Screen-shots of Part I and III of the user study. The usernames
Por um escritor misterioso
Last updated 16 abril 2025


Login and complete requirements - Global Study Partners
Configuring Siebel Enterprise Targets

Solved Question 6JS/AJAX/PHP Create HTML form that contains
How to (back)stitch your custom user id to GA4's client id in
Phishing-resistant MFA, Zero Trust, Cloudflare
User Management

Solved All screenshots, must have your username at command

NITA-Uganda on X: #kolibri is an e-learning service that helps

Rosetta Stone – Idaho Falls Public Library

InstructorLogin - OLLI AT DUKE ONLINE LEARNING
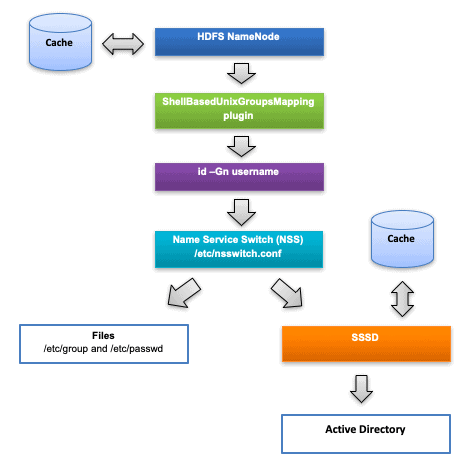
Best Practices Guide for Systems Security Services Daemon
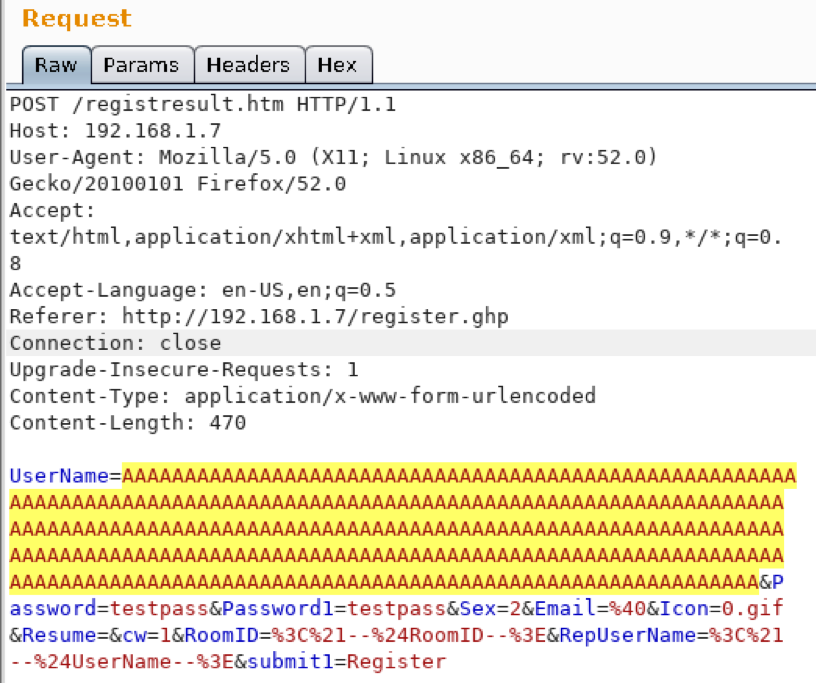
Exploit Development - Part 1: Python Exploit Development
Recomendado para você
-
 Champion classes, League of Legends Wiki16 abril 2025
Champion classes, League of Legends Wiki16 abril 2025 -
 LOL Meaning: What Does The Term LOL Mean and Stand For? • 7ESL16 abril 2025
LOL Meaning: What Does The Term LOL Mean and Stand For? • 7ESL16 abril 2025 -
 Terms That Every League of Legends Player Should Know - Mobalytics16 abril 2025
Terms That Every League of Legends Player Should Know - Mobalytics16 abril 2025 -
EdwardKing02🎄 on X: My favorite narrow gauge engine, its Sir16 abril 2025
-
Autumn Designs NZ - Personalised Keepsake Prints16 abril 2025
-
 This cheat sheet confuses me. Which scale is it showing? Isn't16 abril 2025
This cheat sheet confuses me. Which scale is it showing? Isn't16 abril 2025 -
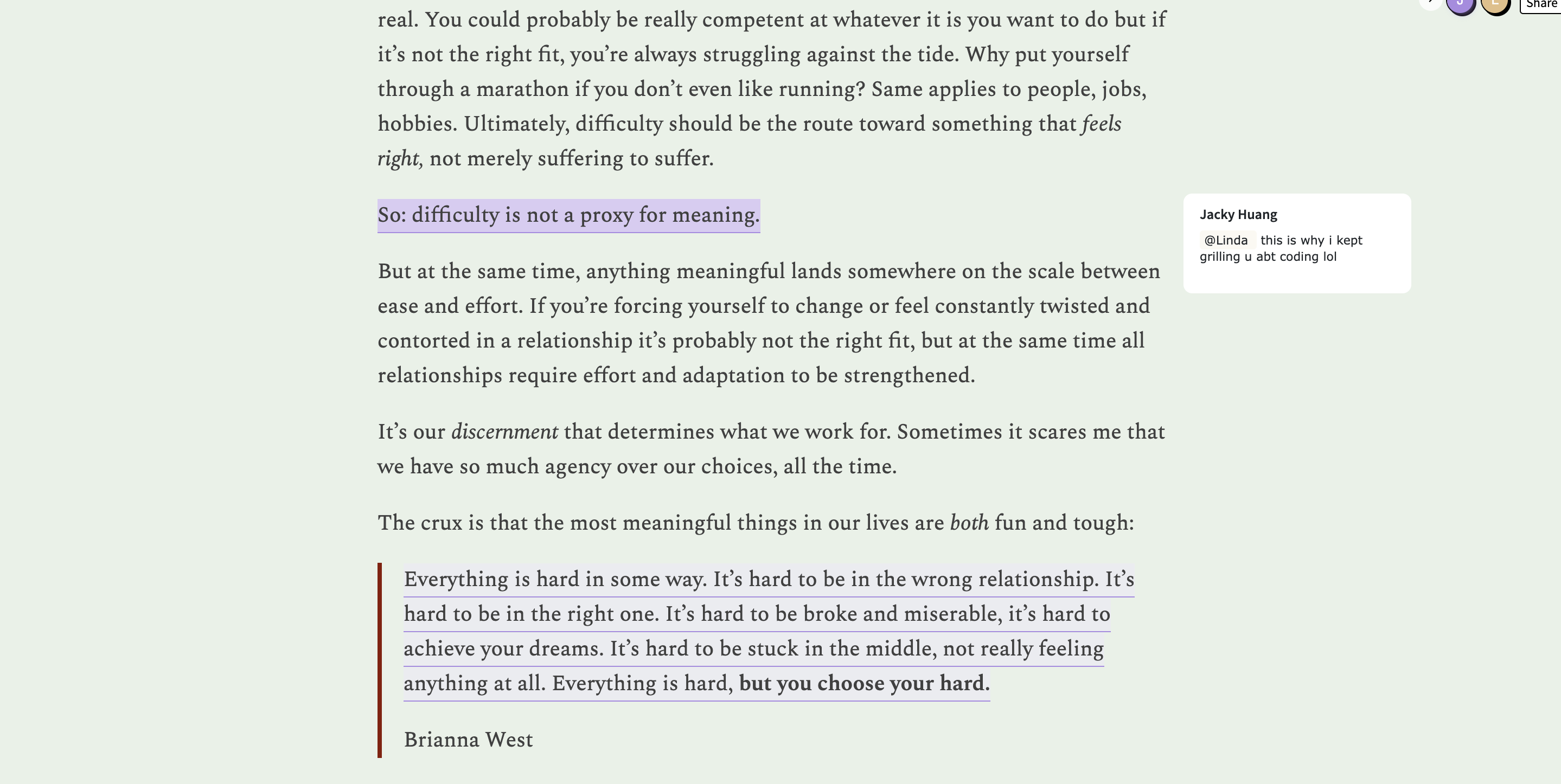 Social learning - Linda Tong16 abril 2025
Social learning - Linda Tong16 abril 2025 -
Is it true that the under-scales of snakes can show if the snake16 abril 2025
-
American Clinical Experience16 abril 2025
-
 How does scaling work. : r/summonerschool16 abril 2025
How does scaling work. : r/summonerschool16 abril 2025
você pode gostar
-
 Peaches by Vihn Nguyen Justin bieber hit songs, Online dance classes, Dance instructor16 abril 2025
Peaches by Vihn Nguyen Justin bieber hit songs, Online dance classes, Dance instructor16 abril 2025 -
8 Ball Pool (GameLoop) para Windows - Baixe gratuitamente na Uptodown16 abril 2025
-
 Legendary Expeditions16 abril 2025
Legendary Expeditions16 abril 2025 -
 Unconscious Ventriloquism: The Unsolved Mystery of the Zaragoza16 abril 2025
Unconscious Ventriloquism: The Unsolved Mystery of the Zaragoza16 abril 2025 -
mecha sonic mk 1|TikTok Search16 abril 2025
-
 Beacon Hill (2021) - IMDb16 abril 2025
Beacon Hill (2021) - IMDb16 abril 2025 -
 minha personagem do roblox (gatinha lucita) by 12iLucitaGamesAnima16 abril 2025
minha personagem do roblox (gatinha lucita) by 12iLucitaGamesAnima16 abril 2025 -
A lenda vai voltar! #naruto #anime #setembro16 abril 2025
-
My Next Life as a Villainess: All Routes Lead to Doom! - Nintendo Switch, Nintendo Switch16 abril 2025
-
 Darkspine Sonic by Sweecrue on DeviantArt16 abril 2025
Darkspine Sonic by Sweecrue on DeviantArt16 abril 2025