Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 20 março 2025

4 of the Biggest Vulnerabilities Talked About During Black Hat 2023
Cloaked Ursa (APT29) Hackers Use Trusted Online Storage Services
How to report misrated websites to Trend Micro

Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer
How to adjust Trend Micro scan settings on Windows
Known issues - Licensing Management Platform
Common questions about Hosted Email Security
How to report misrated websites to Trend Micro

RADIUS Server Authentication: Explained

Connected Philanthropy Podcast - Foundant Technologies
Trend Micro Internet Security Data Collection Notice
Trend Micro AntiVirus+ Security Data Collection Notice
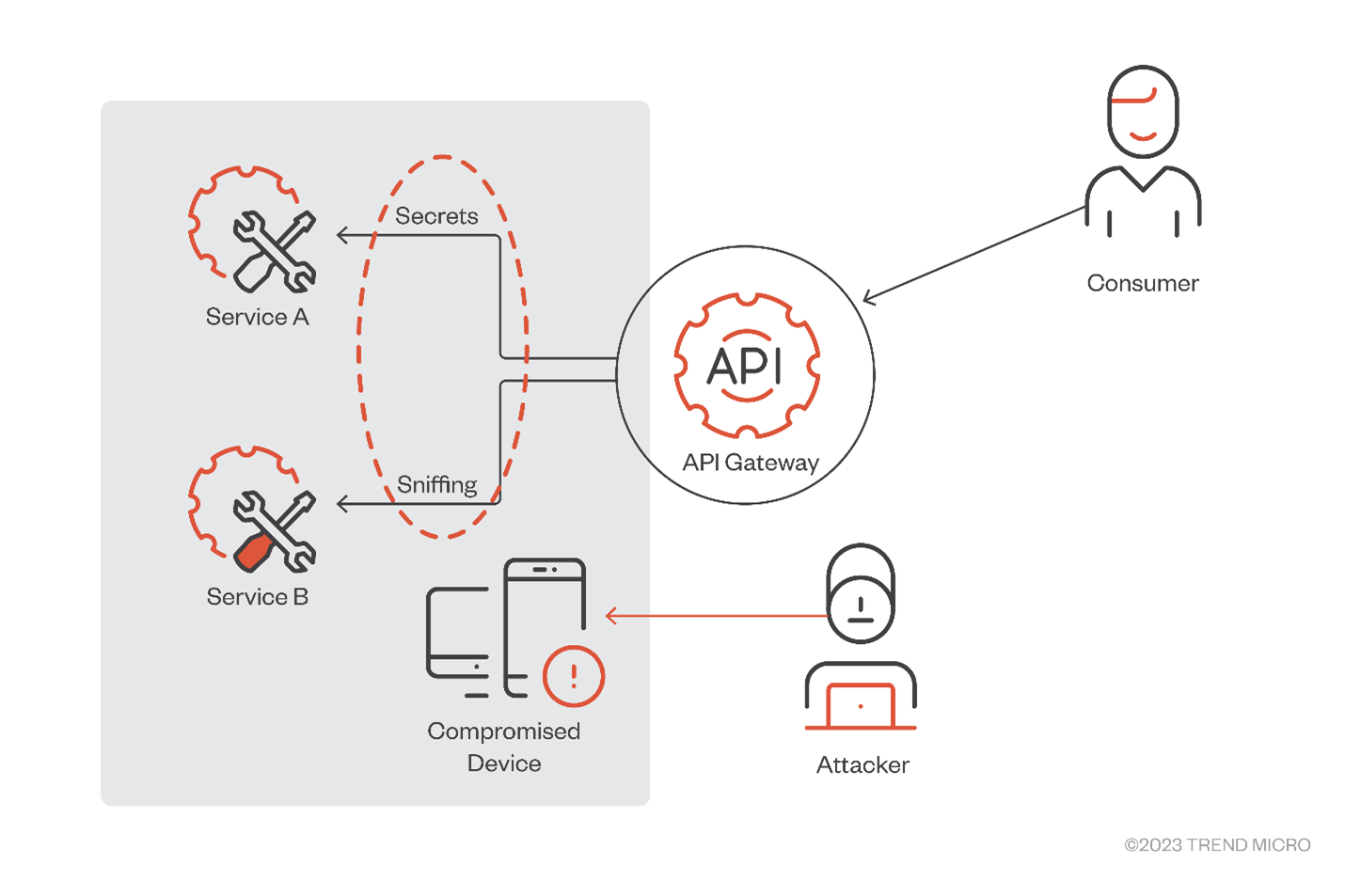
Threat Modeling API Gateways: A New Target for Threat Actors? - Noticias de seguridad - Trend Micro ES
Ransomware - Definition
Recomendado para você
-
Is it possible to get past login history report on Facebook? - Quora20 março 2025
-
 Facebook Login20 março 2025
Facebook Login20 março 2025 -
 Facebook Login Home Page Screen Editorial Stock Photo20 março 2025
Facebook Login Home Page Screen Editorial Stock Photo20 março 2025 -
 Configure Facebook Login on Your Website & Mobile App in 202020 março 2025
Configure Facebook Login on Your Website & Mobile App in 202020 março 2025 -
 Implement Facebook Login with PHP20 março 2025
Implement Facebook Login with PHP20 março 2025 -
 OAuth: How Does 'Login With Facebook/Google' Work? » Science ABC20 março 2025
OAuth: How Does 'Login With Facebook/Google' Work? » Science ABC20 março 2025 -
 How to Integrate Facebook Login with WordPress20 março 2025
How to Integrate Facebook Login with WordPress20 março 2025 -
 facebook login page20 março 2025
facebook login page20 março 2025 -
 Inspiration Login and Signup by Facebook - UI Garage20 março 2025
Inspiration Login and Signup by Facebook - UI Garage20 março 2025 -
 Facebook, social network, homepage with login mask, logo, internet20 março 2025
Facebook, social network, homepage with login mask, logo, internet20 março 2025
você pode gostar
-
 Garfo Grande Inox 33cm Fratelli R-586420 março 2025
Garfo Grande Inox 33cm Fratelli R-586420 março 2025 -
 Twitter reacts to Cheddar Man's dark skin and blue eyes - BBC News20 março 2025
Twitter reacts to Cheddar Man's dark skin and blue eyes - BBC News20 março 2025 -
 Tic Tac Toe Online Game for Kids Online Tic Tac Toe - EasyShiksha20 março 2025
Tic Tac Toe Online Game for Kids Online Tic Tac Toe - EasyShiksha20 março 2025 -
Steam Workshop::A Place Further Than The Universe20 março 2025
-
 EA SPORTS FC 24 Ultimate Team new features: Women's football, PlayStyles, upgradeable cards - Dexerto20 março 2025
EA SPORTS FC 24 Ultimate Team new features: Women's football, PlayStyles, upgradeable cards - Dexerto20 março 2025 -
Queen - Another One Bites The Dust Sheets20 março 2025
-
 Canon EOS R6 (no lens included) 20.1-megapixel full-frame mirrorless camera with Wi-Fi® and Bluetooth® at Crutchfield20 março 2025
Canon EOS R6 (no lens included) 20.1-megapixel full-frame mirrorless camera with Wi-Fi® and Bluetooth® at Crutchfield20 março 2025 -
 I was invisible in subway surfers!20 março 2025
I was invisible in subway surfers!20 março 2025 -
 MAKING ENTITIES of DOORS more CREPPY & REALISTIC!! (Figure, Dupe and Rush) Clay20 março 2025
MAKING ENTITIES of DOORS more CREPPY & REALISTIC!! (Figure, Dupe and Rush) Clay20 março 2025 -
 Fé, sal grosso e memes: como os torcedores do Palmeiras aguardam a20 março 2025
Fé, sal grosso e memes: como os torcedores do Palmeiras aguardam a20 março 2025
