Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Last updated 01 abril 2025


Resources Archives - Page 3 of 12 - F-Secure Blog

Internet Archive Blogs A blog from the team at archive.org

Hacking Archives - F-Secure Blog

THREAT ANALYSIS REPORT: Bumblebee Loader – The High Road to

Prometheus TDS

F-Secure Labs (@FSecureLabs) / X

New campaign targeting security researchers

Threats & Research Archives - F-Secure Blog
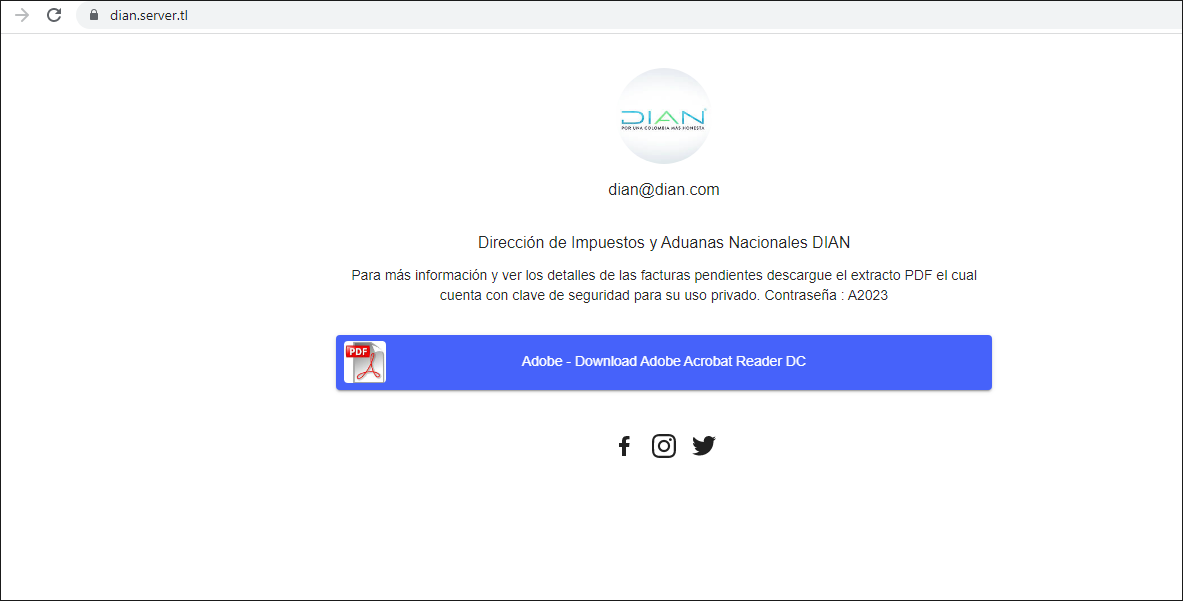
Blind Eagle Deploys Fake UUE Files and Fsociety to Target
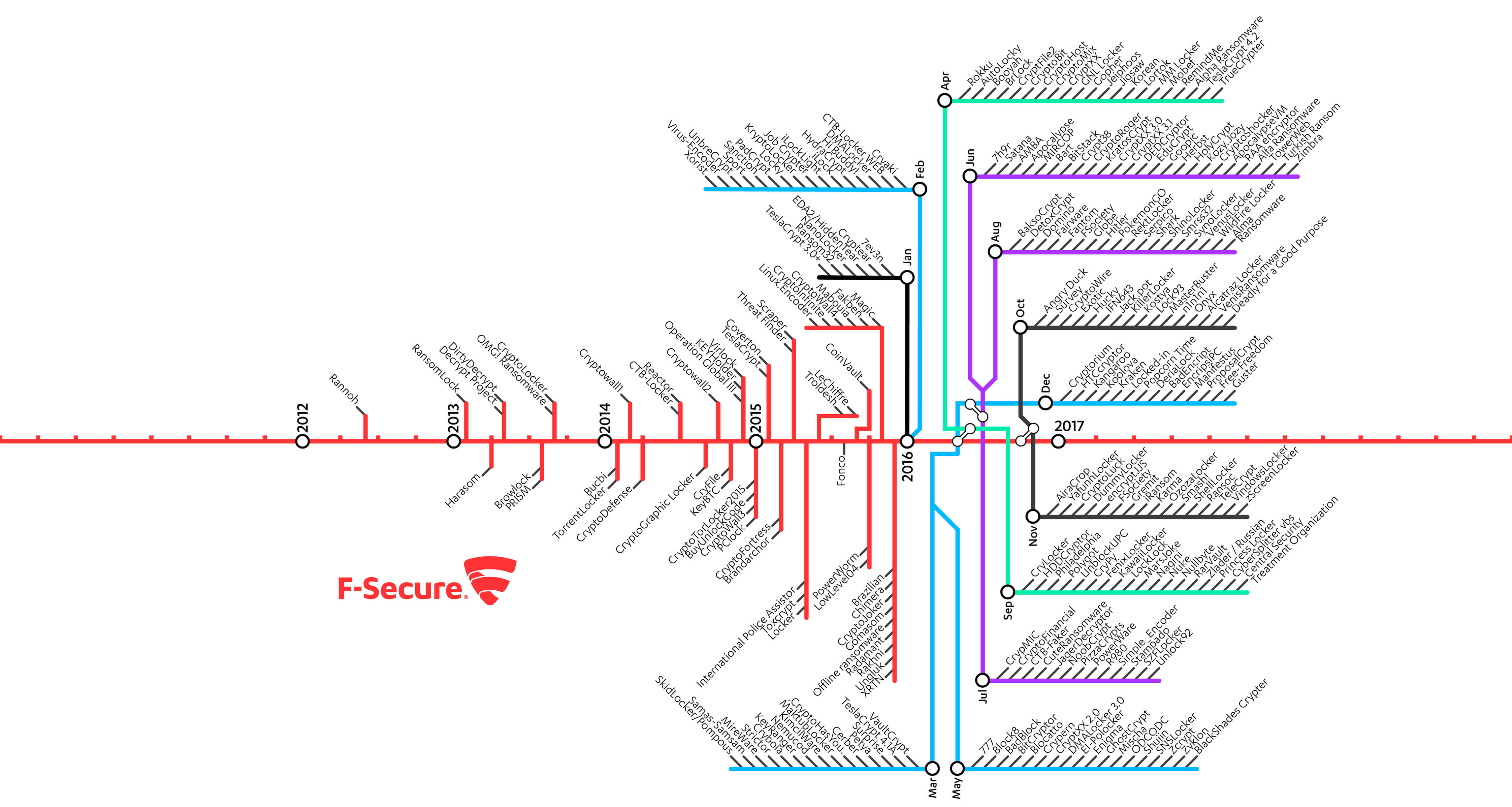
How 4 Types of Cyber Threats Break Your Online Security [INFOGRAPHIC]

CrowdStrike Prevents 3CXDesktopApp Intrusion Campaign

Security in the billions: Toward a multinational strategy to

Cyble — Threat Actor Employs PowerShell-Backed Steganography in

13 in the LEI Lightbulb Blog Series - Understanding the Value of
Recomendado para você
-
 Online Hacker Simulator and Typer01 abril 2025
Online Hacker Simulator and Typer01 abril 2025 -
 Anonymous (hacker group) - Wikipedia01 abril 2025
Anonymous (hacker group) - Wikipedia01 abril 2025 -
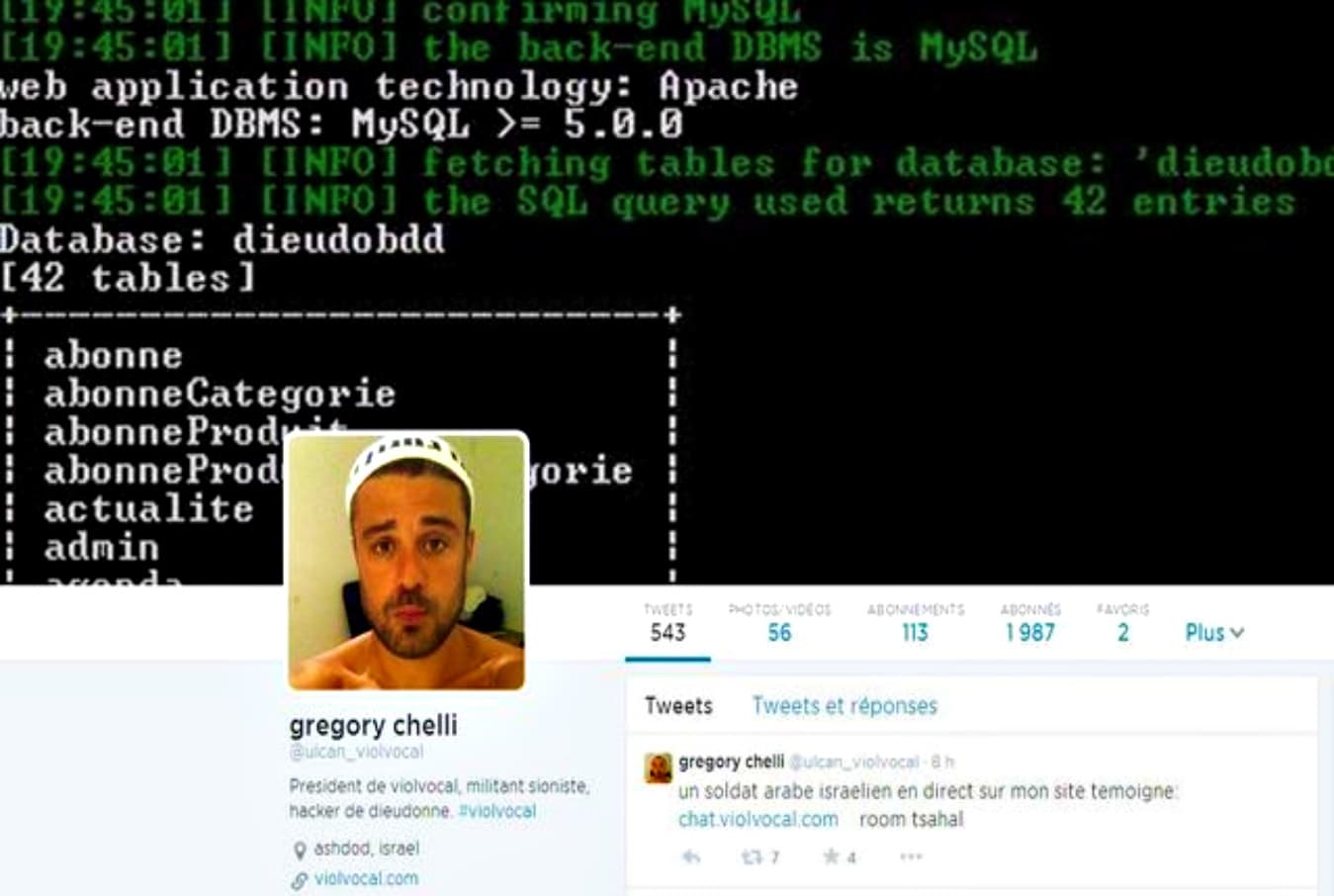 Death linked to prank - France seeks extradition of hacker from Israel01 abril 2025
Death linked to prank - France seeks extradition of hacker from Israel01 abril 2025 -
 Hacks at the Massachusetts Institute of Technology - Wikipedia01 abril 2025
Hacks at the Massachusetts Institute of Technology - Wikipedia01 abril 2025 -
How to hack your friends01 abril 2025
-
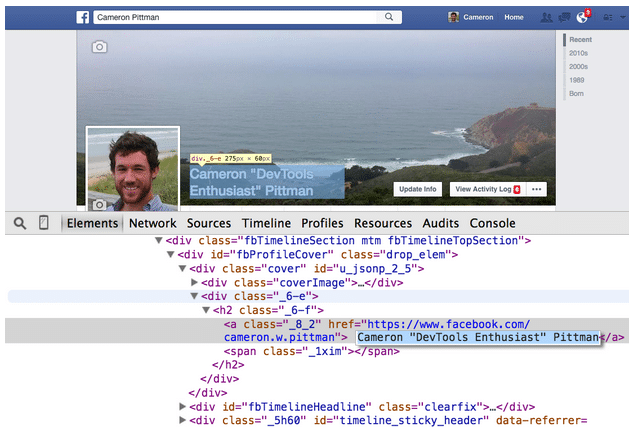 Developer Tools: Facebook “Hacking” Tutorial01 abril 2025
Developer Tools: Facebook “Hacking” Tutorial01 abril 2025 -
 Group claiming ties to Islamic State appear to have hacked key01 abril 2025
Group claiming ties to Islamic State appear to have hacked key01 abril 2025 -
fake hacker prank website|TikTok Search01 abril 2025
-
 Leave no trace: how a teenage hacker lost himself online01 abril 2025
Leave no trace: how a teenage hacker lost himself online01 abril 2025 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/CRPSIVI225EMZL6F5P4MHD5SNA.jpg) The Art of the Prank: How a Hacker Tried to Fake the World's Most Expensive NFT - CoinDesk01 abril 2025
The Art of the Prank: How a Hacker Tried to Fake the World's Most Expensive NFT - CoinDesk01 abril 2025
você pode gostar
-
 Deu trabalho, mas consegui! Vetorizei o Yusuke Urameshi do anime Yu Yu Hakusho, um dos que eu gostava muito de assistir …01 abril 2025
Deu trabalho, mas consegui! Vetorizei o Yusuke Urameshi do anime Yu Yu Hakusho, um dos que eu gostava muito de assistir …01 abril 2025 -
 Placa QAZ9H02 - TOYOTA COROLLA XEI 20 2022 - Placa Fipe01 abril 2025
Placa QAZ9H02 - TOYOTA COROLLA XEI 20 2022 - Placa Fipe01 abril 2025 -
 a chat with Red Dead 2's ARTHUR MORGAN (Roger Clark)01 abril 2025
a chat with Red Dead 2's ARTHUR MORGAN (Roger Clark)01 abril 2025 -
 basic eye design- simple cartoon/anime mouth01 abril 2025
basic eye design- simple cartoon/anime mouth01 abril 2025 -
 Jenny Wakeman transparent background PNG cliparts free download01 abril 2025
Jenny Wakeman transparent background PNG cliparts free download01 abril 2025 -
 Flamenco Soundslice01 abril 2025
Flamenco Soundslice01 abril 2025 -
 Funky Photo Effects, Fotor – Free Online Funky Photo Effects & Filters01 abril 2025
Funky Photo Effects, Fotor – Free Online Funky Photo Effects & Filters01 abril 2025 -
 Dois jogos de futebol grátis para Android - dfiligames01 abril 2025
Dois jogos de futebol grátis para Android - dfiligames01 abril 2025 -
 ANIME CLOUD — Mahoutsukai no Yome Season 2 Part 2 OP01 abril 2025
ANIME CLOUD — Mahoutsukai no Yome Season 2 Part 2 OP01 abril 2025 -
 Raspberry pi zero 2 w quad-core 64-bit Cortex-A53 bluetooth ble01 abril 2025
Raspberry pi zero 2 w quad-core 64-bit Cortex-A53 bluetooth ble01 abril 2025

