Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Last updated 31 março 2025

Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Joker Malware Apps Once Again Bypass Google's Security to Spread
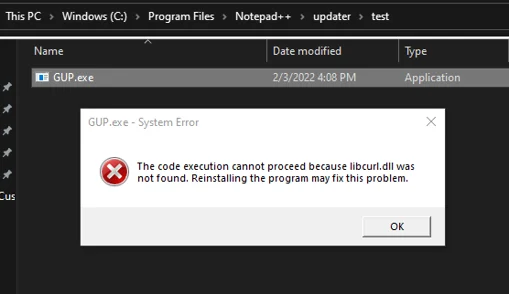
THREAT ANALYSIS REPORT: DLL Side-Loading Widely (Ab)Used

Attackers uses repackaging to publish forged applications on

How cybercriminals evade mobile app store security measures

Google describes how malware for Android can infiltrate the Google

Life cycle of Promon Shield's native library.

What Is Rootkit?

Android Applications Pentesting - HackTricks

BrainTest - A New Level of Sophistication in Mobile Malware
Recomendado para você
-
 Roblox Evade Codes (Updated August 2023) - Hardcore Gamer31 março 2025
Roblox Evade Codes (Updated August 2023) - Hardcore Gamer31 março 2025 -
🔥New Roblox Working *BYPASSED* Audio Codes/IDs in 2023! #fyp #bypasse, Better Call Saul31 março 2025
-
 Roblox music codes, The best song IDs to use31 março 2025
Roblox music codes, The best song IDs to use31 março 2025 -
 NEW* ALL WORKING CODES FOR EVADE IN 2023! ROBLOX EVADE CODES31 março 2025
NEW* ALL WORKING CODES FOR EVADE IN 2023! ROBLOX EVADE CODES31 março 2025 -
 Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X31 março 2025
Hexagon Development Community on X: Use code 'luckyday' in Evade for some pin thing. There's also an update out that's kinda cool / X31 março 2025 -
 Roblox Evolution Evade Codes (December 2023) - Pro Game Guides31 março 2025
Roblox Evolution Evade Codes (December 2023) - Pro Game Guides31 março 2025 -
 CODES – Evade! - Rick News31 março 2025
CODES – Evade! - Rick News31 março 2025 -
 DragonSpark Attacks Evade Detection with SparkRAT and Golang31 março 2025
DragonSpark Attacks Evade Detection with SparkRAT and Golang31 março 2025 -
 CALCRIM No. 2827. Concealing Property With Intent to Evade Tax31 março 2025
CALCRIM No. 2827. Concealing Property With Intent to Evade Tax31 março 2025 -
 20% Off Evade PROMO CODE, COUPONS October 202331 março 2025
20% Off Evade PROMO CODE, COUPONS October 202331 março 2025
você pode gostar
-
 Pure cotton red fashion slim fit wedding suit for groom - Ottavio Nuccio Gala31 março 2025
Pure cotton red fashion slim fit wedding suit for groom - Ottavio Nuccio Gala31 março 2025 -
 Bleach Thousand Year Blood War Episode 9 Review: The Stronger31 março 2025
Bleach Thousand Year Blood War Episode 9 Review: The Stronger31 março 2025 -
 Boruto Episode 195: Release date and time on Crunchyroll31 março 2025
Boruto Episode 195: Release date and time on Crunchyroll31 março 2025 -
 Chained, Tower Defense X Wiki31 março 2025
Chained, Tower Defense X Wiki31 março 2025 -
 Fangs says she'll be debuting very soon, many people believe it's against JustaMinx on Misfits 006 : r/BoxingNews31 março 2025
Fangs says she'll be debuting very soon, many people believe it's against JustaMinx on Misfits 006 : r/BoxingNews31 março 2025 -
Olx Login em Porto - OLX Portugal31 março 2025
-
 Life Lessons from Chess - ChessBase India31 março 2025
Life Lessons from Chess - ChessBase India31 março 2025 -
 meu simulador de vida de mãe grávida - novo jogo grátis de31 março 2025
meu simulador de vida de mãe grávida - novo jogo grátis de31 março 2025 -
 For anyone who plays Asphalt and the crew 2 on ps4, i usually do the decals from cars on A9 and do them on the crew 2,left is huracan, middle is jesko31 março 2025
For anyone who plays Asphalt and the crew 2 on ps4, i usually do the decals from cars on A9 and do them on the crew 2,left is huracan, middle is jesko31 março 2025 -
 Fredbear and Friends: Revelation by RedCraft86 - Game Jolt31 março 2025
Fredbear and Friends: Revelation by RedCraft86 - Game Jolt31 março 2025
