Playing Chess with the Adversary: Value in Security Controls
Por um escritor misterioso
Last updated 26 março 2025


Cybersecurity Sucks And Here's Why: Three Truths To Accept

The Art of Cybersecurity Strategy - Lessons from a Chess Master 🤝

4 Reasons why CISOs should adopt threat intelligence

PDF) Risk intelligence: a Centre for Risk Research discussion document

How do you even cheat in chess? Artificial intelligence and Morse code

Examples where DeepChess prefers to play the same positional sacrifices

How do you even cheat in chess? Artificial intelligence and Morse code

Game Theory and the Nuclear Game Against North Korea - Bloomberg

The Fog Of Metawar - by TJ (Teej) Ragsdale - Vulpine View
Recomendado para você
-
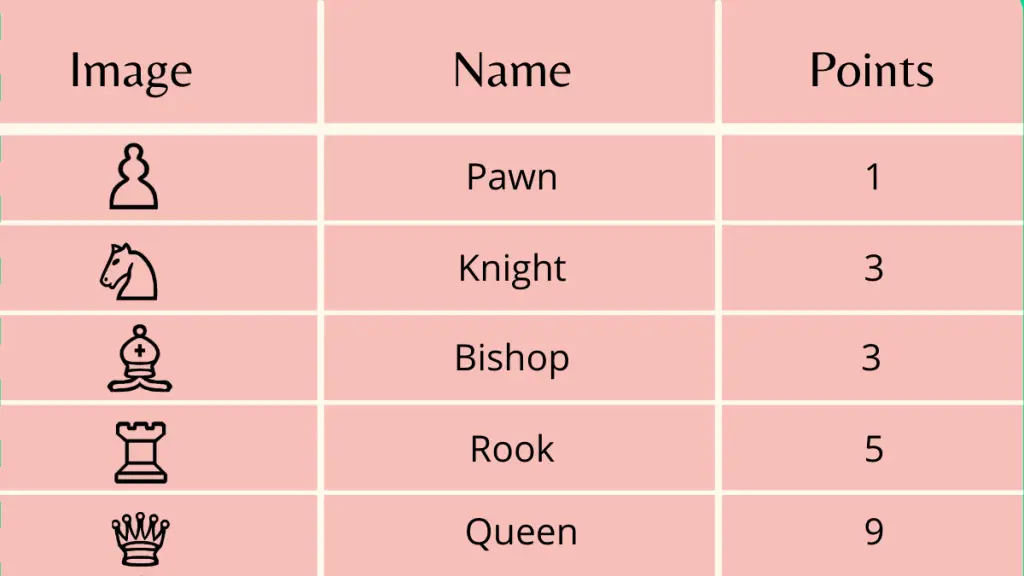 Names Of Chess Pieces and their moves - ChessEasy26 março 2025
Names Of Chess Pieces and their moves - ChessEasy26 março 2025 -
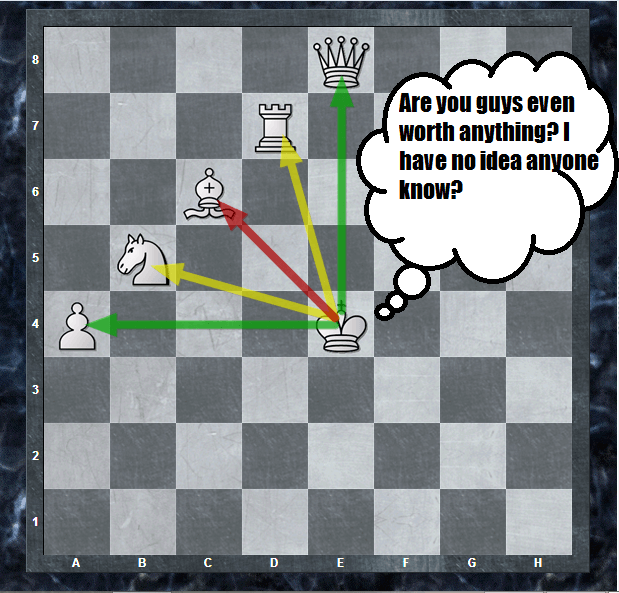 Chess Piece Relative Value26 março 2025
Chess Piece Relative Value26 março 2025 -
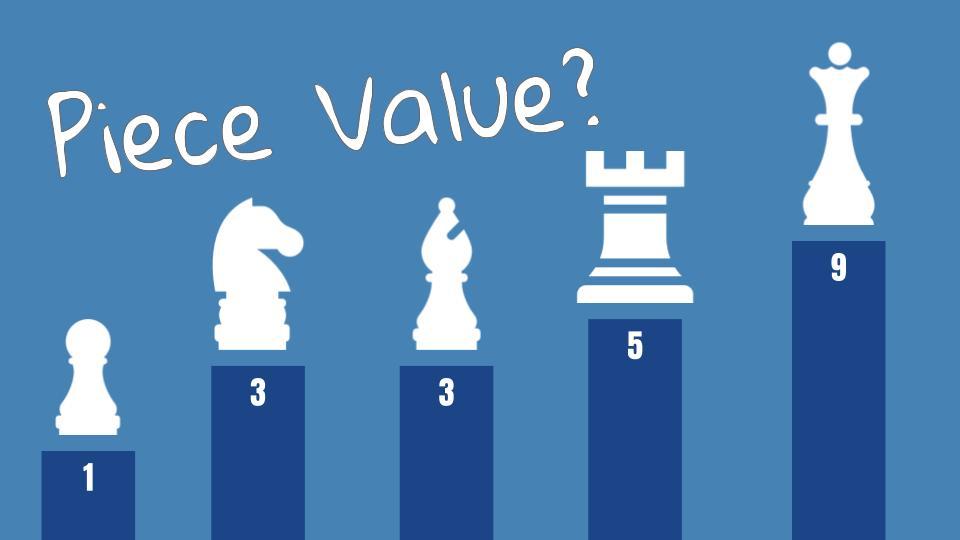 Relative Value of Chess Pieces26 março 2025
Relative Value of Chess Pieces26 março 2025 -
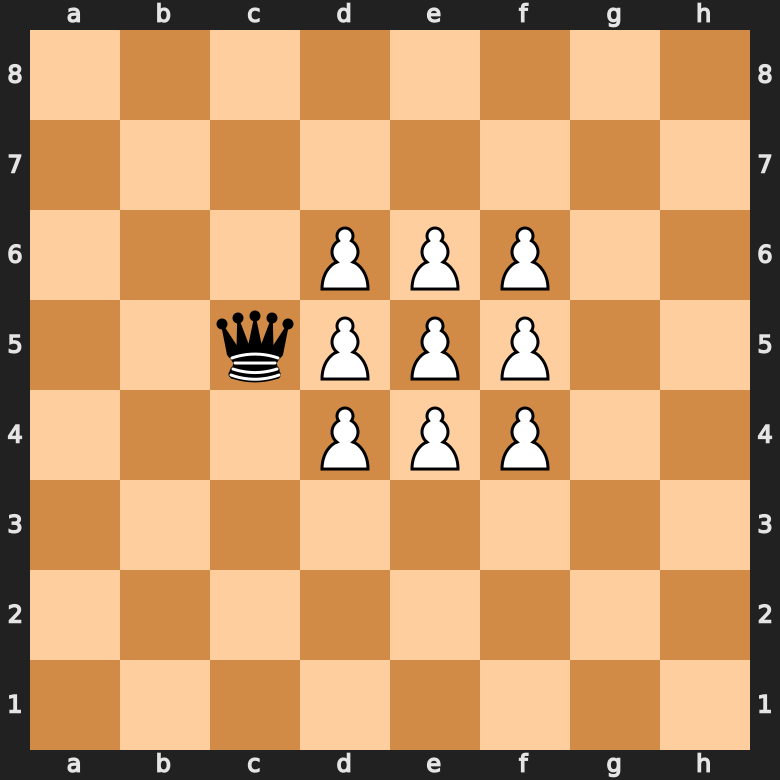 Chess Piece Value: How Much Is Each Chess Piece Worth? (List!)26 março 2025
Chess Piece Value: How Much Is Each Chess Piece Worth? (List!)26 março 2025 -
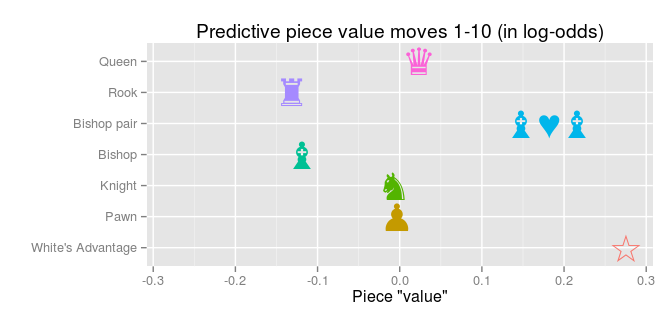 Big Data and Chess Follow-up: Predictive Piece Values Over the Course of a Game26 março 2025
Big Data and Chess Follow-up: Predictive Piece Values Over the Course of a Game26 março 2025 -
 Point Values of Chess Pieces: Beginner's Guide - EnthuZiastic26 março 2025
Point Values of Chess Pieces: Beginner's Guide - EnthuZiastic26 março 2025 -
 The Value of Luxury Wooden Chess Sets and Pieces – Staunton Castle26 março 2025
The Value of Luxury Wooden Chess Sets and Pieces – Staunton Castle26 março 2025 -
Chess Terminology You Should Know: Piece Values (Part 7) #chess #chess26 março 2025
-
 ▷ Chess piece values: What is the most valuable piece of chess26 março 2025
▷ Chess piece values: What is the most valuable piece of chess26 março 2025 -
 WE Games Best Value Tournament Chess Set - Staunton Chess Pieces and Green Roll-Up Vinyl Chess Board26 março 2025
WE Games Best Value Tournament Chess Set - Staunton Chess Pieces and Green Roll-Up Vinyl Chess Board26 março 2025
você pode gostar
-
 Rayman Legends Gra PS4 (Kompatybilna z PS5)26 março 2025
Rayman Legends Gra PS4 (Kompatybilna z PS5)26 março 2025 -
 One Piece X Male Reader26 março 2025
One Piece X Male Reader26 março 2025 -
 Yama no Susume: Next Summit - Episode 12 discussion - FINAL : r/anime26 março 2025
Yama no Susume: Next Summit - Episode 12 discussion - FINAL : r/anime26 março 2025 -
 Lemmings (DOS) - Video Game Music Preservation Foundation Wiki26 março 2025
Lemmings (DOS) - Video Game Music Preservation Foundation Wiki26 março 2025 -
 Icons de Personagens Todo Dia on X: 🎭Icons do Baki Hanma 📺Anime26 março 2025
Icons de Personagens Todo Dia on X: 🎭Icons do Baki Hanma 📺Anime26 março 2025 -
 The Ice King Freeze Dance! 🥶👑 /// Danny Go! Brain Break26 março 2025
The Ice King Freeze Dance! 🥶👑 /// Danny Go! Brain Break26 março 2025 -
 Neptunia x Senran Kagura: Ninja Wars - Review - NookGaming26 março 2025
Neptunia x Senran Kagura: Ninja Wars - Review - NookGaming26 março 2025 -
 GeForce RTX 3080 vs Radeon RX 6800 XT: High-end GPU Face Off26 março 2025
GeForce RTX 3080 vs Radeon RX 6800 XT: High-end GPU Face Off26 março 2025 -
 SBTRKT 4X4 Magic Speed Cube Stickerless Professional 426 março 2025
SBTRKT 4X4 Magic Speed Cube Stickerless Professional 426 março 2025 -
 Títulos e resumos dos episódios do live-action de One Piece26 março 2025
Títulos e resumos dos episódios do live-action de One Piece26 março 2025
