Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 29 março 2025

Describing activities of a crime group attacking Ukraine.

Security in product lifecycle of IoT devices: A survey - ScienceDirect

So long and thanks for all the 0day, NCC Group Research Blog

⚖️ LWIL #25: Copyright Claims Board, Algorithm Lawsuits, Location Data Rules and More

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

You could be hacked and not know it - Storcom, Lombard, Illinois, United States of America
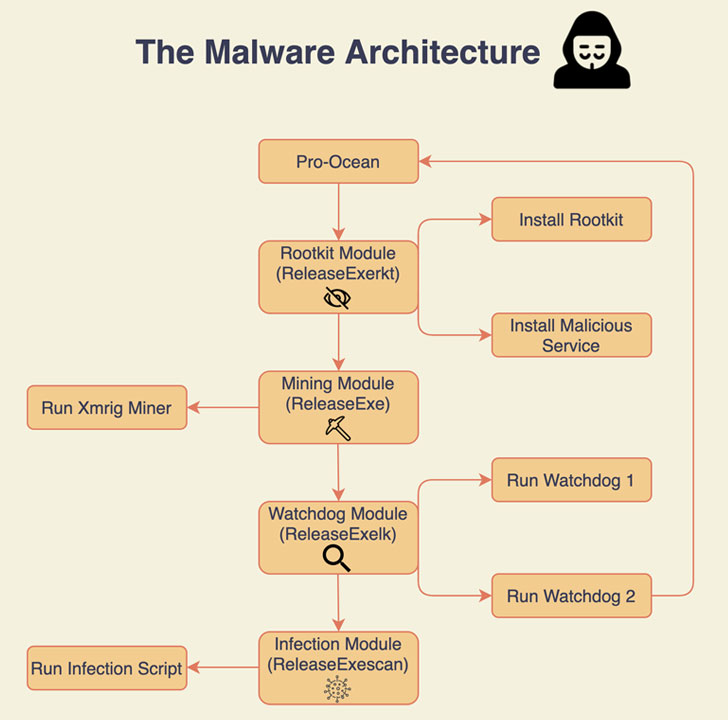
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database

US7236486B2 - Integrated customer web station for web based call management - Google Patents

Initial Access Brokers - who are they, what do they do, and how can you protect yourself?
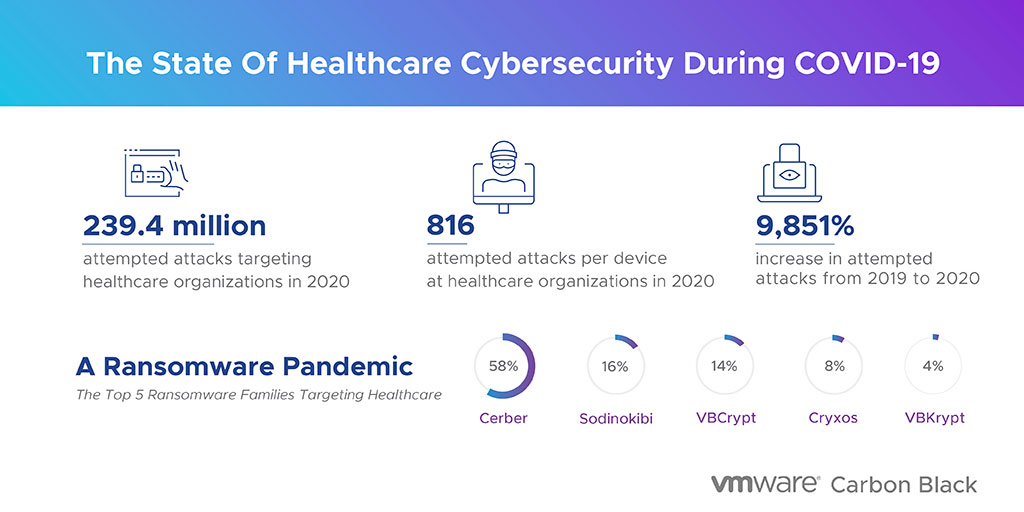
The State of Healthcare Cybersecurity: VMware Carbon Black Explores the Surge in Cyber Threats - REAL security

US20080120240A1 - Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management - Google Patents

PDF) Money Over Morals: A Business Analysis of Conti Ransomware

Target and solution of DoS attacks (source: authors' work)

Initial Access Brokers - who are they, what do they do, and how can you protect yourself?

Transfer Learning: Repurposing ML Algorithms from Different Domains to Cloud Defense
Recomendado para você
-
Analysis Group29 março 2025
-
 Analysis Group Boston29 março 2025
Analysis Group Boston29 março 2025 -
 Q&A: For Bates interns, there's 'no better outlet' for economics29 março 2025
Q&A: For Bates interns, there's 'no better outlet' for economics29 março 2025 -
 Careers - Analysis Group29 março 2025
Careers - Analysis Group29 março 2025 -
Analysis Group HealthEconomics.com Jobs Portal29 março 2025
-
IAG, Image Analysis Group29 março 2025
-
 Annual Meeting of the Lunar Exploration Analysis Group29 março 2025
Annual Meeting of the Lunar Exploration Analysis Group29 março 2025 -
 Analysis Group's CEO on Managing with Soft Metrics29 março 2025
Analysis Group's CEO on Managing with Soft Metrics29 março 2025 -
 Our People - Analysis Group29 março 2025
Our People - Analysis Group29 março 2025 -
 Groupe d'analyse – Montréal - Analysis Group29 março 2025
Groupe d'analyse – Montréal - Analysis Group29 março 2025
você pode gostar
-
 JoJo's Bizarre Adventure: Part 3--Stardust Crusaders, Vol. 1 (1)29 março 2025
JoJo's Bizarre Adventure: Part 3--Stardust Crusaders, Vol. 1 (1)29 março 2025 -
 HINATA SHOYO Drawing Illustration Leisure ver. Postcard Haikyu29 março 2025
HINATA SHOYO Drawing Illustration Leisure ver. Postcard Haikyu29 março 2025 -
 Xereta 2 em 1 - Cadê o bicho? / Cadê o objeto?29 março 2025
Xereta 2 em 1 - Cadê o bicho? / Cadê o objeto?29 março 2025 -
Rentsux29 março 2025
-
 Aliança de Casamento Abaulada Tracional 5mm Ouro 18k - Monterrey Joias e Alianças29 março 2025
Aliança de Casamento Abaulada Tracional 5mm Ouro 18k - Monterrey Joias e Alianças29 março 2025 -
 Shalon Israel - Cabeça de Gelo (Ao Vivo em Teresina-Pi no29 março 2025
Shalon Israel - Cabeça de Gelo (Ao Vivo em Teresina-Pi no29 março 2025 -
 Klobrille on X: Power Your Dreams. With 16 announced and yet to29 março 2025
Klobrille on X: Power Your Dreams. With 16 announced and yet to29 março 2025 -
 Nintendo Switch - Pokémon Brilliant Diamond / Shining Pearl29 março 2025
Nintendo Switch - Pokémon Brilliant Diamond / Shining Pearl29 março 2025 -
 Baixe Guide for God Of War 3 Ghost Of Sparta no PC29 março 2025
Baixe Guide for God Of War 3 Ghost Of Sparta no PC29 março 2025 -
 Guia Completo da Estampa Xadrez: quais são as opções e como usar29 março 2025
Guia Completo da Estampa Xadrez: quais são as opções e como usar29 março 2025


