Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 31 março 2025
What is Malware Analysis? - SOC Prime

Malware Analysis: Steps & Examples - CrowdStrike

Behavioral blocking and containment: Transforming optics into
Free Automated Malware Analysis Sandboxes for Incident Response

How to Detect New Threats via Suspicious Activities
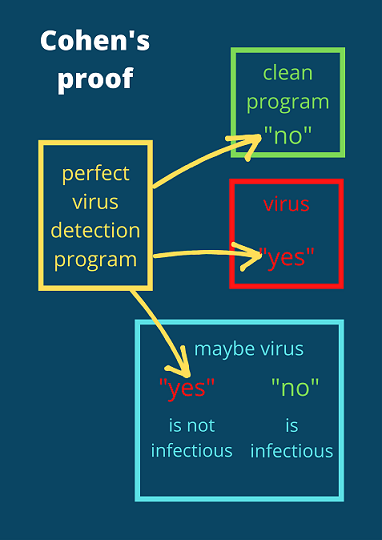
The real reason why malware detection is hard
Introducing malware analysis: enhance your cybersecurity triage

Malware Incident Response Steps on Windows, and Determining If the

Malware Analysis Framework v1.0

Malware Detection: 7 Methods and Security Solutions that Use Them

Security Orchestration Use Case: Automating Malware Analysis

Malware Analysis Benefits Incident Response
Recomendado para você
-
How to Hack Roblox and Should You Do it?31 março 2025
-
 Cuidado! Extensão do Chrome rouba dados de conta no Roblox31 março 2025
Cuidado! Extensão do Chrome rouba dados de conta no Roblox31 março 2025 -
Delta Executor [Latest Version]31 março 2025
-
 how to hack robux Play hacks, Android hacks, Roblox31 março 2025
how to hack robux Play hacks, Android hacks, Roblox31 março 2025 -
 Roblox Hack EXCLUSIVE Download31 março 2025
Roblox Hack EXCLUSIVE Download31 março 2025 -
 7 Hacks ideas roblox, roblox gifts, create an avatar31 março 2025
7 Hacks ideas roblox, roblox gifts, create an avatar31 março 2025 -
 Roblox Hack Roblox pictures, Roblox, Ios games31 março 2025
Roblox Hack Roblox pictures, Roblox, Ios games31 março 2025 -
Roblox Exploited with Trojans from Scripting Engine31 março 2025
-
 robux: Roblox 2023 guide: How to get free Robux? Here's what you need to know - The Economic Times31 março 2025
robux: Roblox 2023 guide: How to get free Robux? Here's what you need to know - The Economic Times31 março 2025 -
 Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire31 março 2025
Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire31 março 2025
você pode gostar
-
 Trem De Brinquedo Para Crianças Ilustração Vetorial Plana. Trem De Brinquedo Para Crianças No Fundo Branco. Infância, Entretenimento, Conceito De Transporte Royalty Free SVG, Cliparts, Vetores, e Ilustrações Stock. Image 19426475831 março 2025
Trem De Brinquedo Para Crianças Ilustração Vetorial Plana. Trem De Brinquedo Para Crianças No Fundo Branco. Infância, Entretenimento, Conceito De Transporte Royalty Free SVG, Cliparts, Vetores, e Ilustrações Stock. Image 19426475831 março 2025 -
 Shadow Warrior 3: Definitive Edition - IGN31 março 2025
Shadow Warrior 3: Definitive Edition - IGN31 março 2025 -
 Kami-tachi ni Hirowareta Otoko by Kikydream on DeviantArt31 março 2025
Kami-tachi ni Hirowareta Otoko by Kikydream on DeviantArt31 março 2025 -
 Rio characters offline code only Gacha Club by Adyneo on DeviantArt31 março 2025
Rio characters offline code only Gacha Club by Adyneo on DeviantArt31 março 2025 -
 MUSISALY Teclado Retroiluminado Teclado Punk Teclado Sem Fio De Viagem Teclado Pequeno Sem Fio Teclado Sem Fio Para Notebook Teclado Gamer Com Fio Teclado Digital Plástico Computador Número31 março 2025
MUSISALY Teclado Retroiluminado Teclado Punk Teclado Sem Fio De Viagem Teclado Pequeno Sem Fio Teclado Sem Fio Para Notebook Teclado Gamer Com Fio Teclado Digital Plástico Computador Número31 março 2025 -
 Phantom Forces Script, Nexus V231 março 2025
Phantom Forces Script, Nexus V231 março 2025 -
 Shopify – Hotjar Documentation31 março 2025
Shopify – Hotjar Documentation31 março 2025 -
CRIANDO O REINO DO COGUMELO - PressReader31 março 2025
-
 Arquivos the crew 2 pc download utorrent31 março 2025
Arquivos the crew 2 pc download utorrent31 março 2025 -
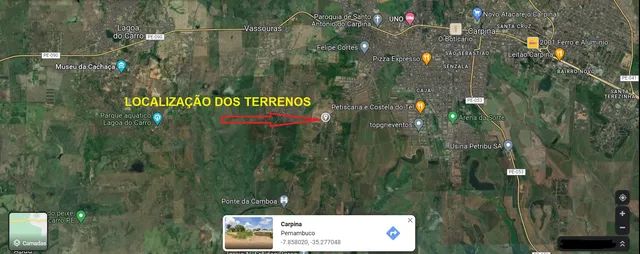 Oportunidade de negócio: Repasse dois lotes com suaves parcelas em Carpina! - Terrenos, sítios e fazendas - Santo Antônio, Carpina 109597466131 março 2025
Oportunidade de negócio: Repasse dois lotes com suaves parcelas em Carpina! - Terrenos, sítios e fazendas - Santo Antônio, Carpina 109597466131 março 2025