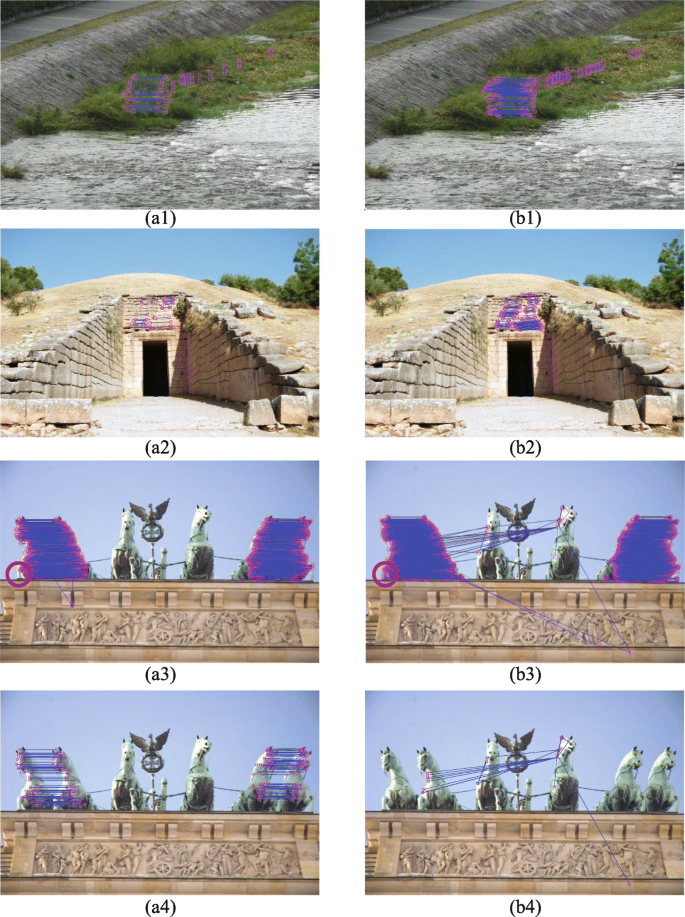
a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 01 abril 2025

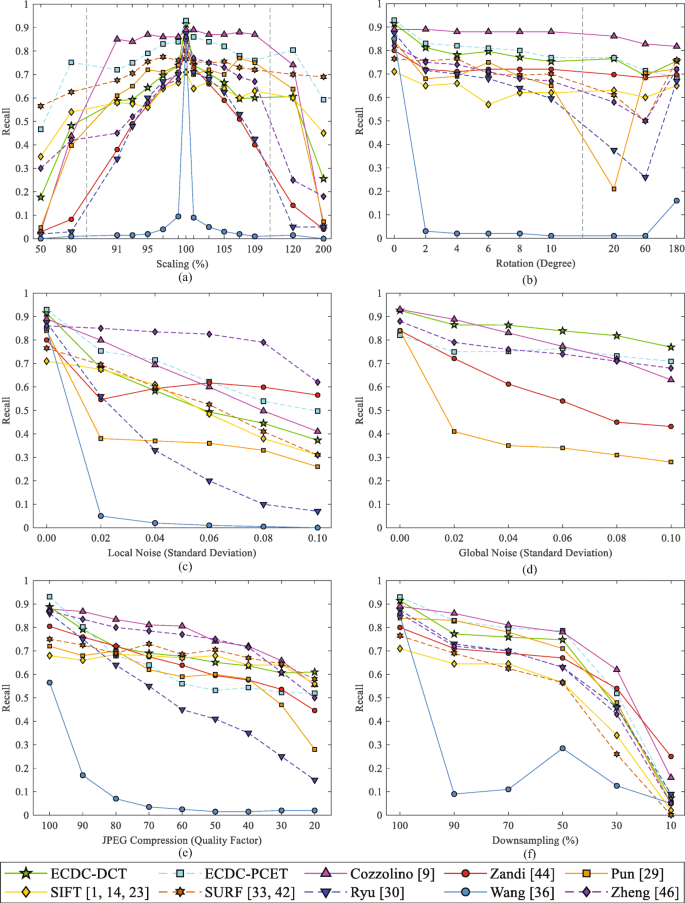
Copy-move image forgery detection based on evolving circular domains coverage
Week 1 — Copy Move Forgery Detection, by Eflatun Doğa AYDIN, BBM406 Spring 2021 Projects
Copy-move image forgery detection based on evolving circular domains coverage
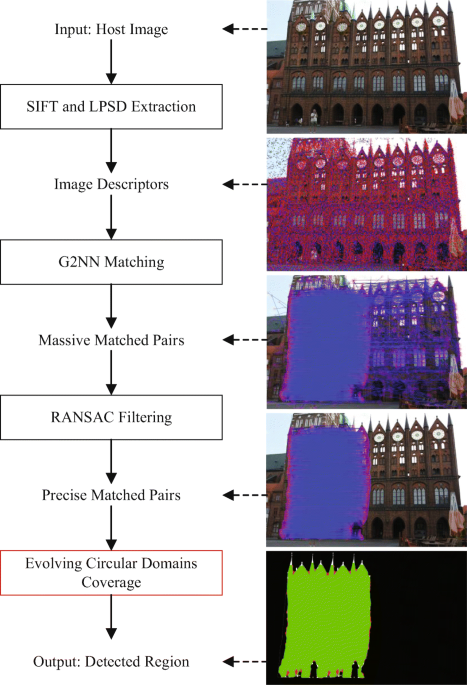
Copy-move image forgery detection based on evolving circular domains coverage

Copy-move forgery detection using binary discriminant features - ScienceDirect

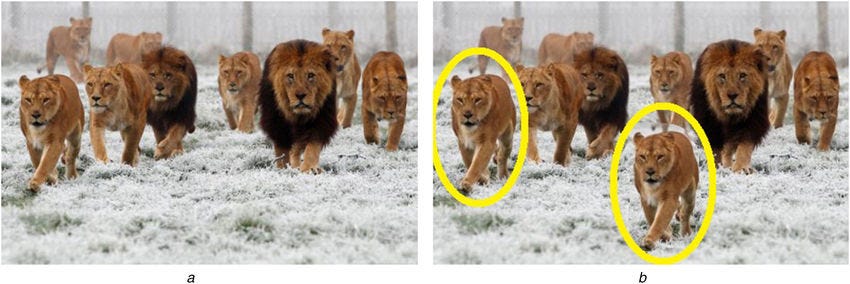
Example for copy-move forgery from [MS07] (original image left
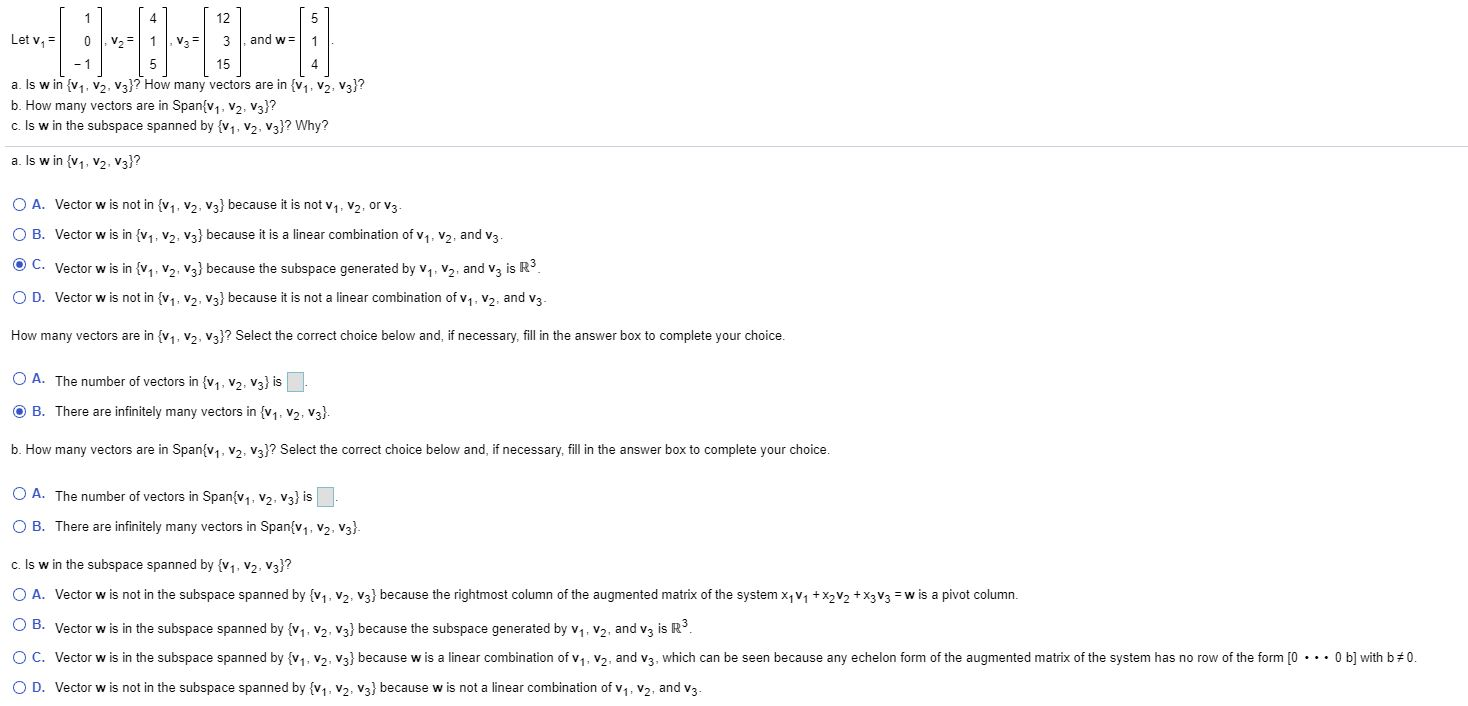
Solved Let v, = 0 V2 = 1.133 and w= 1 a. Is w in {V1, V2

Copy-move image forgery detection based on evolving circular domains coverage
GitHub - niyishakapatrick/Copy-move-forgery-detection-using-image-blobs-BRISK-features.: One of the most frequently used types of digital image forgery is copying one area in the image and pasting it into another area of the same image. This
Recomendado para você
-
 G1/F1 System - Genera - 3D Printing & Additive Manufacturing01 abril 2025
G1/F1 System - Genera - 3D Printing & Additive Manufacturing01 abril 2025 -
 F1 Car Simplify Transform】Transformers G1 Series Third party custom Mirage DX9 D03 Car Robot Toys01 abril 2025
F1 Car Simplify Transform】Transformers G1 Series Third party custom Mirage DX9 D03 Car Robot Toys01 abril 2025 -
 The Racing Cars of Diaclone and Early G1 – The Source Report01 abril 2025
The Racing Cars of Diaclone and Early G1 – The Source Report01 abril 2025 -
 Anime Transformers Robot Element TE-03 TE Mirage F1 MP G1 Animation Action Figure Assembly Model Collectible Kids Toy Gift01 abril 2025
Anime Transformers Robot Element TE-03 TE Mirage F1 MP G1 Animation Action Figure Assembly Model Collectible Kids Toy Gift01 abril 2025 -
 20mm F1/2 G1/2 Thread 2M Long Stainless Steel Handheld Shower Hose Pipe - Silver Tone - On Sale - Bed Bath & Beyond - 3580865601 abril 2025
20mm F1/2 G1/2 Thread 2M Long Stainless Steel Handheld Shower Hose Pipe - Silver Tone - On Sale - Bed Bath & Beyond - 3580865601 abril 2025 -
 a1, b1, c1, d1, e1, f1, g1, h1, i1, j1, k1, l1, m1, n1 and o1 are some01 abril 2025
a1, b1, c1, d1, e1, f1, g1, h1, i1, j1, k1, l1, m1, n1 and o1 are some01 abril 2025 -
 G1 Wants to Hide F1's Car keys #601 abril 2025
G1 Wants to Hide F1's Car keys #601 abril 2025 -
 Veja imagens do game de corrida 'F1 2014' - fotos em Games - g101 abril 2025
Veja imagens do game de corrida 'F1 2014' - fotos em Games - g101 abril 2025 -
 F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News01 abril 2025
F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News01 abril 2025 -
 Griiip strikes first broadcast deal for disruptive race car series01 abril 2025
Griiip strikes first broadcast deal for disruptive race car series01 abril 2025
você pode gostar
-
 Rumble - OsmarioBros React (2022) : OsmarioBros React : Free Download, Borrow, and Streaming : Internet Archive01 abril 2025
Rumble - OsmarioBros React (2022) : OsmarioBros React : Free Download, Borrow, and Streaming : Internet Archive01 abril 2025 -
 Feno-Grego01 abril 2025
Feno-Grego01 abril 2025 -
initial d anime or manga|TikTok Search01 abril 2025
-
 Free Baby Stuff - Must Have Free Baby Samples (Worth $2,100+!) - The Frugal Navy Wife01 abril 2025
Free Baby Stuff - Must Have Free Baby Samples (Worth $2,100+!) - The Frugal Navy Wife01 abril 2025 -
 Guarda Municipal apreende arsenal em São José dos Pinhais - Bem Paraná01 abril 2025
Guarda Municipal apreende arsenal em São José dos Pinhais - Bem Paraná01 abril 2025 -
 Inazuma Eleven Strikers (2011)01 abril 2025
Inazuma Eleven Strikers (2011)01 abril 2025 -
 AO VIVO, GRÊMIO X CORINTHIANS - CAMPEONATO BRASILEIRO 18° RODADA01 abril 2025
AO VIVO, GRÊMIO X CORINTHIANS - CAMPEONATO BRASILEIRO 18° RODADA01 abril 2025 -
![Cross Ange: Rondo of Angel and Dragon: Collection 2 [Blu-ray]](https://m.media-amazon.com/images/I/91kBsXgsDDL._AC_UF894,1000_QL80_.jpg) Cross Ange: Rondo of Angel and Dragon: Collection 2 [Blu-ray]01 abril 2025
Cross Ange: Rondo of Angel and Dragon: Collection 2 [Blu-ray]01 abril 2025 -
 I Am Reaper Sans01 abril 2025
I Am Reaper Sans01 abril 2025 -
 Soruto Uchiha, Filho de Boruto e Sarada o Ninja mais Poderoso - Boruto01 abril 2025
Soruto Uchiha, Filho de Boruto e Sarada o Ninja mais Poderoso - Boruto01 abril 2025
