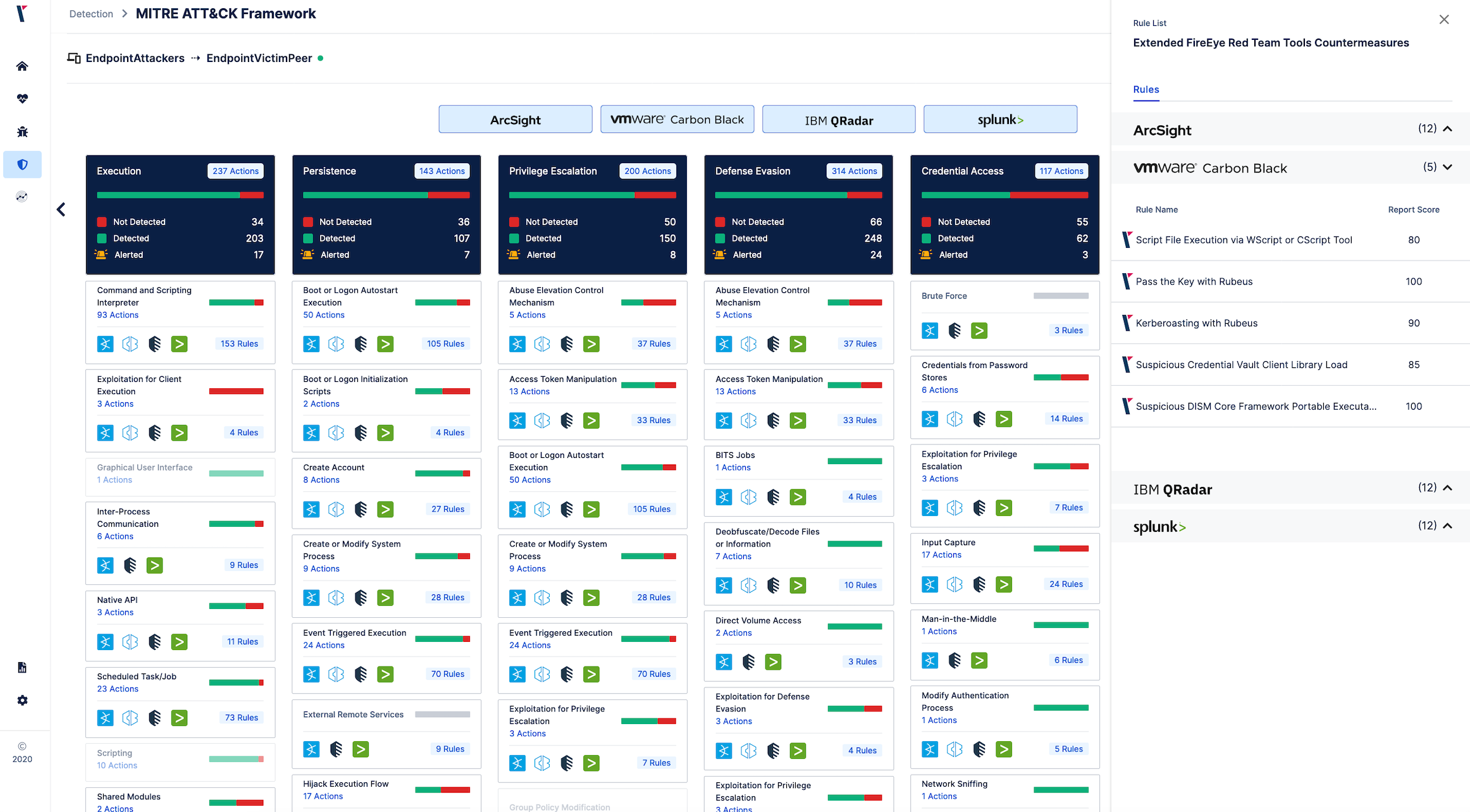
It is Time to Take Action - How to Defend Against FireEye's Red
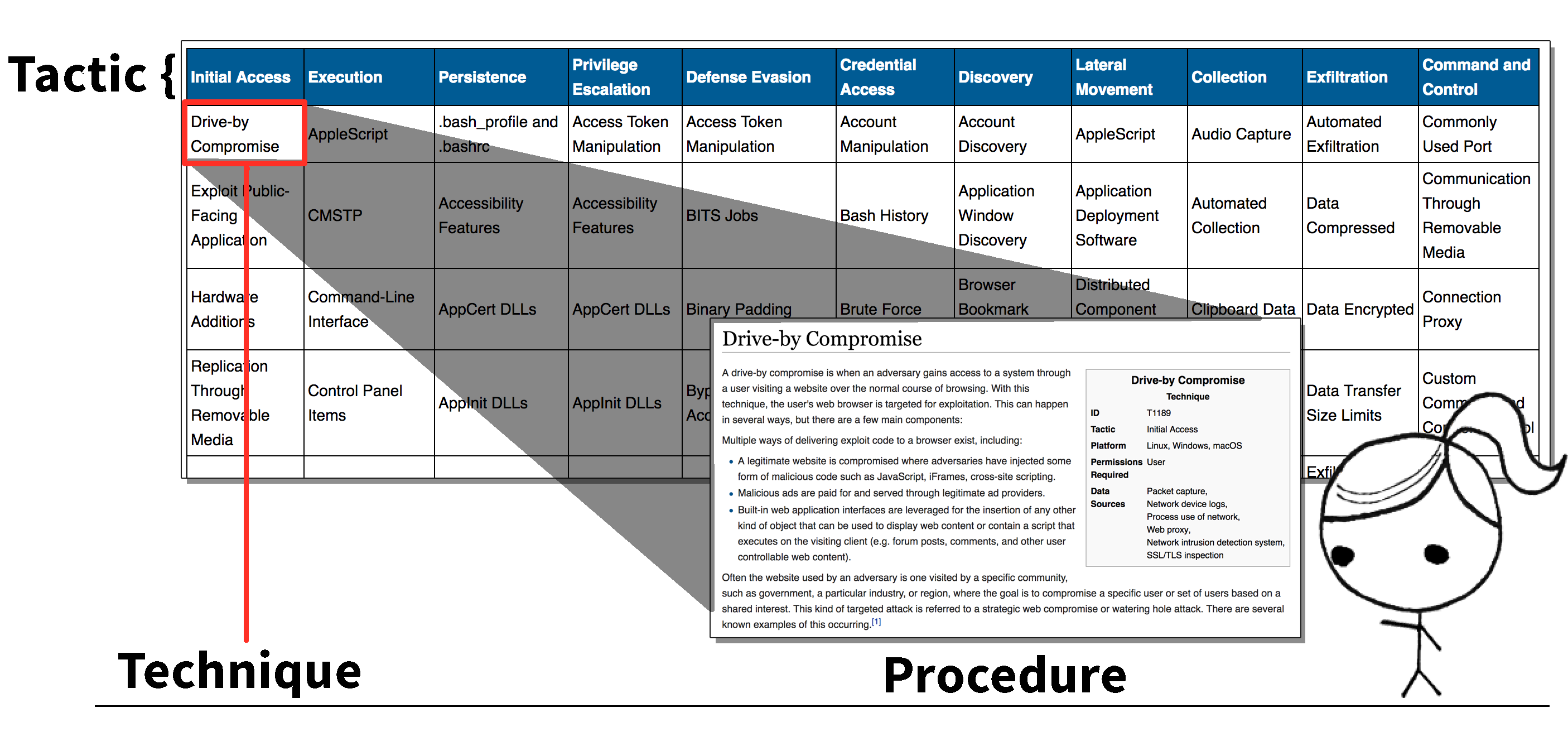
Red Teaming and MITRE ATT&CK Red Team Development and Operations

Adversary Emulation and Red Team Exercises - EDUCAUSE
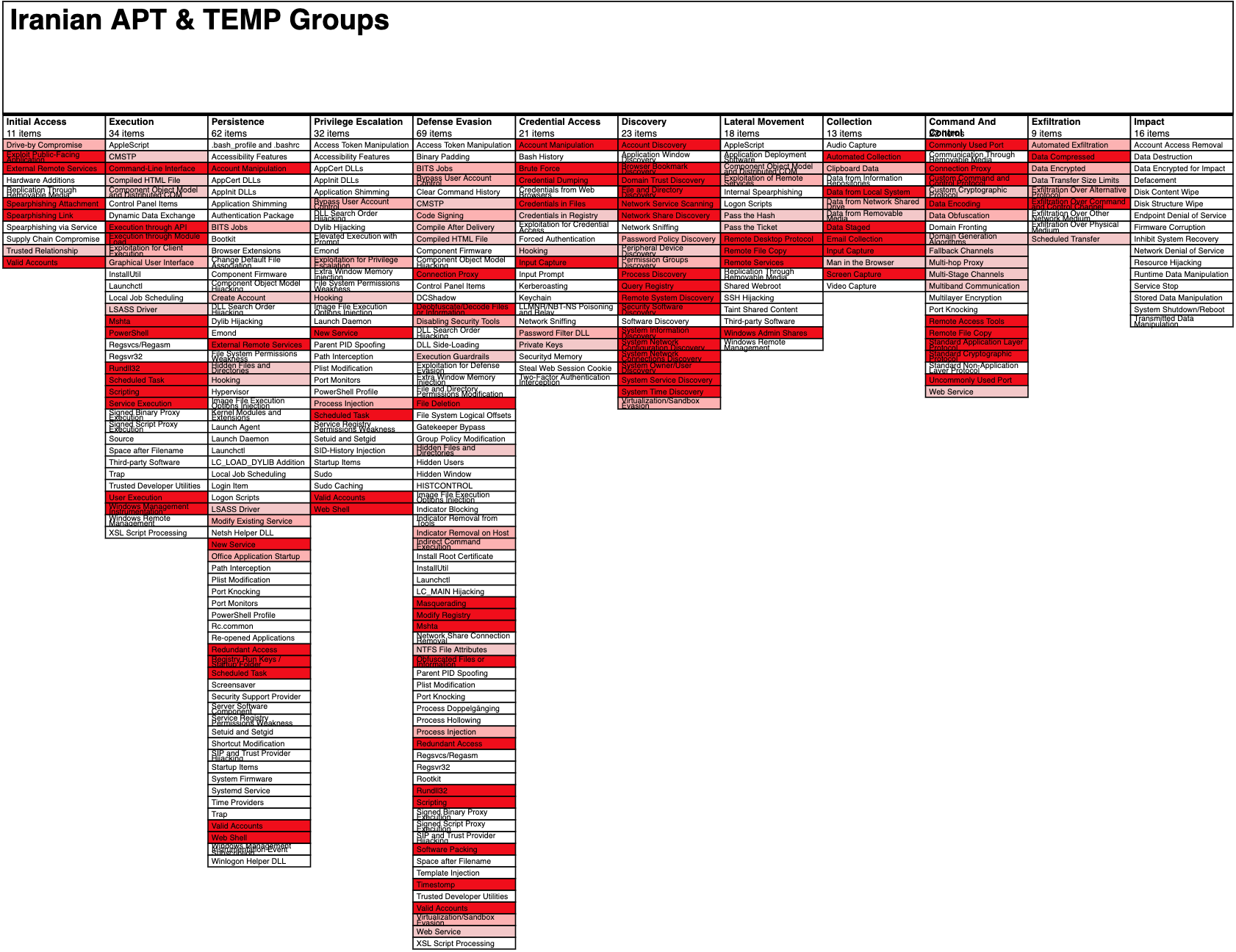
Picus Labs analyzed all the 60 stolen FireEye red team tools and

Implementing Counter Measures in ArcSight for Unauthorized Access
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

GitHub - A-poc/RedTeam-Tools: Tools and Techniques for Red Team
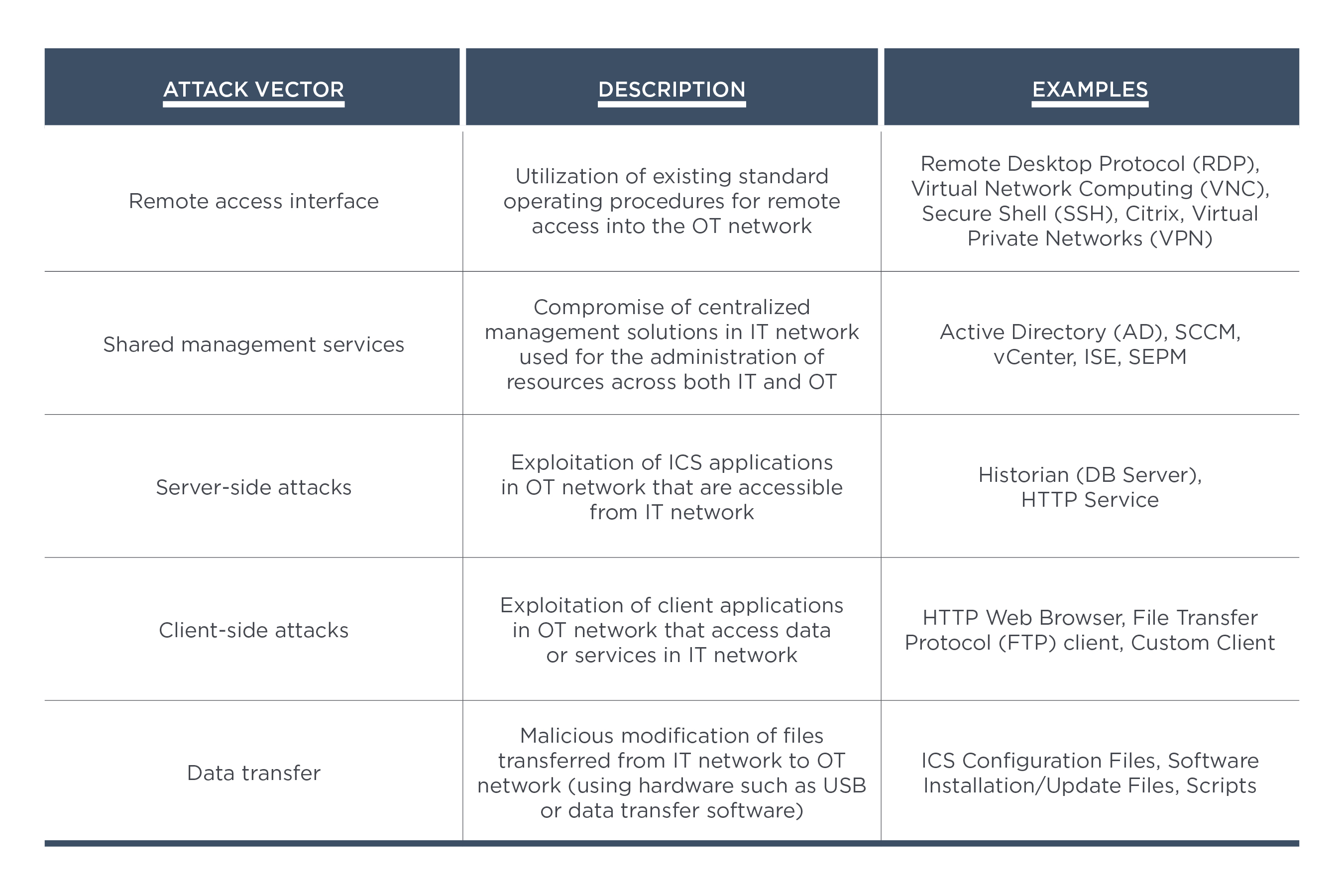
Hacking Operational Technology for Defense
Operationalizing CTI: Using MITRE ATT&CK to Hunt for and Defend

Red Team tactics – breaching the lines of defense – Comsec Global
Reprint: Security in an Era of Coercive Cyber Attacks
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

Stamus ND/NDR is Armed to Detect Stolen FireEye Red Team Tools
Recomendado para você
-
 meu cachorro morreu e agora não tenho dinheiro para spoofer no18 abril 2025
meu cachorro morreu e agora não tenho dinheiro para spoofer no18 abril 2025 -
 YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub18 abril 2025
YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub18 abril 2025 -
 Explaining and Exploring Spoofing - Deribit Insights18 abril 2025
Explaining and Exploring Spoofing - Deribit Insights18 abril 2025 -
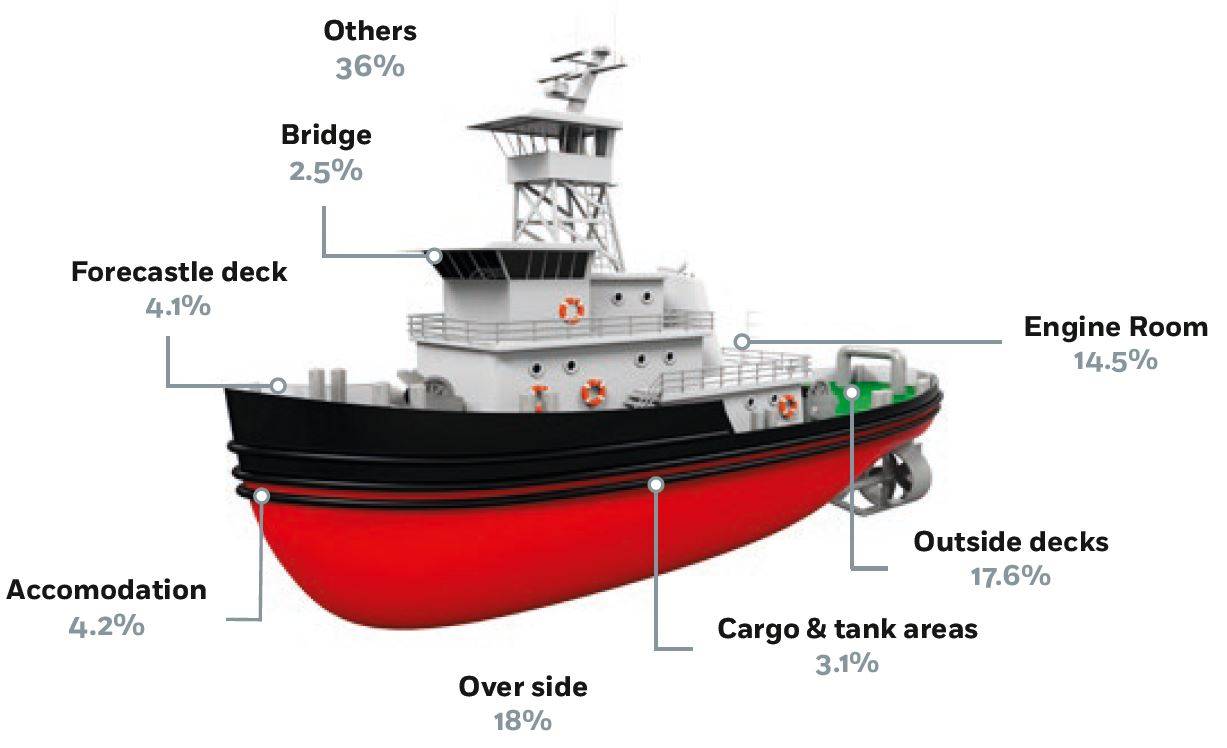 Autonomous Shipping – Cyber Hazards Ahead18 abril 2025
Autonomous Shipping – Cyber Hazards Ahead18 abril 2025 -
 Beware of Spoof Websites - RCB Bank18 abril 2025
Beware of Spoof Websites - RCB Bank18 abril 2025 -
 GootBot - Gootloader's new approach to post-exploitation18 abril 2025
GootBot - Gootloader's new approach to post-exploitation18 abril 2025 -
![Release] Spoofer](https://imgur.com/7tgB7vv.png) Release] Spoofer18 abril 2025
Release] Spoofer18 abril 2025 -
![Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)](https://i.imgur.com/6tS6Yxf.png) Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)18 abril 2025
Release] rainbow - EFI bootkit like HWID spoofer (SMBIOS/disk/NIC)18 abril 2025 -
 Licensing18 abril 2025
Licensing18 abril 2025 -
Eulen or redengine? #cheating #eulen #fivem #jus2rich #gaming18 abril 2025
você pode gostar
-
 paper duck roupa imprimir celular|TikTok Search18 abril 2025
paper duck roupa imprimir celular|TikTok Search18 abril 2025 -
 How to catch Ditto in Pokemon Go? Possible disguises & more (September 2022)18 abril 2025
How to catch Ditto in Pokemon Go? Possible disguises & more (September 2022)18 abril 2025 -
 Undertale Characters - Undertale - Sticker18 abril 2025
Undertale Characters - Undertale - Sticker18 abril 2025 -
 My Hero Academia Chapter 402: Spoilers, Release Date and more18 abril 2025
My Hero Academia Chapter 402: Spoilers, Release Date and more18 abril 2025 -
 Naruto Shippuden: Kakashi Hatake vs. Obito Uchiha Full Fight (Eng18 abril 2025
Naruto Shippuden: Kakashi Hatake vs. Obito Uchiha Full Fight (Eng18 abril 2025 -
 The Fruit of Grisaia - Wikiwand18 abril 2025
The Fruit of Grisaia - Wikiwand18 abril 2025 -
 Minecraft Original gratis :: Minecraftgratis1418 abril 2025
Minecraft Original gratis :: Minecraftgratis1418 abril 2025 -
![Video] Naruto - Naruto Uzumaki by LeisaigeArts on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/247ebae2-c6e6-4093-beb7-b4c42715d3d4/dfzj0zc-92f24dcc-b6e7-4297-9824-ac772bde1a76.jpg?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzI0N2ViYWUyLWM2ZTYtNDA5My1iZWI3LWI0YzQyNzE1ZDNkNFwvZGZ6ajB6Yy05MmYyNGRjYy1iNmU3LTQyOTctOTgyNC1hYzc3MmJkZTFhNzYuanBnIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.bxpoo6I2Zj4LhrZfkXjq-7vCrZIP4U56eFNPNc2TVVM) Video] Naruto - Naruto Uzumaki by LeisaigeArts on DeviantArt18 abril 2025
Video] Naruto - Naruto Uzumaki by LeisaigeArts on DeviantArt18 abril 2025 -
 Read Peter Grill To Kenja No Jikan Chapter 2 - Manganelo18 abril 2025
Read Peter Grill To Kenja No Jikan Chapter 2 - Manganelo18 abril 2025 -
 Não faças da tua vida um rascunho. Poderás não ter tempo de passá-la a - Fraseteca18 abril 2025
Não faças da tua vida um rascunho. Poderás não ter tempo de passá-la a - Fraseteca18 abril 2025
