Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 02 abril 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

7 powerful pentesting tools (& why you should stop pedestalizing them)

Linux Challenges - Cyber Security / Ethical Hacking

Live Linux Hacking Login Bypass and Privilege Escalation & Q & A Session - WsCube Tech

Postman Hack The Box (HTB). Hello guys today Postman got retired by…, by Musyoka Ian

Playing with FHIR? Don't get burned, white-hat hacker cautions
Ethical Hacking - Quick Guide

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS

Hack The Box - Monitors Walkthrough - Steflan's Security Blog

Connecting All the World's Users in an Open Way: Decentralized Authentication with Brooklyn Zelenka
Recomendado para você
-
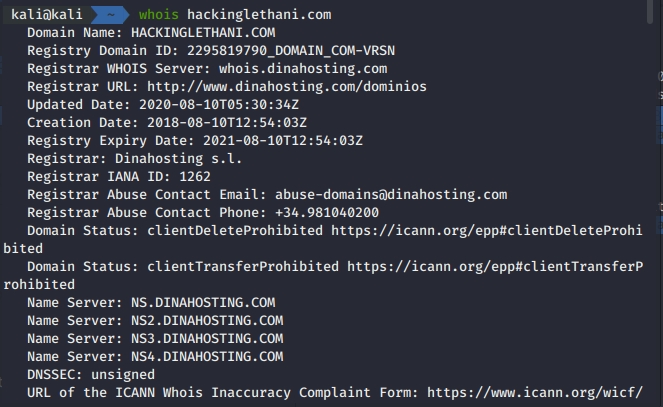
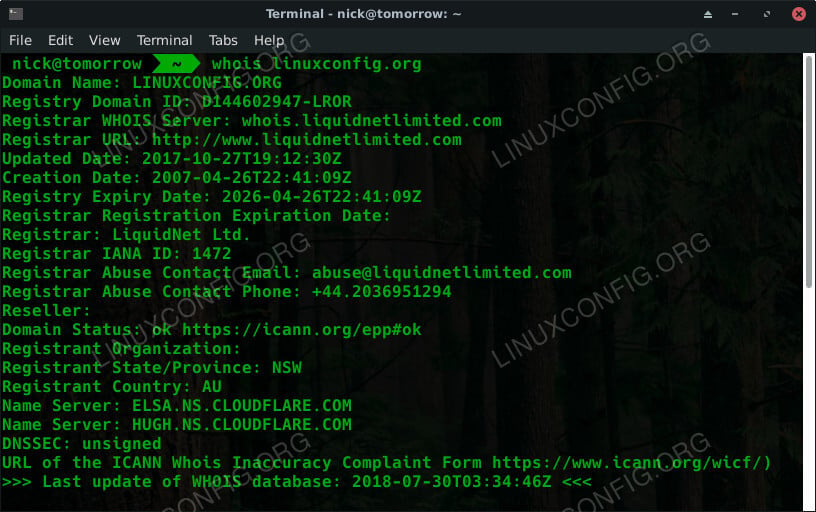 Look Up Website Information With Whois in Linux - Linux Tutorials02 abril 2025
Look Up Website Information With Whois in Linux - Linux Tutorials02 abril 2025 -
 What Is Whois Lookup And How Can It Help You? - Monsterhost02 abril 2025
What Is Whois Lookup And How Can It Help You? - Monsterhost02 abril 2025 -
 WHOIS - Wikipedia02 abril 2025
WHOIS - Wikipedia02 abril 2025 -
 WHOIS Email, Email Address WHOIS02 abril 2025
WHOIS Email, Email Address WHOIS02 abril 2025 -
 macos - WHOIS in Mac OS terminal not doing anything - Stack Overflow02 abril 2025
macos - WHOIS in Mac OS terminal not doing anything - Stack Overflow02 abril 2025 -
 Whois Lookup: How to Check Domain Availability & Expiry Date02 abril 2025
Whois Lookup: How to Check Domain Availability & Expiry Date02 abril 2025 -
 Check domain name availability with bash and whois - Linux02 abril 2025
Check domain name availability with bash and whois - Linux02 abril 2025 -
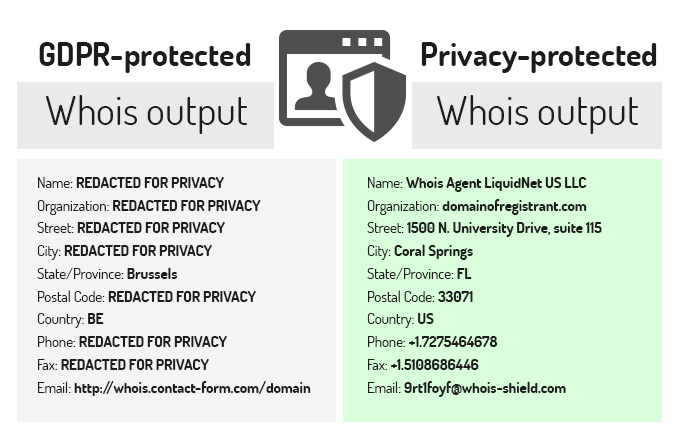 Privacy Protected vs GDPR Protected Whois - the key differences02 abril 2025
Privacy Protected vs GDPR Protected Whois - the key differences02 abril 2025 -
 Prefix WhoIs - Wikipedia02 abril 2025
Prefix WhoIs - Wikipedia02 abril 2025 -
WhoIs - Apps on Google Play02 abril 2025
você pode gostar
-
 Legging 3D Vertical Alta Compressão Preta c/ Rosa bb02 abril 2025
Legging 3D Vertical Alta Compressão Preta c/ Rosa bb02 abril 2025 -
 Characters appearing in The Devil is a Part-Timer! Anime02 abril 2025
Characters appearing in The Devil is a Part-Timer! Anime02 abril 2025 -
 Verstappen: Miami weekend is going to be pretty crazy02 abril 2025
Verstappen: Miami weekend is going to be pretty crazy02 abril 2025 -
 Battlefield 2042 Open Beta pre-load begins, 19GB download on the PC02 abril 2025
Battlefield 2042 Open Beta pre-load begins, 19GB download on the PC02 abril 2025 -
 FIFA 2025 Club World Cup dates: Which teams have qualified?02 abril 2025
FIFA 2025 Club World Cup dates: Which teams have qualified?02 abril 2025 -
 You can now play Silent Hill 4 on GOG02 abril 2025
You can now play Silent Hill 4 on GOG02 abril 2025 -
Soft Enterprise02 abril 2025
-
 Ao Ashi Fire Ball alas Explocion - Anime And Manga - Pin02 abril 2025
Ao Ashi Fire Ball alas Explocion - Anime And Manga - Pin02 abril 2025 -
sasukeuchiha #sasuke #uchihasasuke02 abril 2025
-
 ITT games you need to play if you own a computer, Wise Mystical Tree / If You're Over 25 and Own a Computer, This Game Is a Must-Have02 abril 2025
ITT games you need to play if you own a computer, Wise Mystical Tree / If You're Over 25 and Own a Computer, This Game Is a Must-Have02 abril 2025

