The Newest Variant of the Astaroth Trojan Evades Detection in the
Por um escritor misterioso
Last updated 25 abril 2025
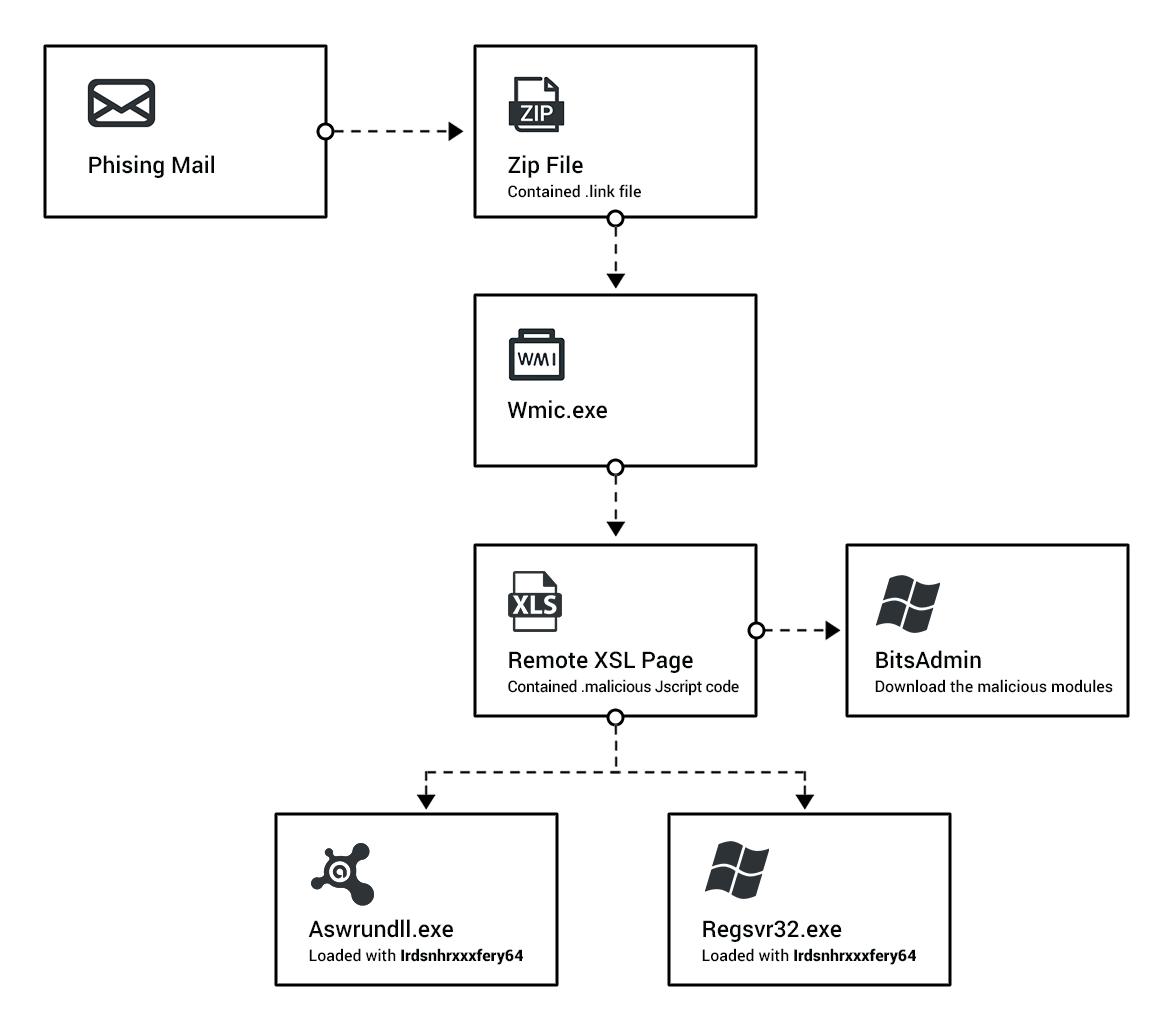
In this malware research, we explain one of the most recent and unique campaigns involving the Astaroth trojan. This Trojan and information stealer affected Europe and especially Brazil through the abuse of native OS processes and the exploitation of security-related products.

Cybereason Nocturnus, Authors, Malicious Life Network
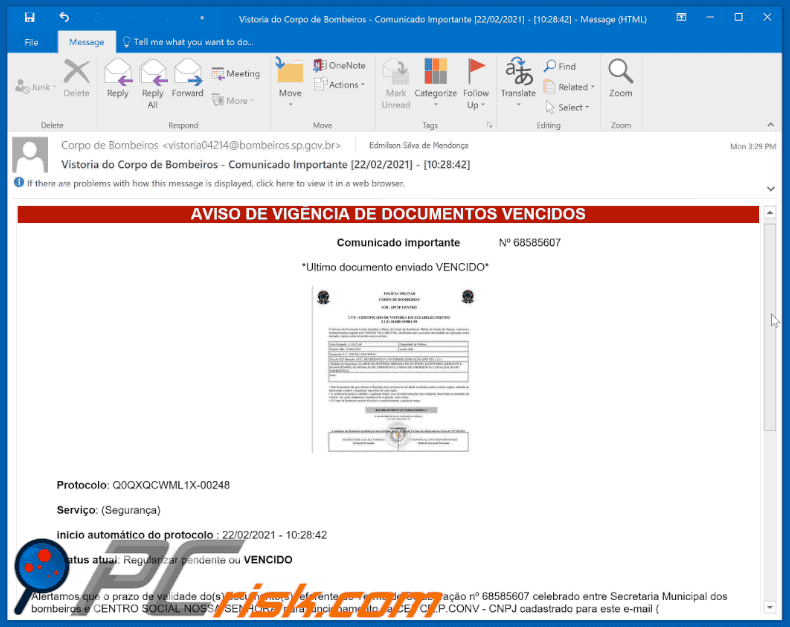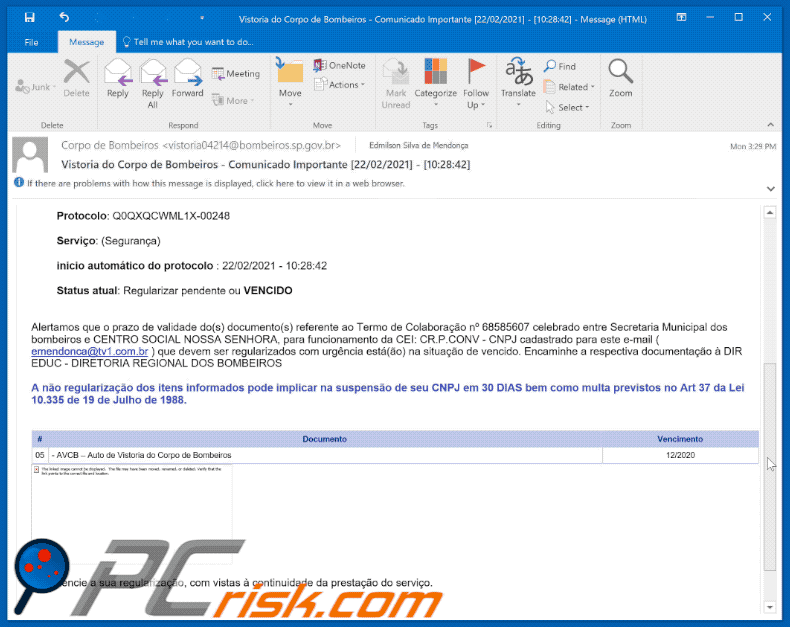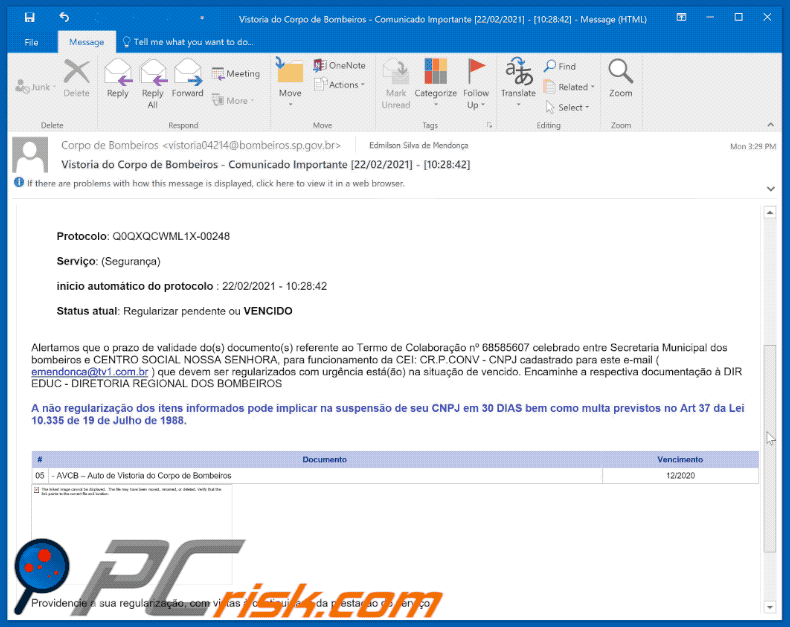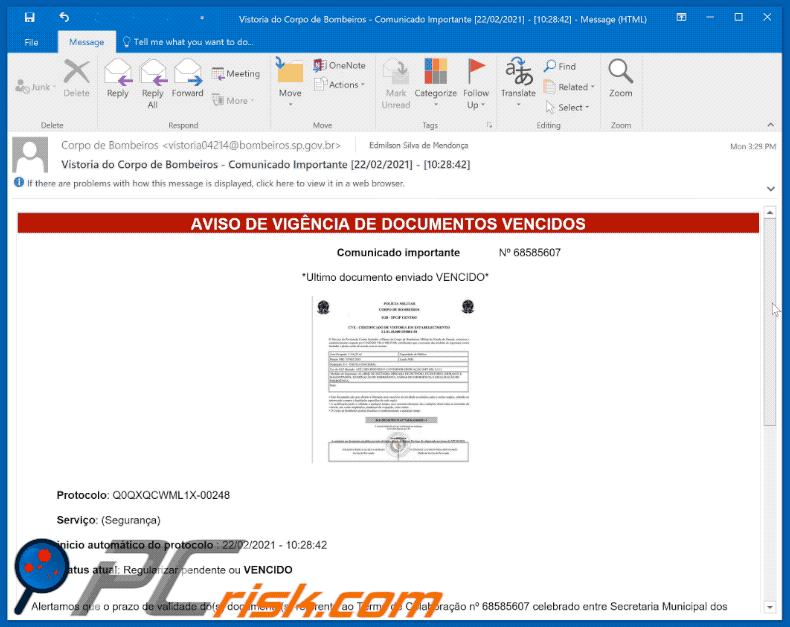
Astaroth Trojan - Malware removal instructions (updated)
JCP, Free Full-Text
Astaroth Malware Uses Legitimate OS and Antivirus Processes to Steal Passwords and Personal Data

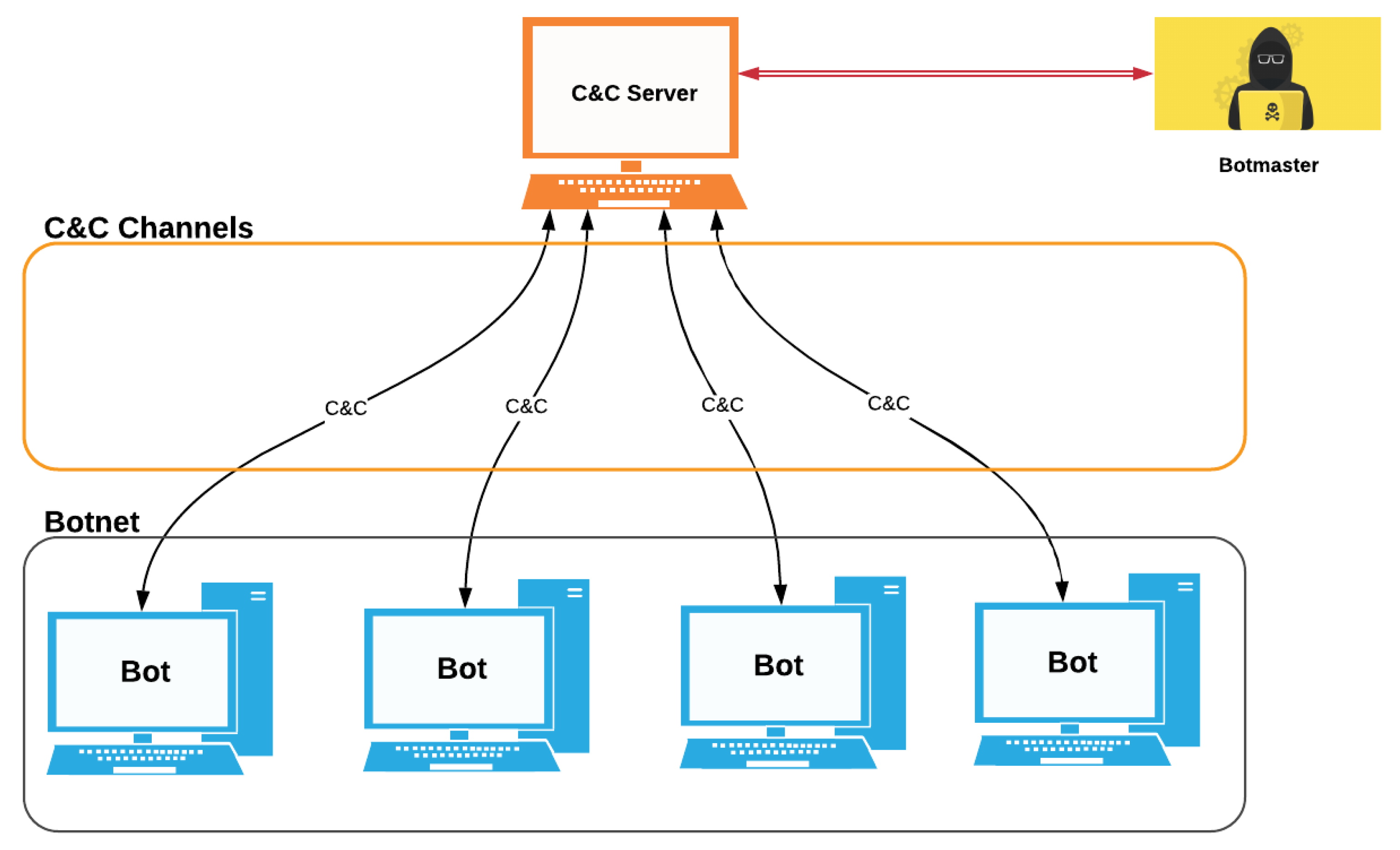
Command-and-Control (C&C) - Security Intelligence

Trojan - Security Intelligence

Guildma: The Devil drives electric

No Win32 Process Needed Expanding the WMI Lateral Movement Arsenal
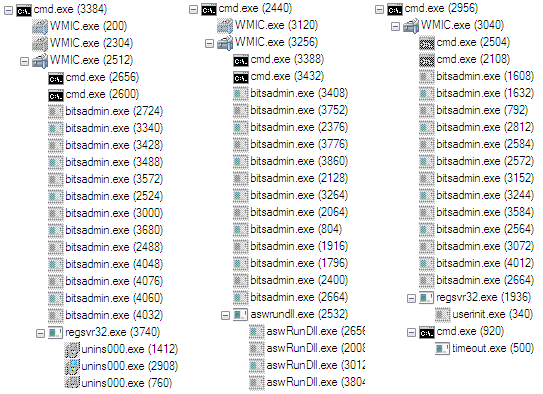
Astaroth Malware Uses Legitimate OS and Antivirus Processes to Steal Passwords and Personal Data

Fecebook and Profiles to Host Astaroth Malware C2 Server

Microsoft Discovers Fileless Malware Campaign Dropping Astaroth Info Stealer - Nachrichten zum Thema Sicherheit - Trend Micro DE

IFinder Info Solutions

Glimpsing inside the trojan horse: An insider analysis of Emotet
Recomendado para você
-
 Evades (2016), Encantadia Wiki25 abril 2025
Evades (2016), Encantadia Wiki25 abril 2025 -
 How to Evade in Star Wars Jedi: Survivor25 abril 2025
How to Evade in Star Wars Jedi: Survivor25 abril 2025 -
 Fox Evades25 abril 2025
Fox Evades25 abril 2025 -
No Sin Evades His Gaze25 abril 2025
-
 Good Pretty Sharp Intellect Evades The Pursuer Enola Holmes Funny Acrylic Print by Inny Shop - Pixels25 abril 2025
Good Pretty Sharp Intellect Evades The Pursuer Enola Holmes Funny Acrylic Print by Inny Shop - Pixels25 abril 2025 -
 Evades memes. Best Collection of funny Evades pictures on iFunny Brazil25 abril 2025
Evades memes. Best Collection of funny Evades pictures on iFunny Brazil25 abril 2025 -
 Landmark Court Decision: Marijuana Grower Evades Felony Charges Due to25 abril 2025
Landmark Court Decision: Marijuana Grower Evades Felony Charges Due to25 abril 2025 -
 Solana and Arbitrum knocked offline, while Ethereum evades attack25 abril 2025
Solana and Arbitrum knocked offline, while Ethereum evades attack25 abril 2025 -
Loose emu evades capture in Lakevillev_1N5nqFiRwB25 abril 2025
-
 Barkley evades the tackle for 15-yard gain25 abril 2025
Barkley evades the tackle for 15-yard gain25 abril 2025
você pode gostar
-
 Ubisoft Assassin's Creed Origins, PS4 Basic PlayStation 4 video game - video games (PS4, Basic, PlayStation 4, Action / Adventure, RP (Rating25 abril 2025
Ubisoft Assassin's Creed Origins, PS4 Basic PlayStation 4 video game - video games (PS4, Basic, PlayStation 4, Action / Adventure, RP (Rating25 abril 2025 -
ZAP Fibra - A ZAP traz-lhe em directo e em exclusivo os25 abril 2025
-
 How to minimize game lags in Windows 10 in 7 steps25 abril 2025
How to minimize game lags in Windows 10 in 7 steps25 abril 2025 -
 ABRIMOS UMA LOJA DE CAMISETAS BRANCOALA NO BRASIL!25 abril 2025
ABRIMOS UMA LOJA DE CAMISETAS BRANCOALA NO BRASIL!25 abril 2025 -
K's Koncepts on X: #602 Funko Pop! Box & Pop Concept: Eda & The25 abril 2025
-
 Generating The Universe in Elite: Dangerous25 abril 2025
Generating The Universe in Elite: Dangerous25 abril 2025 -
 Megami no Café Terrace Capítulo 106 - Manga Online25 abril 2025
Megami no Café Terrace Capítulo 106 - Manga Online25 abril 2025 -
 Won't Rian Johnson's Poker Face Just Be A Knives Out Copy?25 abril 2025
Won't Rian Johnson's Poker Face Just Be A Knives Out Copy?25 abril 2025 -
 HoYoverse Anime Expo 2023 Lineup Includes Genshin Impact, Honkai Impact 3rd, Honkai: Star Rail, and Zenless Zone Zero - QooApp News25 abril 2025
HoYoverse Anime Expo 2023 Lineup Includes Genshin Impact, Honkai Impact 3rd, Honkai: Star Rail, and Zenless Zone Zero - QooApp News25 abril 2025 -
 Significado del apellido camille - Significados de los apellidos25 abril 2025
Significado del apellido camille - Significados de los apellidos25 abril 2025



