— Proton Exploit
Por um escritor misterioso
Last updated 22 março 2025
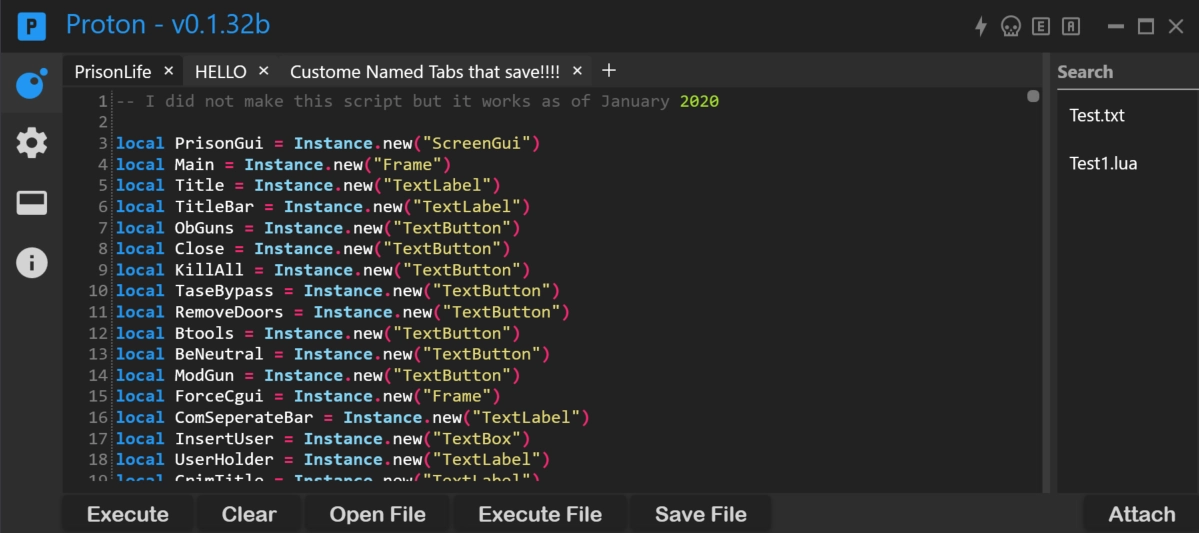

De-Anonymization attacks against Proton services

Defending online freedom with technology

What Are Zero-Day Exploits and Attacks?

WinRAR Vulnerability Puts Illicit Content Consumers at Risk of Apanyan Stealer, Murk-Stealer & AsyncRAT — Cyble

Proton Pass security flaw exposed: Firefox users at risk

Code Vulnerabilities Put Proton Mails at Risk

Strategies to Enhance the Rate of Proton‐Coupled Electron Transfer Reactions in Dye‐Water Oxidation Catalyst Complexes - Haas - 2023 - ChemPhotoChem - Wiley Online Library

Code Vulnerabilities Put Proton Mails at Risk

De-Anonymization attacks against Proton services

Lot #175 - GHOSTBUSTERS (2016) - Light-Up V-3 Style Proton Pack
A breakdown of a DKIM replay attack

Agrius group targets Israel with data-wipers disguised as ransomware

Development of a Typical Distribution Function of Relaxation Times Model for Polymer Electrolyte Membrane Fuel Cells and Quantifying the Resistance to Proton Conduction within the Catalyst Layer
Recomendado para você
-
 jjsploit queries - WRD Community22 março 2025
jjsploit queries - WRD Community22 março 2025 -
 is jjsploit safe? : r/ROBLOXExploiting22 março 2025
is jjsploit safe? : r/ROBLOXExploiting22 março 2025 -
Free Script Executor Roblox22 março 2025
-
 Free Electron Download 202122 março 2025
Free Electron Download 202122 março 2025 -
What are the best Roblox exploits and how do you use them? - Quora22 março 2025
-
 WeAreDevs World Congress 22 on the App Store22 março 2025
WeAreDevs World Congress 22 on the App Store22 março 2025 -
 WeAreDevelopers World Congress22 março 2025
WeAreDevelopers World Congress22 março 2025 -
Isabelle Borgert on LinkedIn: #droidcon #applicationstore #vw #androidautomotive #cariad #volkswagen…22 março 2025
-
 DCX 22 on the App Store22 março 2025
DCX 22 on the App Store22 março 2025 -
![Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 2023](https://i.ytimg.com/vi/7BUrPkEP9dc/maxresdefault.jpg) Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 202322 março 2025
Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 202322 março 2025
você pode gostar
-
 fotos de perfil de meninas de cria|Pesquisa do TikTok22 março 2025
fotos de perfil de meninas de cria|Pesquisa do TikTok22 março 2025 -
 Remastering Starter Place Billboard - Creations Feedback - Developer Forum22 março 2025
Remastering Starter Place Billboard - Creations Feedback - Developer Forum22 março 2025 -
 Val x Love - The Fall 2019 Anime Preview Guide - Anime News Network22 março 2025
Val x Love - The Fall 2019 Anime Preview Guide - Anime News Network22 março 2025 -
 Isekai-Shoukan-wa Nidome-desu Vol. 1-10 latest volume Manga Comic22 março 2025
Isekai-Shoukan-wa Nidome-desu Vol. 1-10 latest volume Manga Comic22 março 2025 -
 RickRollEye 64, 007 Goldeneye with memes - N64 Squid22 março 2025
RickRollEye 64, 007 Goldeneye with memes - N64 Squid22 março 2025 -
The 100 Greatest Drummers Of All Time (In Order)22 março 2025
-
 Doodle chess checkmate king queen Royalty Free Vector Image22 março 2025
Doodle chess checkmate king queen Royalty Free Vector Image22 março 2025 -
 Gummy Bear Song Lyrics APK for Android Download22 março 2025
Gummy Bear Song Lyrics APK for Android Download22 março 2025 -
 Killing Stalking - Koogi - BL - Webtoons - Lezhin Comics22 março 2025
Killing Stalking - Koogi - BL - Webtoons - Lezhin Comics22 março 2025 -
 Download Roblox Theme for Windows 10/1122 março 2025
Download Roblox Theme for Windows 10/1122 março 2025
