Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download
Por um escritor misterioso
Last updated 24 abril 2025
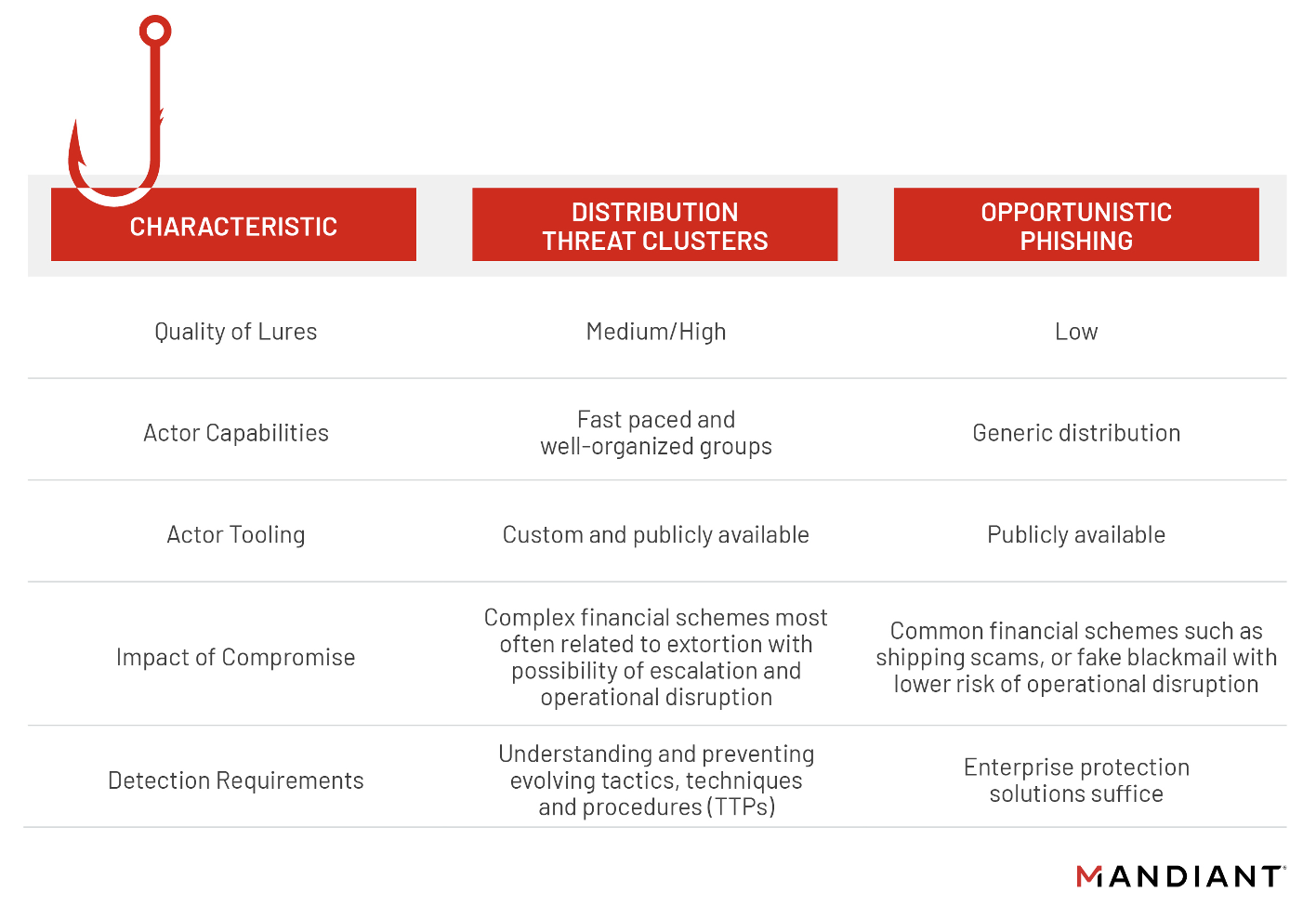
Phishing utilizing social engineering Induces the recipient to reveal desired personal information Bank account SSN Address Etc. Sometimes entices the recipient to go to a malicious web site
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the

What is IP Spoofing? How to Prevent it

PPT - Spam, Phishing & Trojans PowerPoint Presentation, free

Phishing Attacks And Strategies To Mitigate Them Powerpoint

Perfect Domain Name Essay

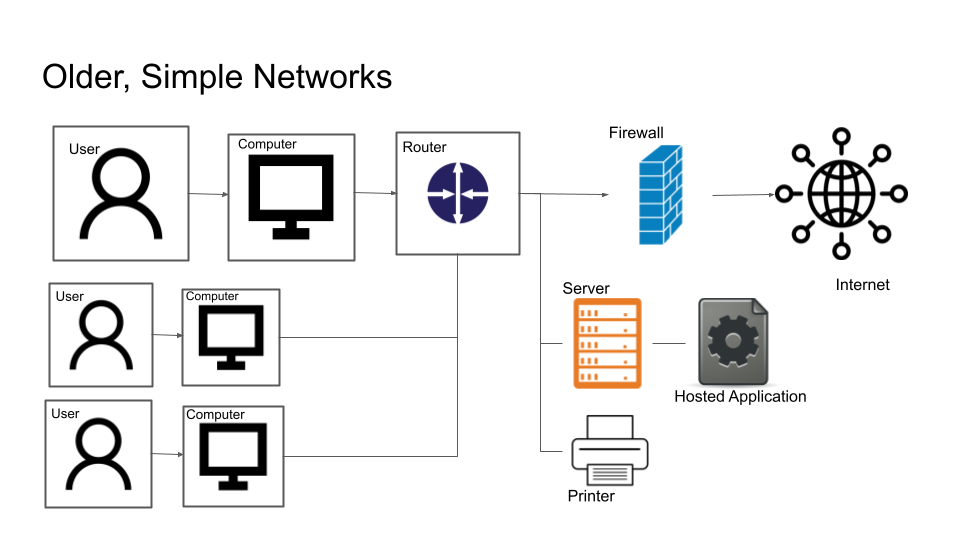
CSC586 Network Forensics IP Tracing/Domain Name Tracing. - ppt
What is Network Security? Definition, Threats & Protections

Email - Wikipedia
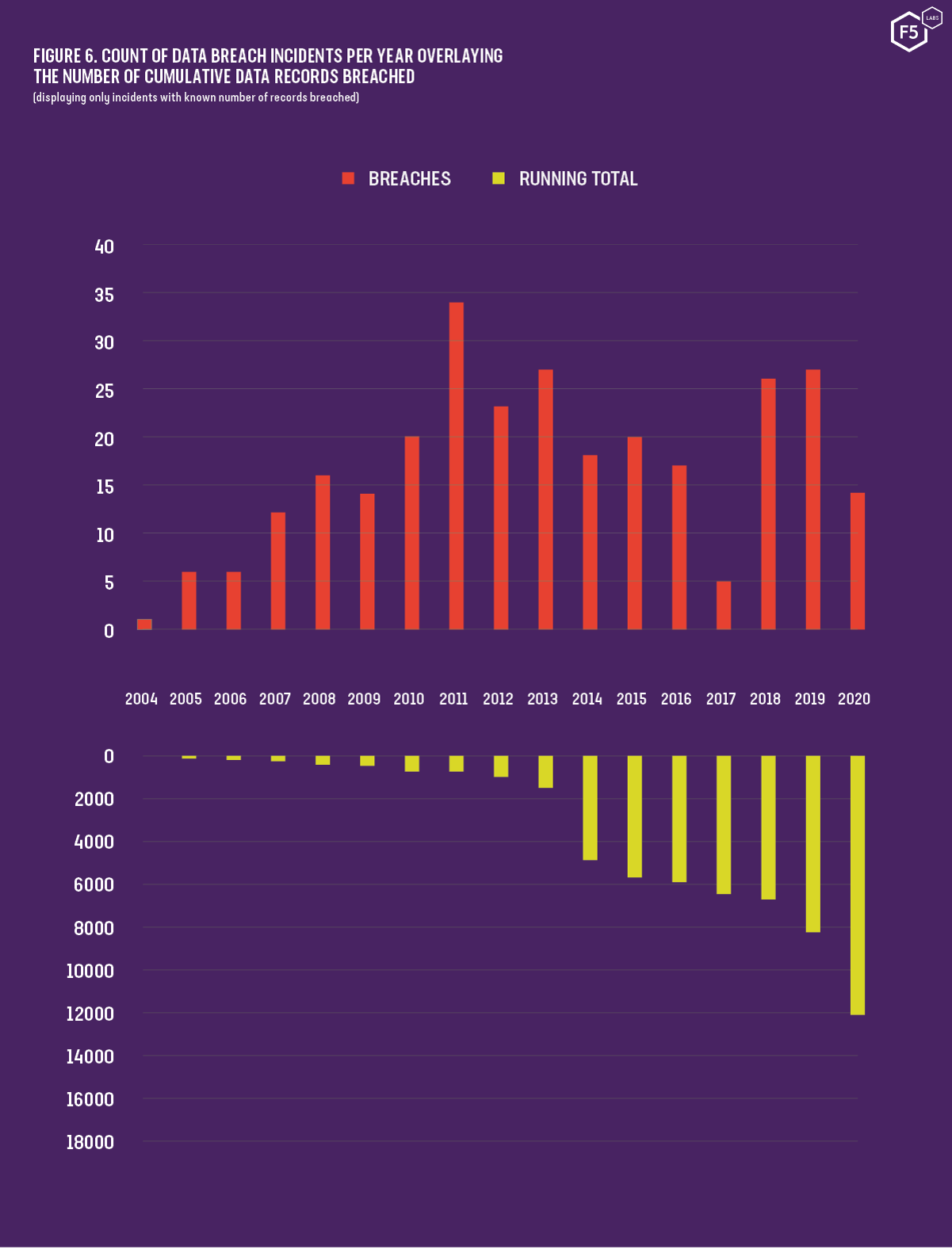
2020 Phishing and Fraud Report
Gone Phishing: Hunting for Malicious Industrial-Themed Emails to

Web Filtering Blog
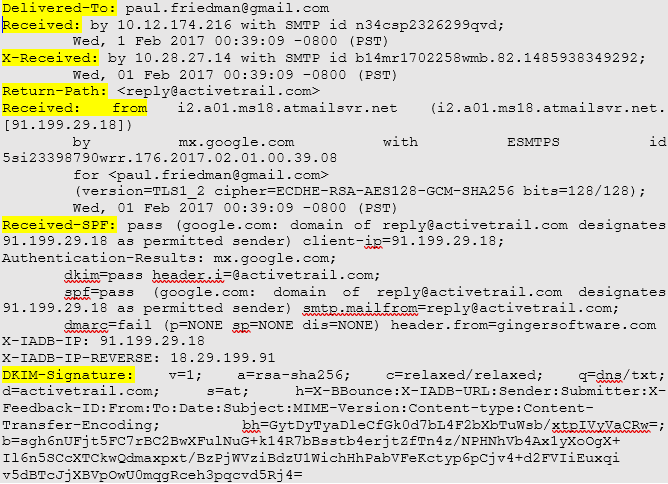
Email Forensics Investigation Techniques- A Complete Guide

Web Filtering Blog

Phishing Attacks And Strategies To Mitigate Them Powerpoint
Recomendado para você
-
 What does your IP address say about you? - CNET24 abril 2025
What does your IP address say about you? - CNET24 abril 2025 -
 Show Your Public IP - Restreamer24 abril 2025
Show Your Public IP - Restreamer24 abril 2025 -
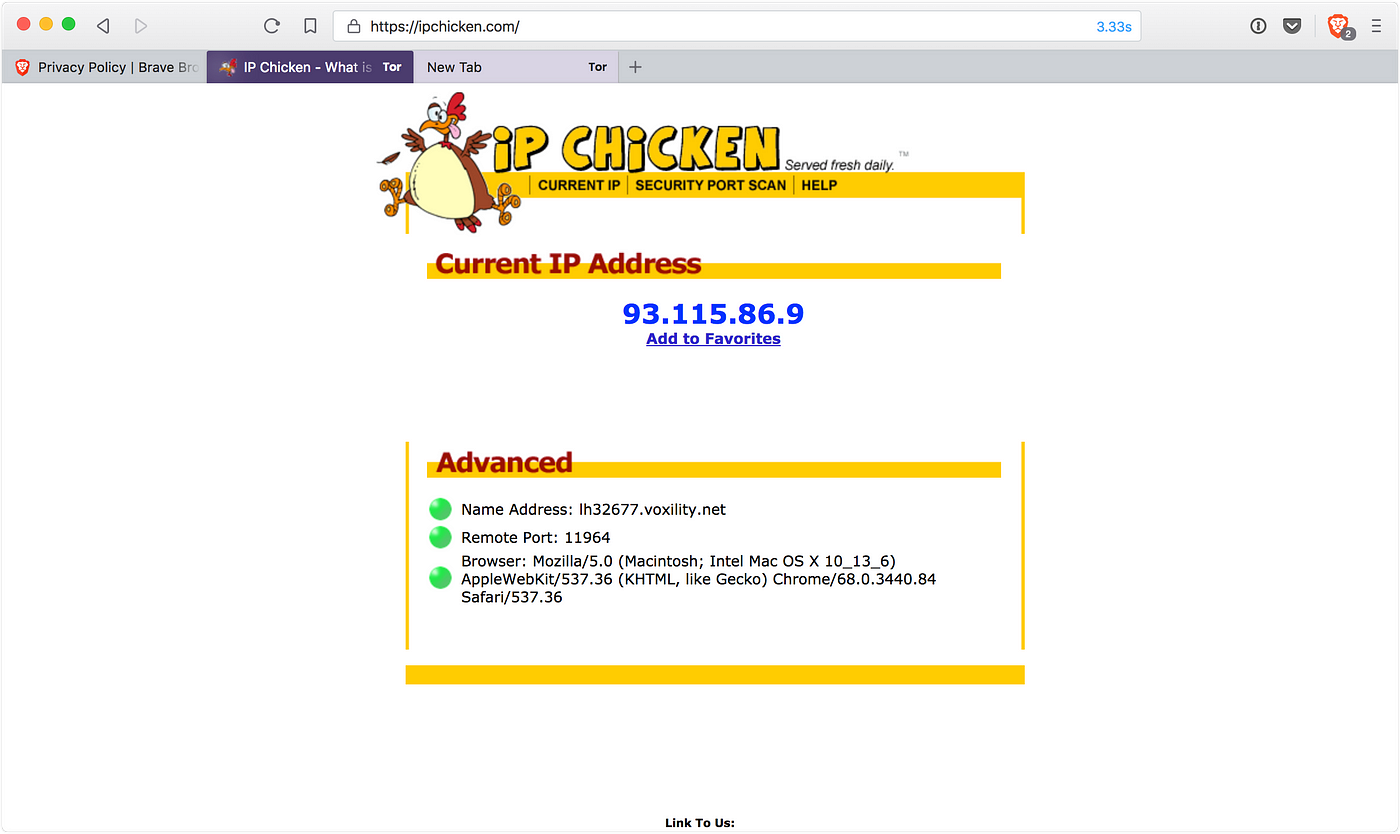 Using a truly private browser — Brave, by Dave Smith24 abril 2025
Using a truly private browser — Brave, by Dave Smith24 abril 2025 -
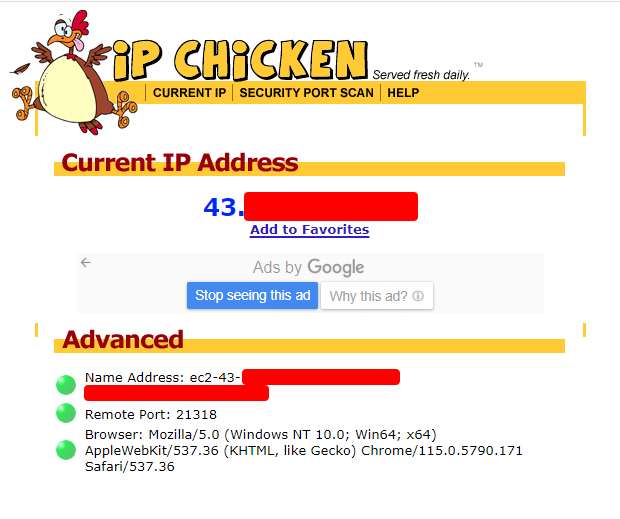 Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K24 abril 2025
Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K24 abril 2025 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community24 abril 2025
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community24 abril 2025 -
 VyprVPN Review - Secure Personal VPN Service Review24 abril 2025
VyprVPN Review - Secure Personal VPN Service Review24 abril 2025 -
 How to Prevent Port Scan Attacks? - GeeksforGeeks24 abril 2025
How to Prevent Port Scan Attacks? - GeeksforGeeks24 abril 2025 -
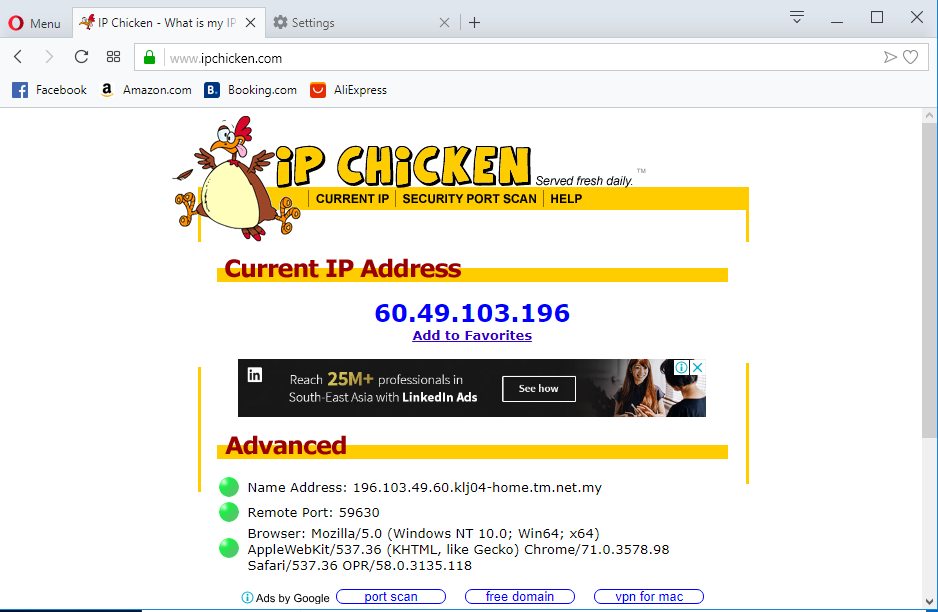 nexuscyberinfo24 abril 2025
nexuscyberinfo24 abril 2025 -
Help Center24 abril 2025
-
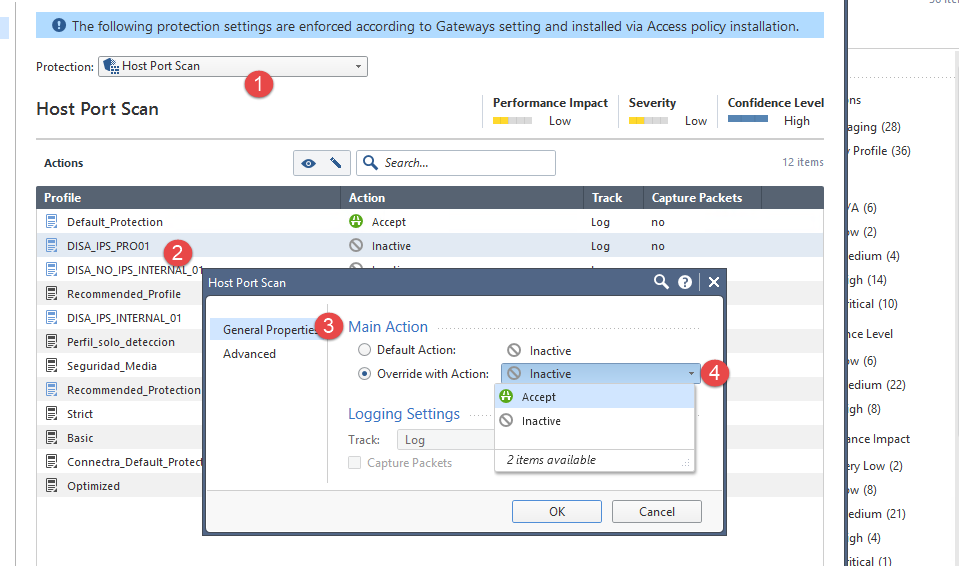 How can I avoid Host Port scan? - Check Point CheckMates24 abril 2025
How can I avoid Host Port scan? - Check Point CheckMates24 abril 2025
você pode gostar
-
 You can now play some PC games on your Xbox, thanks to Nvidia24 abril 2025
You can now play some PC games on your Xbox, thanks to Nvidia24 abril 2025 -
 7 Rhode Island Ice Cream Spots to Hit Up this Summer - Rhode24 abril 2025
7 Rhode Island Ice Cream Spots to Hit Up this Summer - Rhode24 abril 2025 -
JDBC (Oracle) driver exceptions caused by connection timeout kills the tasks · Issue #345 · confluentinc/kafka-connect-jdbc · GitHub24 abril 2025
-
 Moana baby shark azul - festa decoração - BOLA DE NEVE - Kit24 abril 2025
Moana baby shark azul - festa decoração - BOLA DE NEVE - Kit24 abril 2025 -
League of Legends - Lunar Revel 2023 – League of Legends Support24 abril 2025
-
 Granny Smith Apples Bite Size24 abril 2025
Granny Smith Apples Bite Size24 abril 2025 -
 Jogo Pokémon Brilliant Diamond para Nintendo Switch no Paraguai - Atacado Games - Paraguay24 abril 2025
Jogo Pokémon Brilliant Diamond para Nintendo Switch no Paraguai - Atacado Games - Paraguay24 abril 2025 -
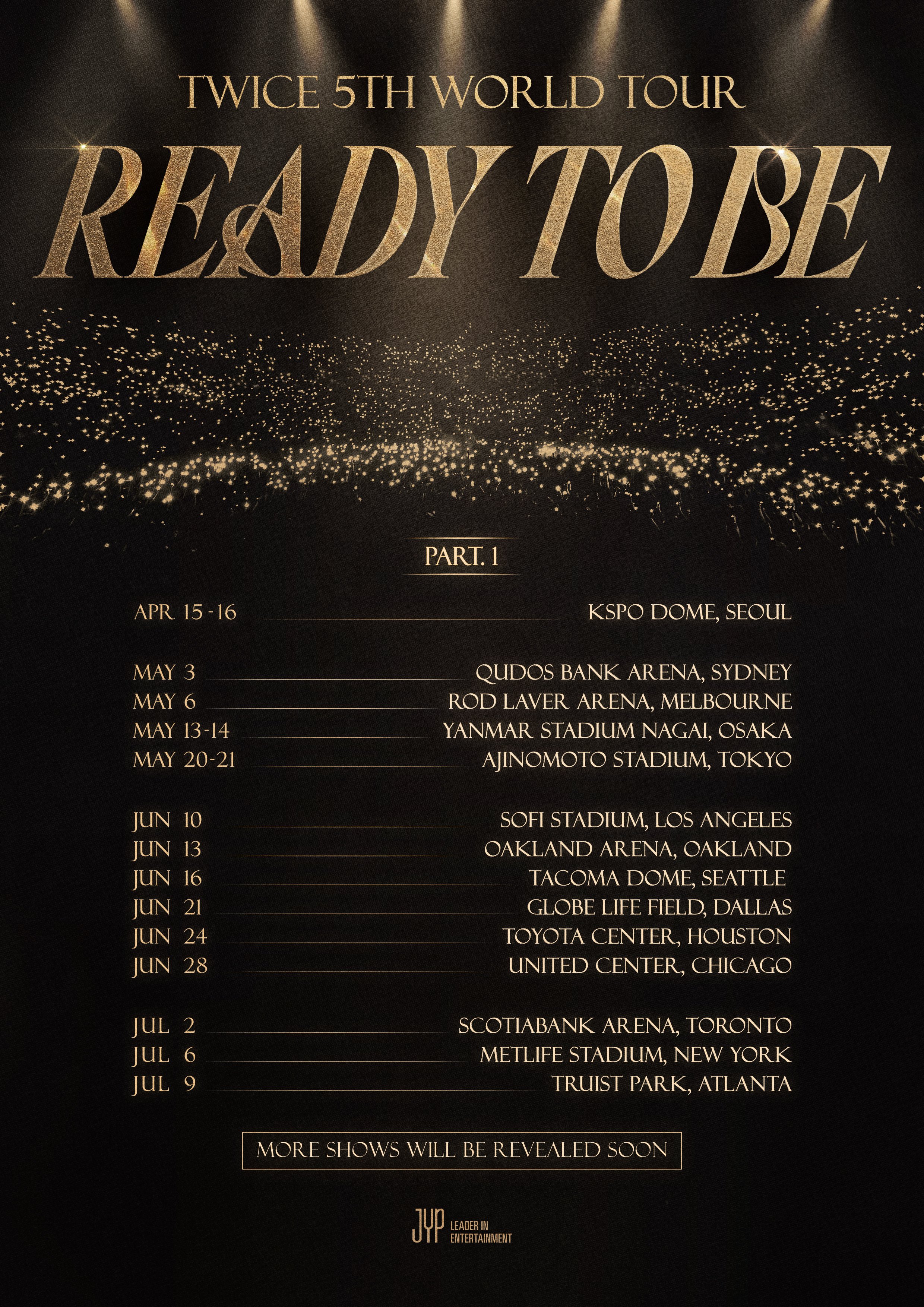
TWICE on X: TWICE 5TH WORLD TOUR READY TO BE 2023 TOUR24 abril 2025
-
 Nico Robin, Wiki24 abril 2025
Nico Robin, Wiki24 abril 2025 -
 coleção de monstros engraçados redondos coloridos. marrom, verde24 abril 2025
coleção de monstros engraçados redondos coloridos. marrom, verde24 abril 2025