Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 30 março 2025
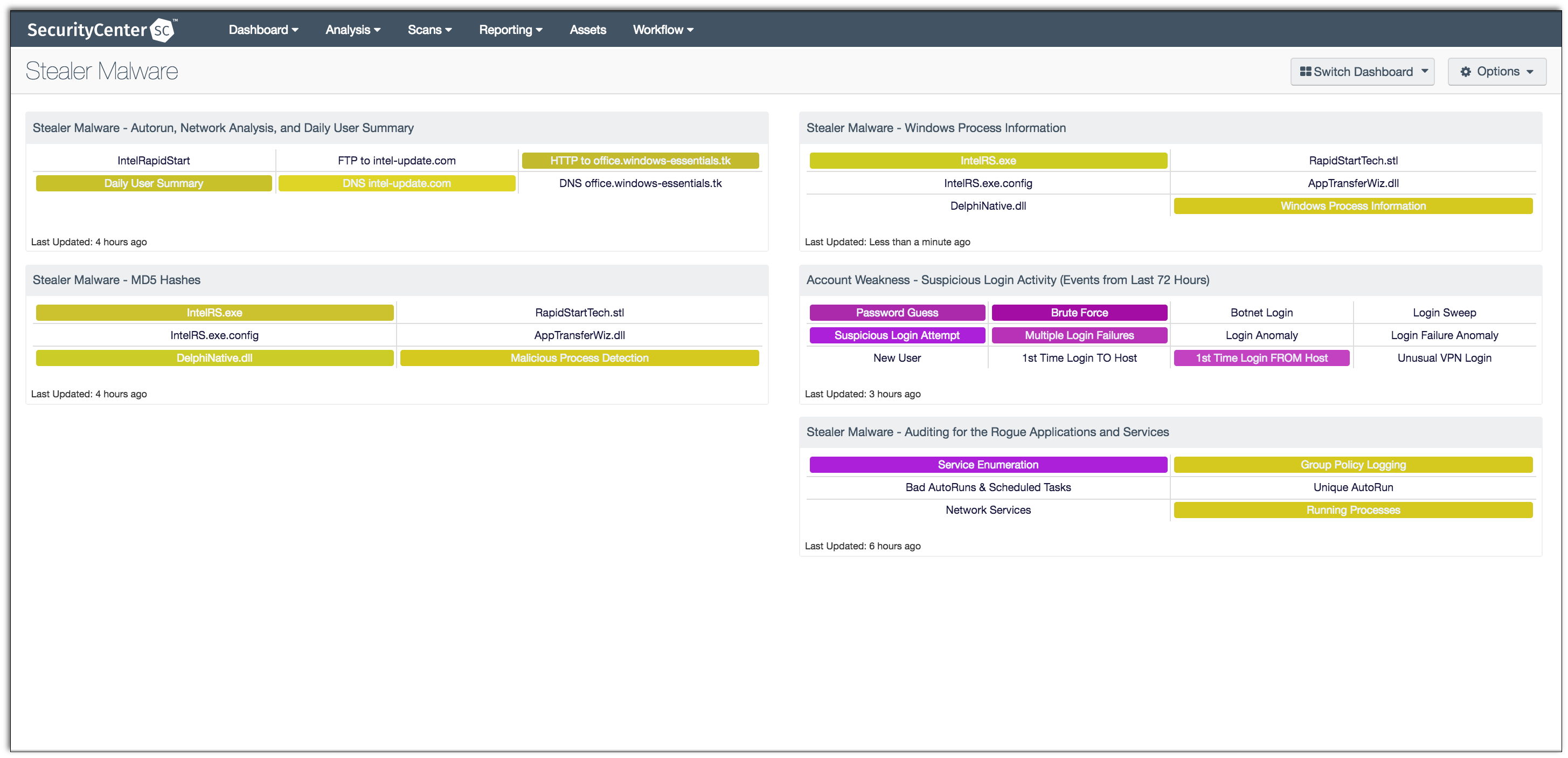
Stealer Malware - SC Dashboard

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis Benefits Incident Response

Malware Detection & Top Techniques Today
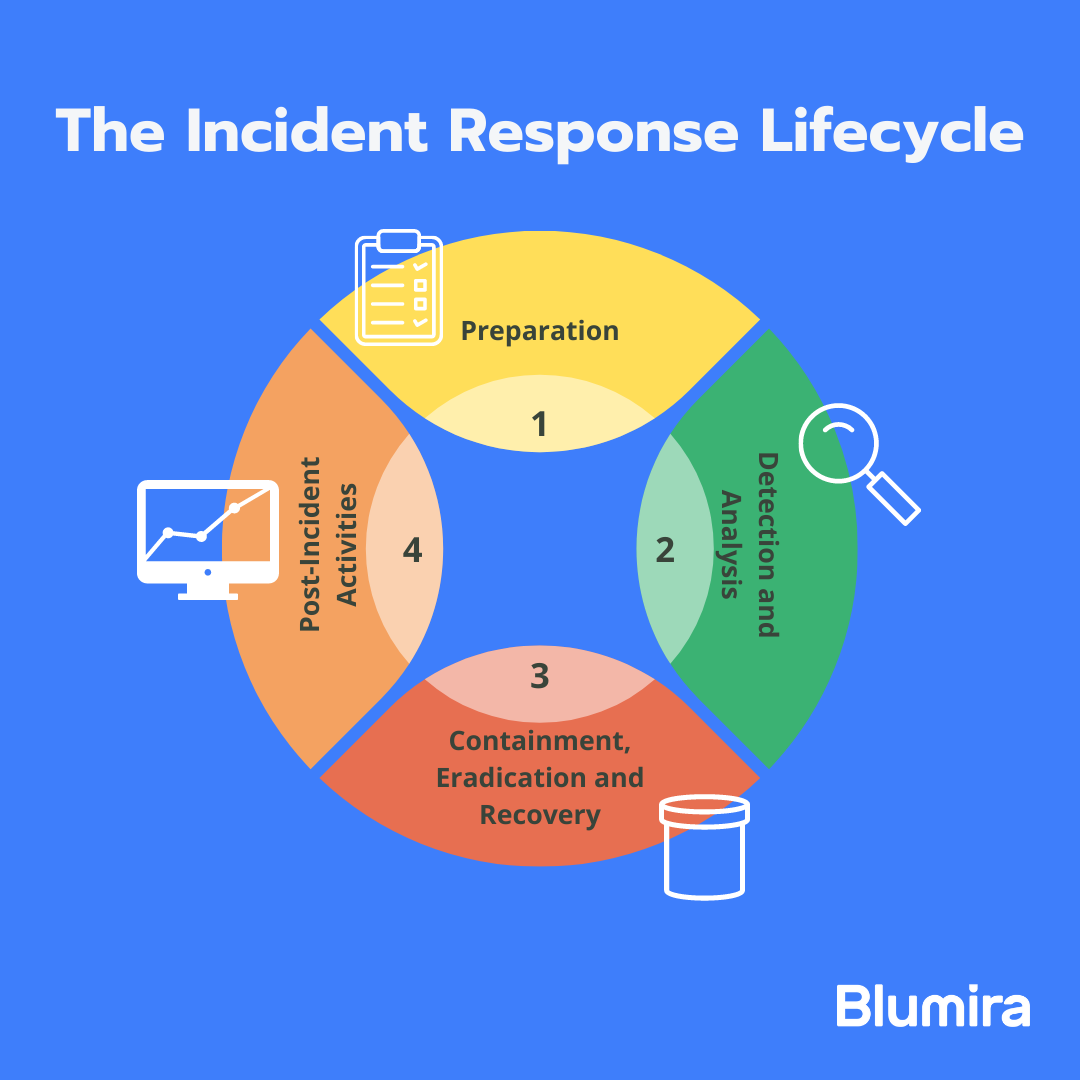
Building Effective Incident Response Procedures

1. General Flow of Signature-Based Malware Detection and Analysis

Election Security Spotlight – Malware Analysis

Malware Analysis and Reverse Engineering, by Ensar Seker
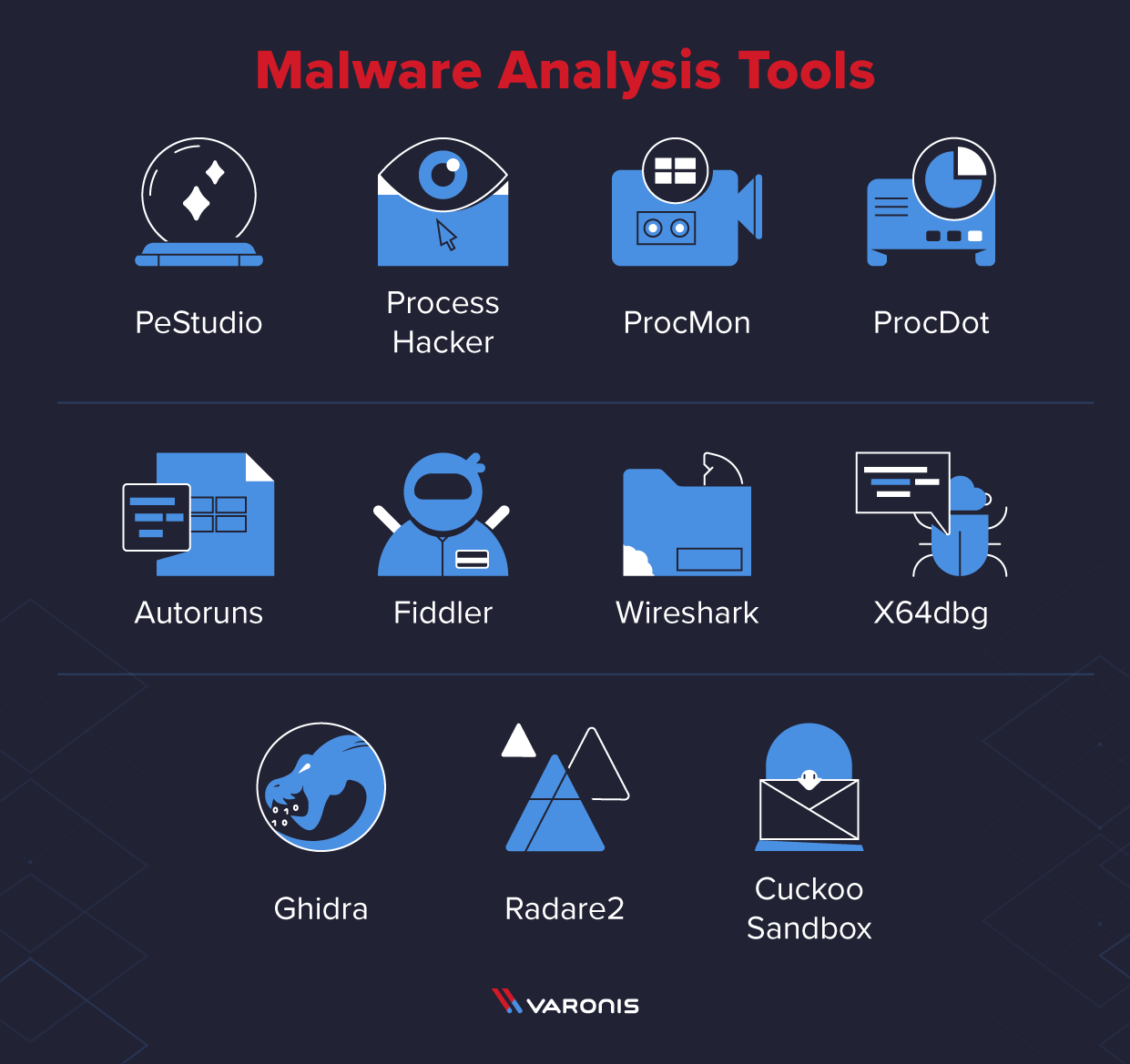
11 Best Malware Analysis Tools and Their Features

Microsoft 365 Alerting - Detect and React to Threats Instantly

Diagram of the malware analysis methodology.

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
 What does your IP address say about you? - CNET30 março 2025
What does your IP address say about you? - CNET30 março 2025 -
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack30 março 2025
-
 Show Your Public IP - Restreamer30 março 2025
Show Your Public IP - Restreamer30 março 2025 -
 Doing “IP Chicken” from the CLI – InfoSec Monkey30 março 2025
Doing “IP Chicken” from the CLI – InfoSec Monkey30 março 2025 -
 Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders30 março 2025
Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders30 março 2025 -
 The Fuck you Tony P Guide to getting around an IP ban!30 março 2025
The Fuck you Tony P Guide to getting around an IP ban!30 março 2025 -
![🔴LIVE] How to know my Local PC IP address?](https://i.ytimg.com/vi/HbDJUHhXKhg/maxresdefault.jpg) 🔴LIVE] How to know my Local PC IP address?30 março 2025
🔴LIVE] How to know my Local PC IP address?30 março 2025 -
SOLVED] Port Forwarding for IP Camera not working30 março 2025
-
GitHub - dogshep-zz/telnetipchicken: A simple telnet server to run geoip and IP chicken30 março 2025
-
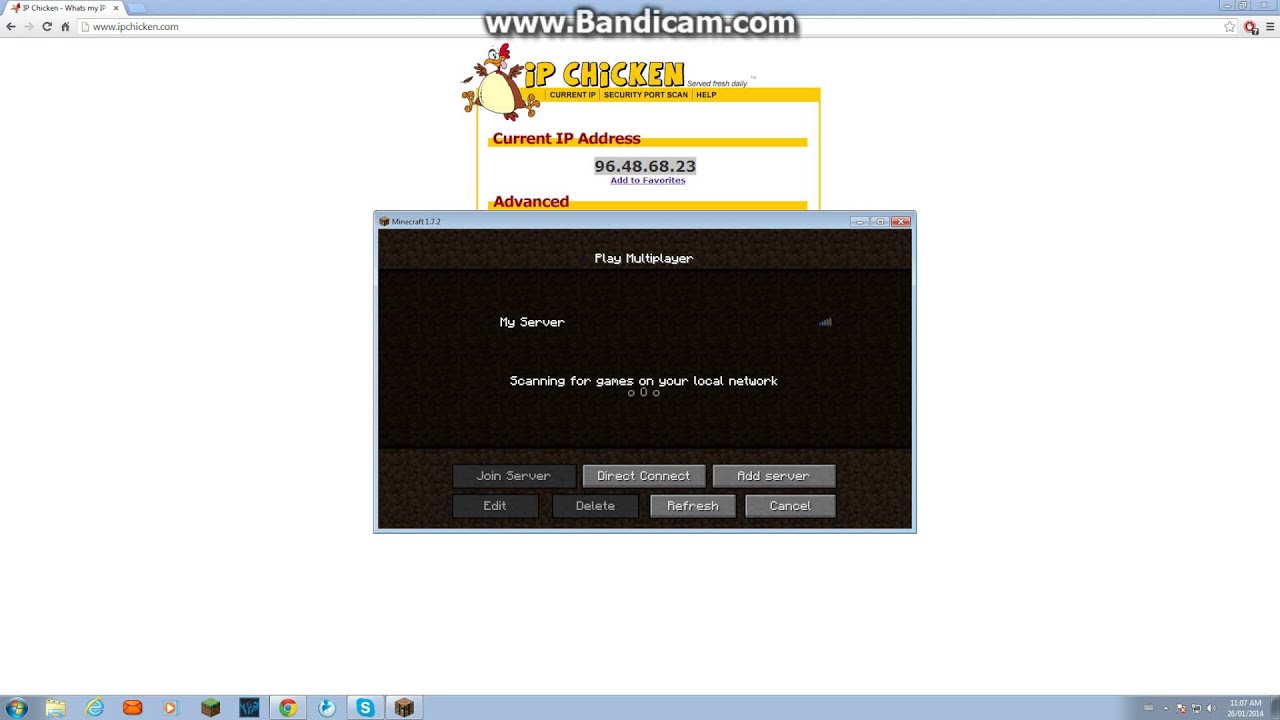 How to use ipchicken to access your minecraft server30 março 2025
How to use ipchicken to access your minecraft server30 março 2025
você pode gostar
-
 Brinquedo Cognitivo Montessori Forma Cor Geométrica Combinação Jogo Memória Sensorial Educativos Infantil30 março 2025
Brinquedo Cognitivo Montessori Forma Cor Geométrica Combinação Jogo Memória Sensorial Educativos Infantil30 março 2025 -
 Em leilão, Corsan é vendida por R$ 4,1 bilhões – Giro de Gravataí30 março 2025
Em leilão, Corsan é vendida por R$ 4,1 bilhões – Giro de Gravataí30 março 2025 -
 Minecraft Mine-Keshi Cobblestone & Wooden Door Block Set30 março 2025
Minecraft Mine-Keshi Cobblestone & Wooden Door Block Set30 março 2025 -
 Android App & Streamer Toolkit30 março 2025
Android App & Streamer Toolkit30 março 2025 -
 Read 100 Man No Inochi No Ue Ni Ore Wa Tatte Iru Chapter 430 março 2025
Read 100 Man No Inochi No Ue Ni Ore Wa Tatte Iru Chapter 430 março 2025 -
 Made a mosaic of Nagisa : r/Clannad30 março 2025
Made a mosaic of Nagisa : r/Clannad30 março 2025 -
 You Don't Need Pokemon GO To Catch Alolan Forms In Pokemon Let's GO Pikachu/Eevee – NintendoSoup30 março 2025
You Don't Need Pokemon GO To Catch Alolan Forms In Pokemon Let's GO Pikachu/Eevee – NintendoSoup30 março 2025 -
 Mahershala Ali's Netflix Film Confirmed To Be Set in the Same30 março 2025
Mahershala Ali's Netflix Film Confirmed To Be Set in the Same30 março 2025 -
 EVENT: Mario Kart Tournament30 março 2025
EVENT: Mario Kart Tournament30 março 2025 -
 New Script: Roblox Ohio Script / Hack - Auto-Farm Infinite Money + Gun Mods : r/Zaptosis30 março 2025
New Script: Roblox Ohio Script / Hack - Auto-Farm Infinite Money + Gun Mods : r/Zaptosis30 março 2025