SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 01 abril 2025

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.
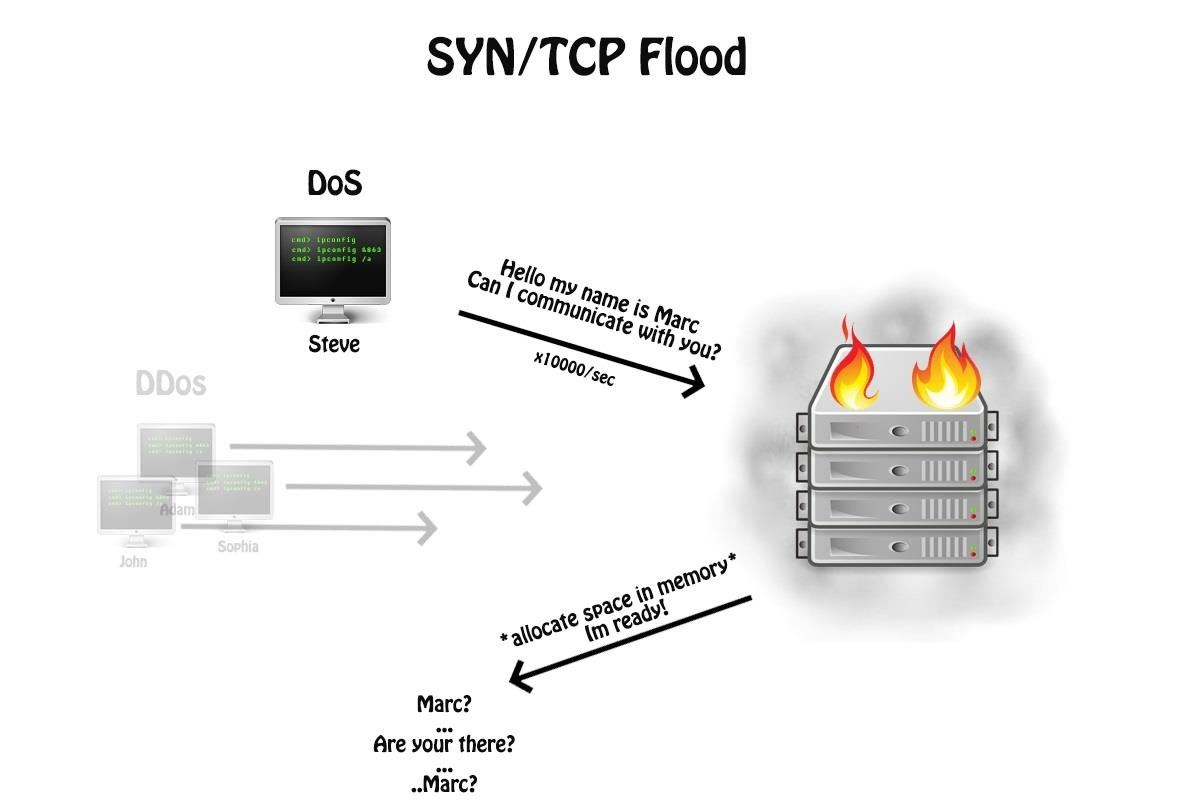
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 4 (Evading Detection While DoSing) « Null Byte :: WonderHowTo

1-15 March 2023 Cyber Attacks Timeline – HACKMAGEDDON

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Hackers start using double DLL sideloading to evade detection
Lynx-CERT

Exaramel Malware Links Industroyer ICS malware and NotPetya wiper
AV/EDR Evasion, Malware Development P-3

New Godlua Backdoor Found Abusing DNS Over HTTPS (DoH) Protocol - Noticias de seguridad - Trend Micro ES

Endpoint Protection - Symantec Enterprise

Lynx-CERT

Malware - Wikipedia
Recomendado para você
-
![NEW] Evade Script / Hack GUI, God Mode](https://i.ytimg.com/vi/nHcDYO46Ib8/maxresdefault.jpg) NEW] Evade Script / Hack GUI, God Mode01 abril 2025
NEW] Evade Script / Hack GUI, God Mode01 abril 2025 -
evade script|TikTok Search01 abril 2025
-
evade mobile script|TikTok Search01 abril 2025
-
![Evade [Auto Farm - Fast Revive & More!] Scripts](https://rbxscript.com/images/-nOtc6We36d-image.jpg) Evade [Auto Farm - Fast Revive & More!] Scripts01 abril 2025
Evade [Auto Farm - Fast Revive & More!] Scripts01 abril 2025 -
 Snippet of Server-side script generated by ChatGPT to evade01 abril 2025
Snippet of Server-side script generated by ChatGPT to evade01 abril 2025 -
 CanHub Evade Script Download 100% Free01 abril 2025
CanHub Evade Script Download 100% Free01 abril 2025 -
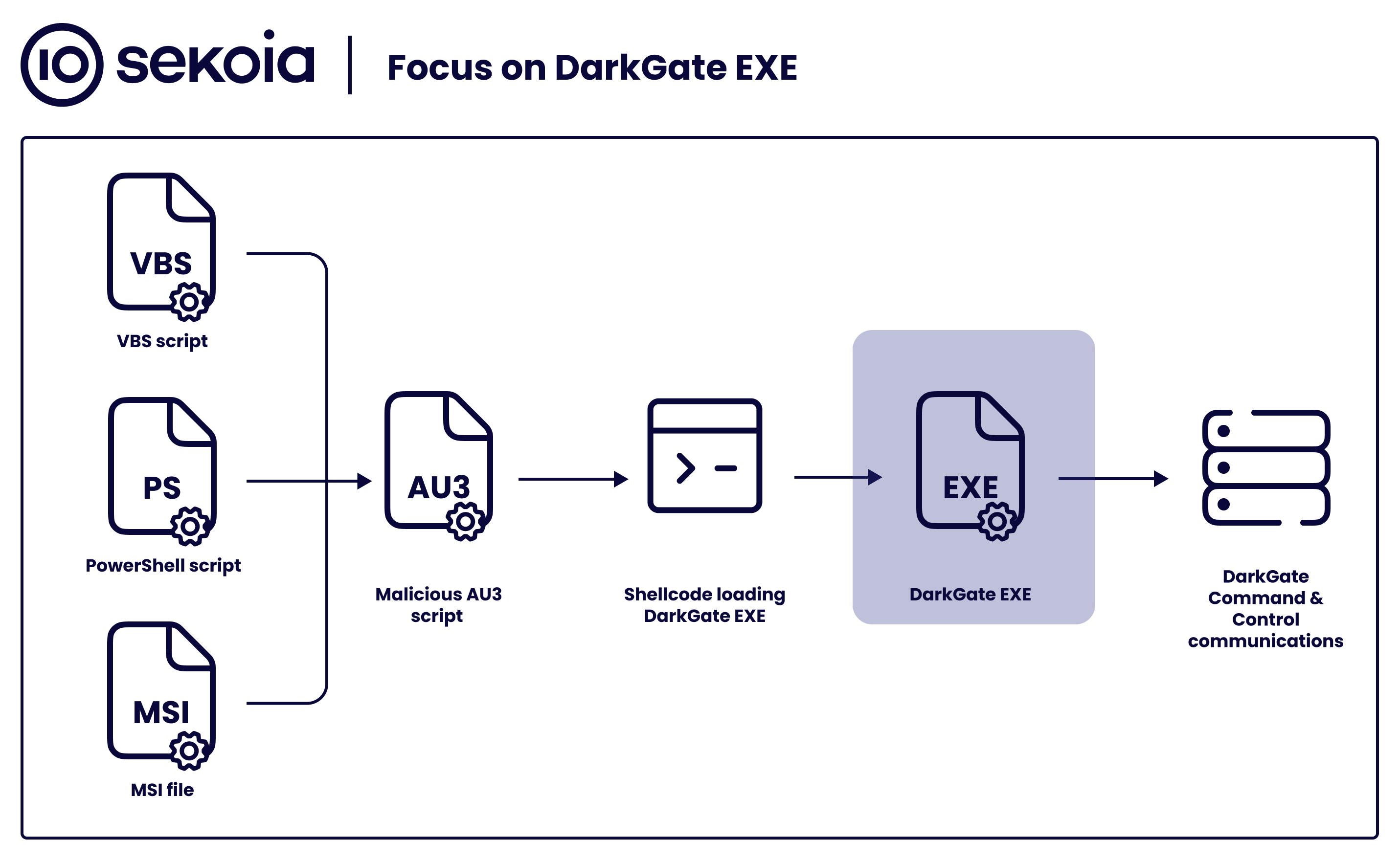
Sekoia.io on X: #DarkGate gained popularity among threat actors01 abril 2025
-
evade script template|TikTok Search01 abril 2025
-
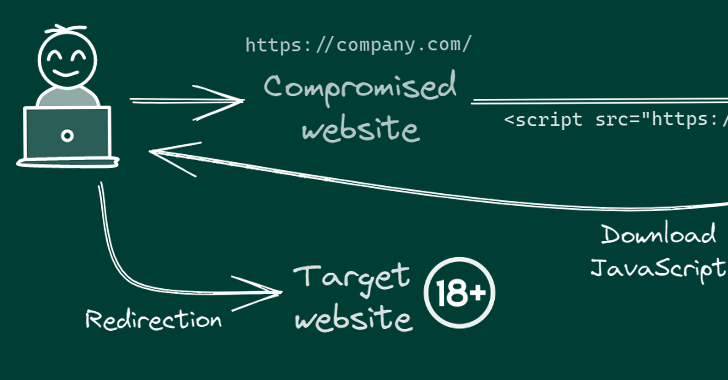 Malicious Python Package Uses Unicode Trickery to Evade Detection01 abril 2025
Malicious Python Package Uses Unicode Trickery to Evade Detection01 abril 2025 -
 Evade Scripts - Blox Fruit Script01 abril 2025
Evade Scripts - Blox Fruit Script01 abril 2025
você pode gostar
-
 Jogo Tabuleiro Pequeno Fazendeiro Pais & Filhos01 abril 2025
Jogo Tabuleiro Pequeno Fazendeiro Pais & Filhos01 abril 2025 -
my tier list of barbie faces updated with new faces #slay #trader01 abril 2025
-
 Baltoy Claydol Pokémon Pokédex Bulbapedia, baltoy, png01 abril 2025
Baltoy Claydol Pokémon Pokédex Bulbapedia, baltoy, png01 abril 2025 -
Hamster Care Sheet: Food, Habitat & Health01 abril 2025
-
 Só Pra Contrariar - Fundo de Quintal - VAGALUME01 abril 2025
Só Pra Contrariar - Fundo de Quintal - VAGALUME01 abril 2025 -
Who is Roronoa Zoro in One Piece?01 abril 2025
-
 10 Video Game Boss Battles Who Tricked You Into Thinking You'd Won01 abril 2025
10 Video Game Boss Battles Who Tricked You Into Thinking You'd Won01 abril 2025 -
 Pokemon Black 2 Cheats - Action Replay Codes For Nintendo DS01 abril 2025
Pokemon Black 2 Cheats - Action Replay Codes For Nintendo DS01 abril 2025 -
Kuro no Shoukanshi capitulo 1 sub español. Si te gusto dale like y Suscríbete, By Anime01 abril 2025
-
ALAN WAKE'S AMERICAN NIGHTMARE Gameplay Walkthrough PART 4 XBOX 360 Arcade - video Dailymotion01 abril 2025