Validating User Flows to Protect Software Defined Network Environments
Por um escritor misterioso
Last updated 31 março 2025

Software Defined Network is a promising network paradigm which has led to several security threats in SDN applications that involve user flows, switches, and controllers in the network. Threats as spoofing, tampering, information disclosure, Denial of Service, flow table overloading, and so on have been addressed by many researchers. In this paper, we present novel SDN design to solve three security threats: flow table overloading is solved by constructing a star topology-based architecture, unsupervised hashing method mitigates link spoofing attack, and fuzzy classifier combined with L1-ELM running on a neural network for isolating anomaly packets from normal packets. For effective flow migration Discrete-Time Finite-State Markov Chain model is applied. Extensive simulations using OMNeT++ demonstrate the performance of our proposed approach, which is better at preserving holding time than are other state-of-the-art works from the literature.

Validating User Flows to Protect Software Defined Network Environments
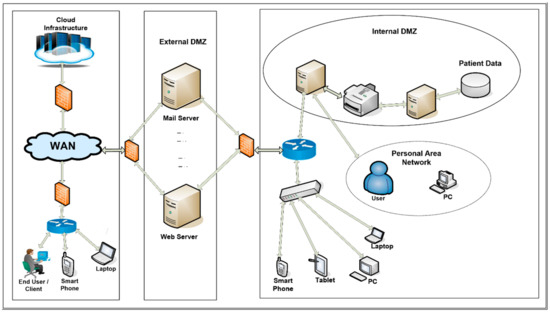
Applied Sciences, Free Full-Text
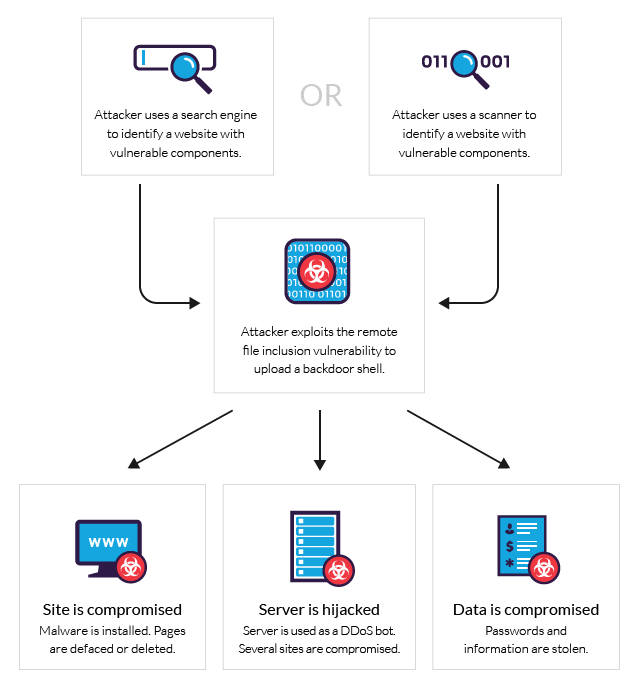
What is RFI Remote File Inclusion Example & Mitigation Methods
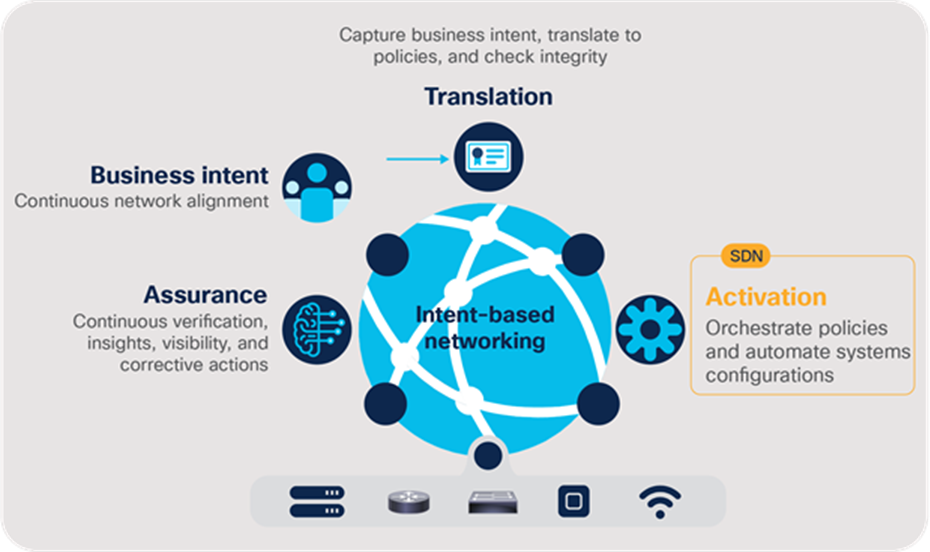
Cisco Group-Based Policies for Zero-Trust Security White Paper - Cisco

Software defined wireless sensor networks application

Cisco Secure Network Access Whitepaper - Cisco

Validating User Flows to Protect Software Defined Network Environments
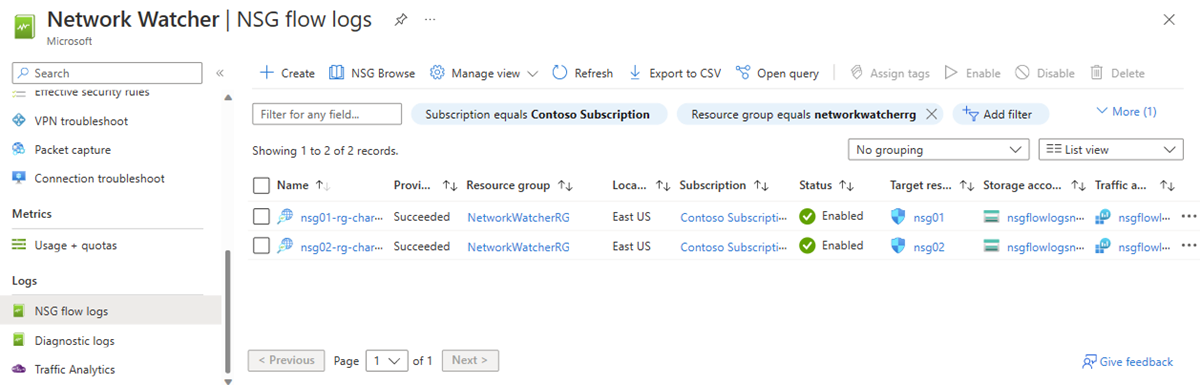
NSG flow logs overview - Azure Network Watcher
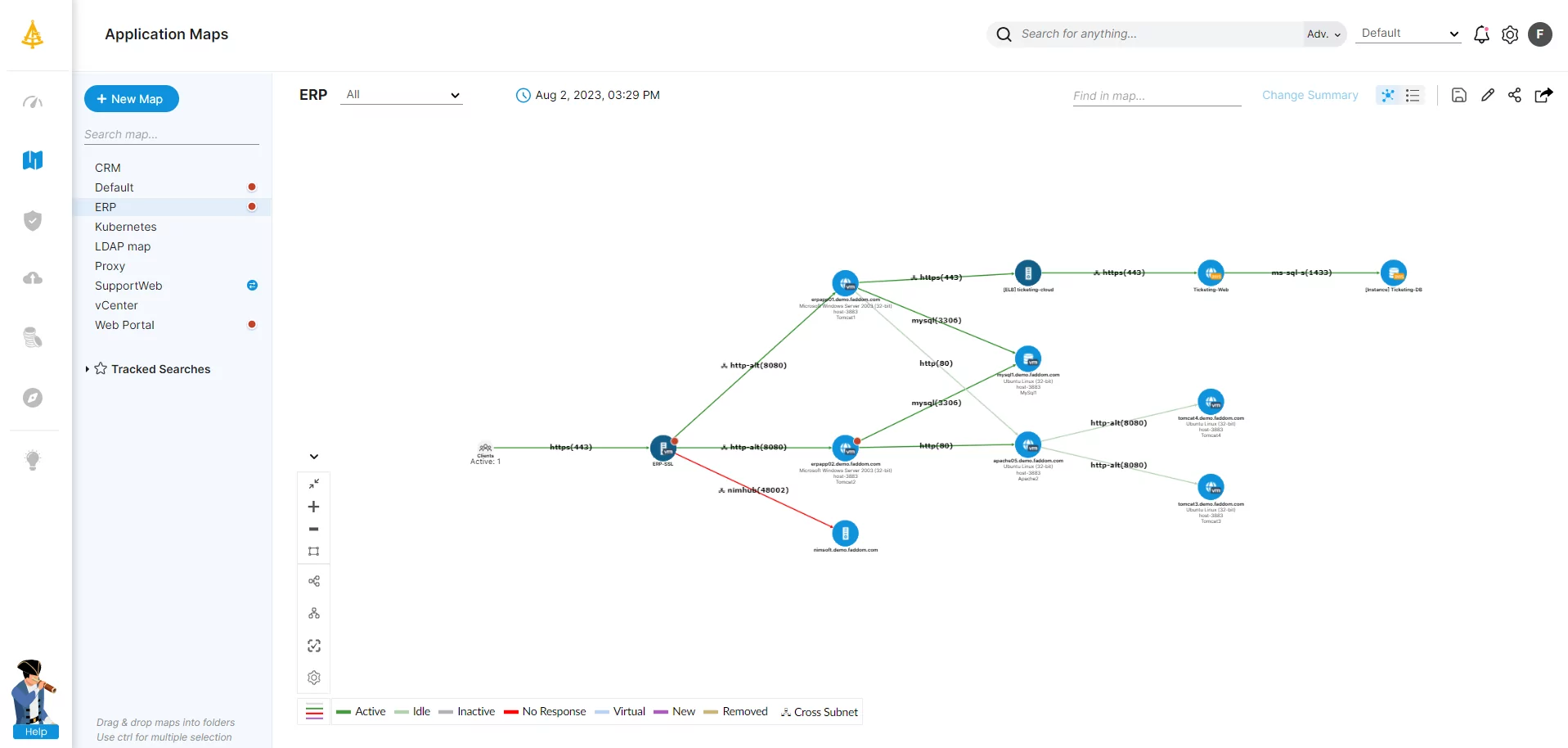
Application Dependency Mapping: The Complete Guide
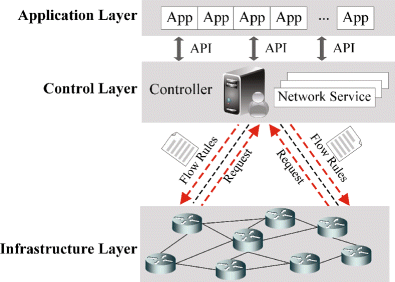
PERM-GUARD: Authenticating the Validity of Flow Rules in Software
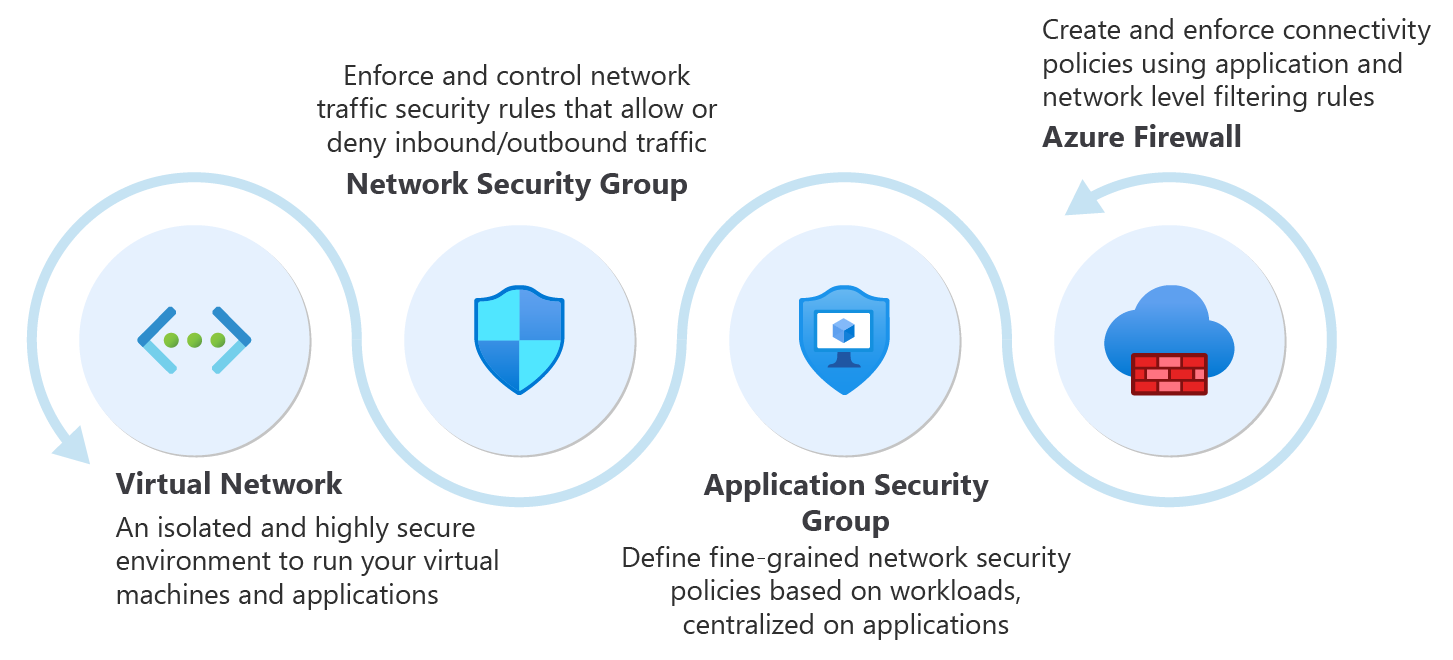
Recommendations for building a segmentation strategy - Microsoft

Validating User Flows to Protect Software Defined Network Environments
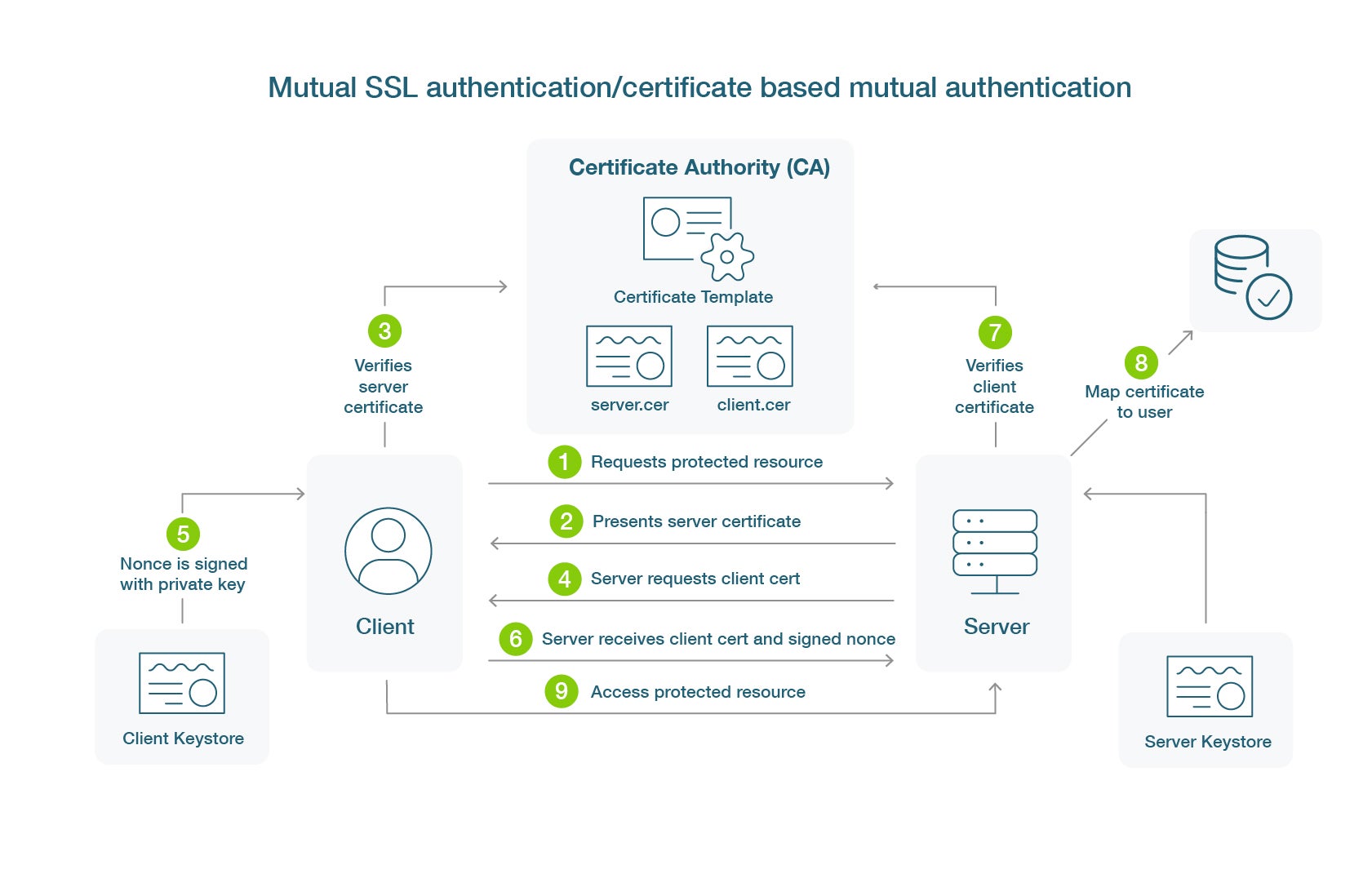
What is Certificate-Based Authentication - Yubico
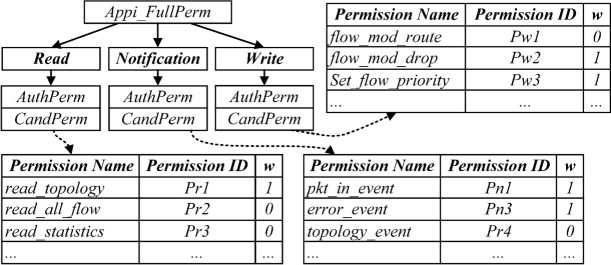
PERM-GUARD: Authenticating the Validity of Flow Rules in Software

Validating User Flows to Protect Software Defined Network Environments
Recomendado para você
-
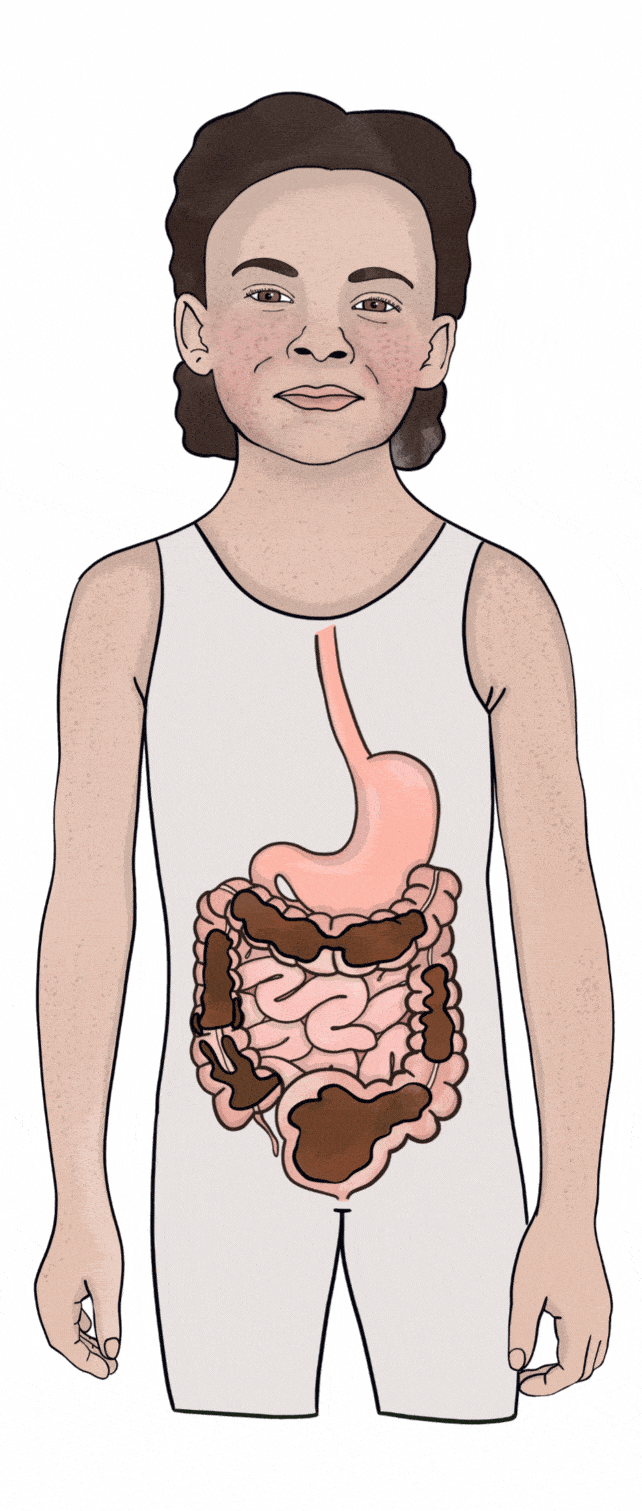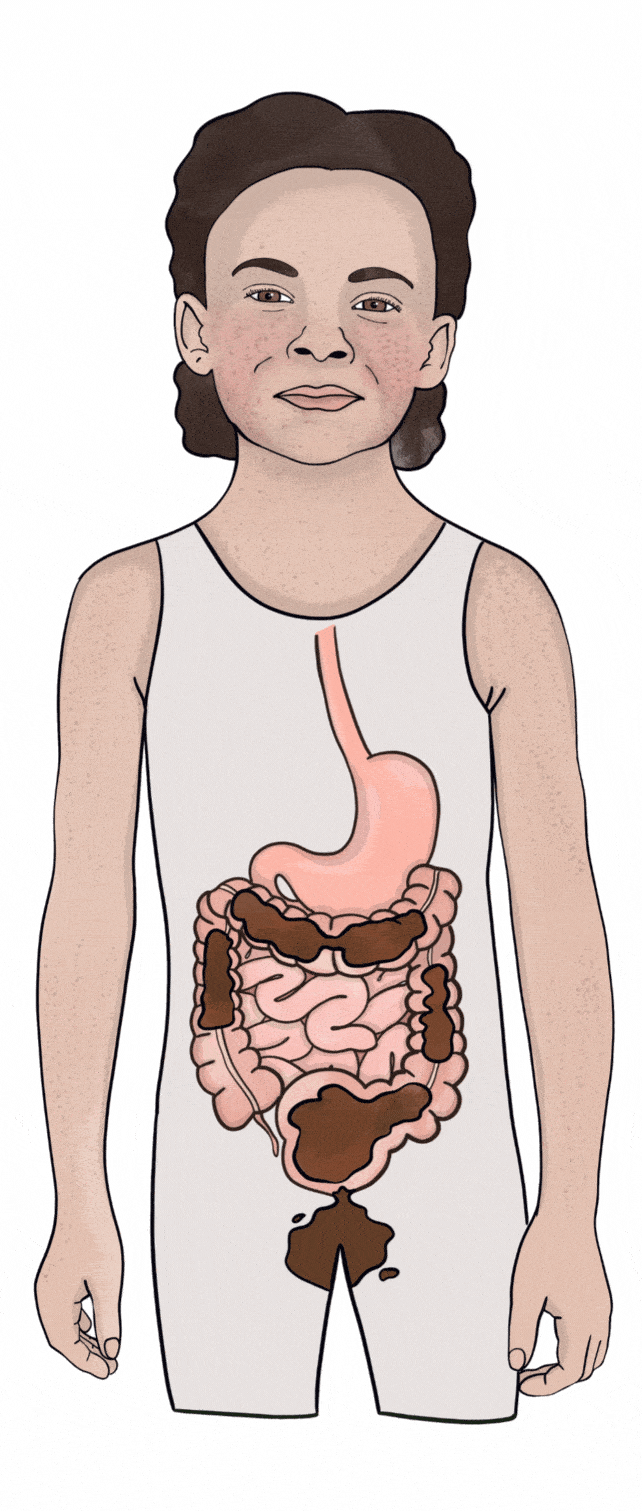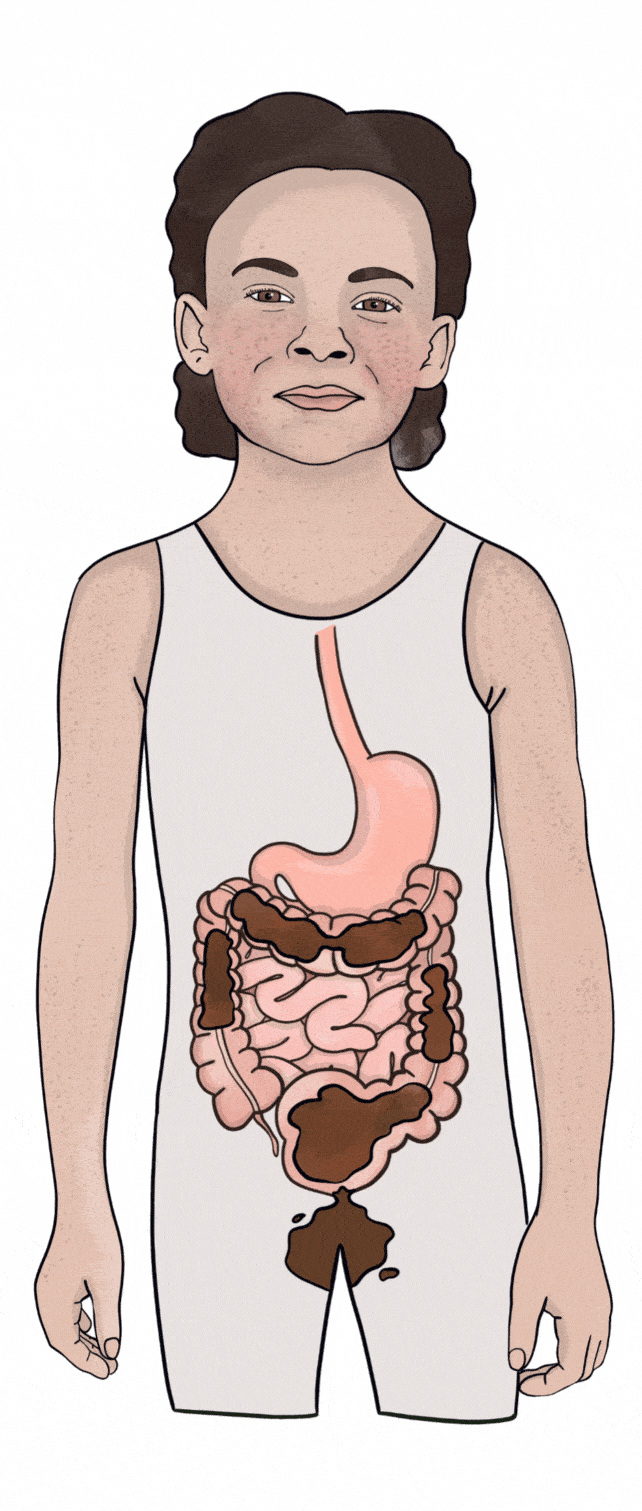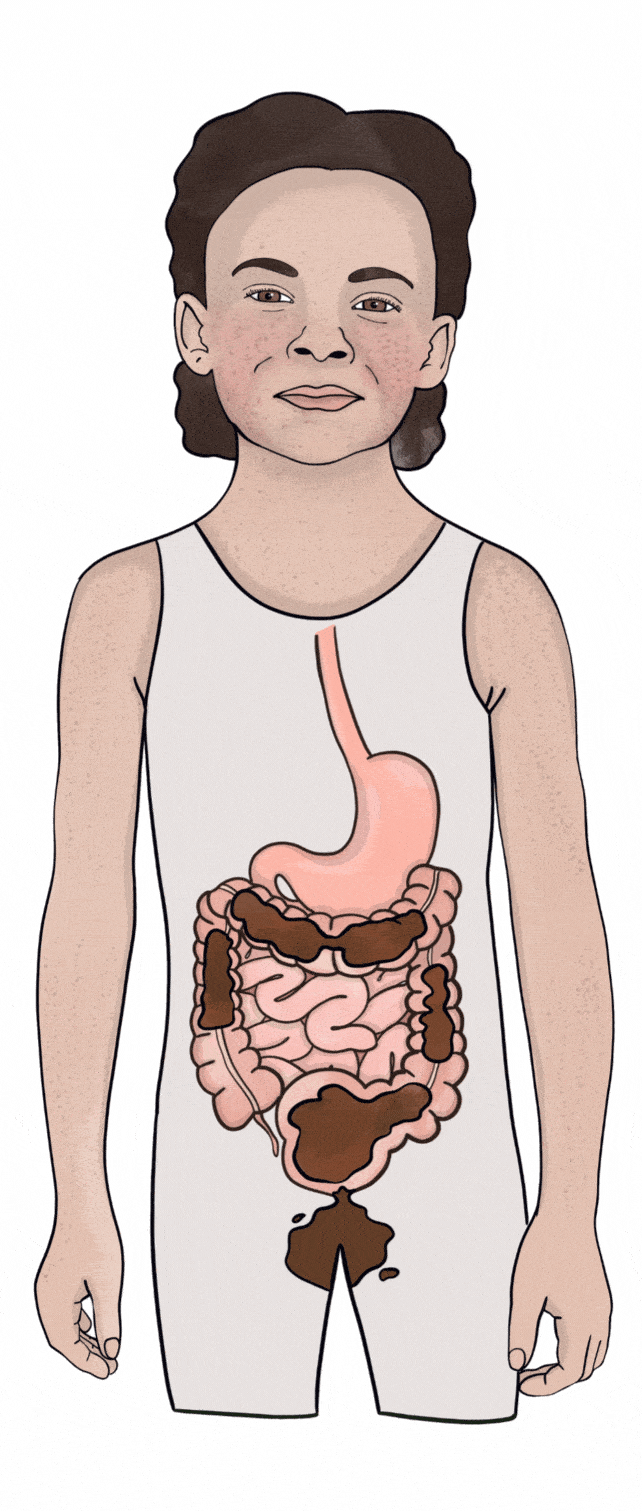 Soiling KidsHealth NZ31 março 2025
Soiling KidsHealth NZ31 março 2025 -
 POO - 18 - Sobrecarga e Sobreposição de Métodos31 março 2025
POO - 18 - Sobrecarga e Sobreposição de Métodos31 março 2025 -
 Overload de métodos - POO - s02e1231 março 2025
Overload de métodos - POO - s02e1231 março 2025 -
GitHub - evil-mad/politicians-to-poop: Chrome extension that replaces names of politicians with the poop emoji.31 março 2025
-
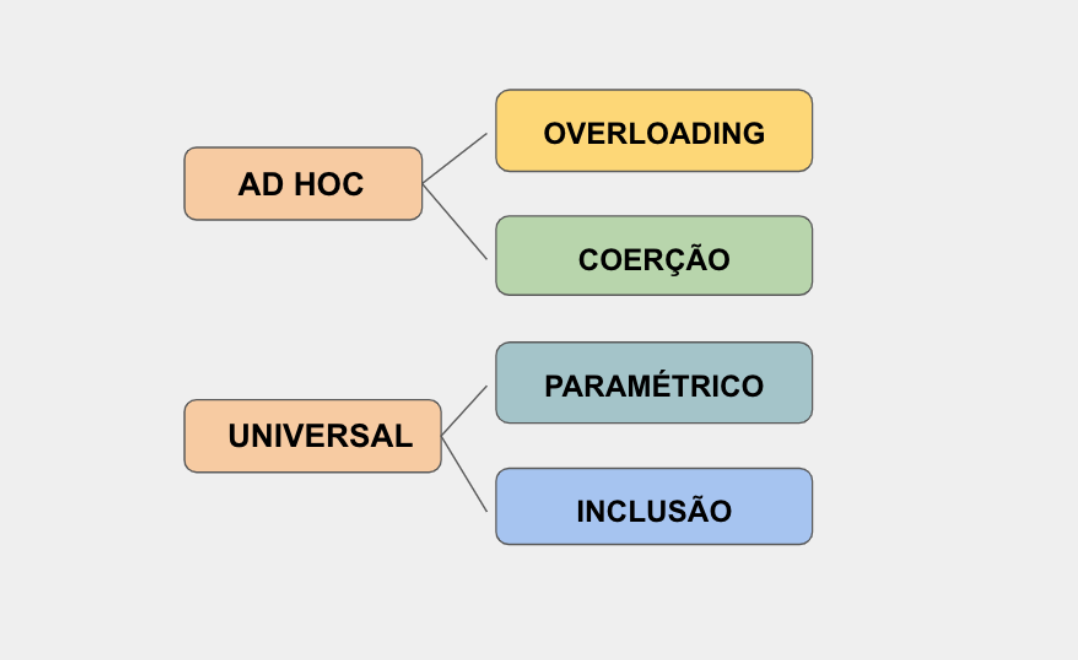 POLIMORFISMO, O ULTIMATO!. Olá! Esse é o primeiro de muitos…, by Verônica Rocha31 março 2025
POLIMORFISMO, O ULTIMATO!. Olá! Esse é o primeiro de muitos…, by Verônica Rocha31 março 2025 -
To Get To The Bottom Of Your Microbiome, Start With A Swab Of Poo, NPR Article31 março 2025
-
 Dog Poop Color Chart, What's Normal?31 março 2025
Dog Poop Color Chart, What's Normal?31 março 2025 -
Loose yellow poos and white speckles31 março 2025
-
 Dutch Truffle Overloaded Cake With Macaroons (Eggless) - Ovenfresh31 março 2025
Dutch Truffle Overloaded Cake With Macaroons (Eggless) - Ovenfresh31 março 2025 -
 Cartões: Orientação a Objetos31 março 2025
Cartões: Orientação a Objetos31 março 2025
você pode gostar
-
 Anvil of the Void (Assault, III) - Dragon Age Guide - IGN31 março 2025
Anvil of the Void (Assault, III) - Dragon Age Guide - IGN31 março 2025 -
 Descubren cómo conseguir Pokémon Shiny infinitos en Escarlata y Púrpura - Nintenderos31 março 2025
Descubren cómo conseguir Pokémon Shiny infinitos en Escarlata y Púrpura - Nintenderos31 março 2025 -
 Free 3d character animations from MoCap animated gif31 março 2025
Free 3d character animations from MoCap animated gif31 março 2025 -
 Apple Shooter Play Now Online for Free31 março 2025
Apple Shooter Play Now Online for Free31 março 2025 -
 80 fun questions to ask your friends to get to know them on a deeper level31 março 2025
80 fun questions to ask your friends to get to know them on a deeper level31 março 2025 -
 Aprenda como SOBREVIVER em uma ilha deserta → Survival Master 3D 📱🎮31 março 2025
Aprenda como SOBREVIVER em uma ilha deserta → Survival Master 3D 📱🎮31 março 2025 -
![Análise] Dragon Ball Z: Kakarot: Vale a Pena?](https://meups.com.br/wp-content/uploads/2020/01/Dragon-Ball-Z-Kakarot.jpg) Análise] Dragon Ball Z: Kakarot: Vale a Pena?31 março 2025
Análise] Dragon Ball Z: Kakarot: Vale a Pena?31 março 2025 -
 Rebuilding and Connecting31 março 2025
Rebuilding and Connecting31 março 2025 -
 Bola de cristal: qual origem?31 março 2025
Bola de cristal: qual origem?31 março 2025 -
 Free Online Games to Play with Friends on Phone 202331 março 2025
Free Online Games to Play with Friends on Phone 202331 março 2025
