Malware analysis Malicious activity
Por um escritor misterioso
Last updated 03 abril 2025

Malware Analysis - What is, Benefits & Types (Easily Explained)

Process of traditional signature-based malware detection. [14

Malware leveraging public infrastructure like GitHub on the rise

A basic malware analysis method - ScienceDirect

Outline of malware detection methodology.

Robust Malware Detection Models: Learning From Adversarial Attacks

Remediation and Malware Detection Overview

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis Guide: Types & Tools

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug
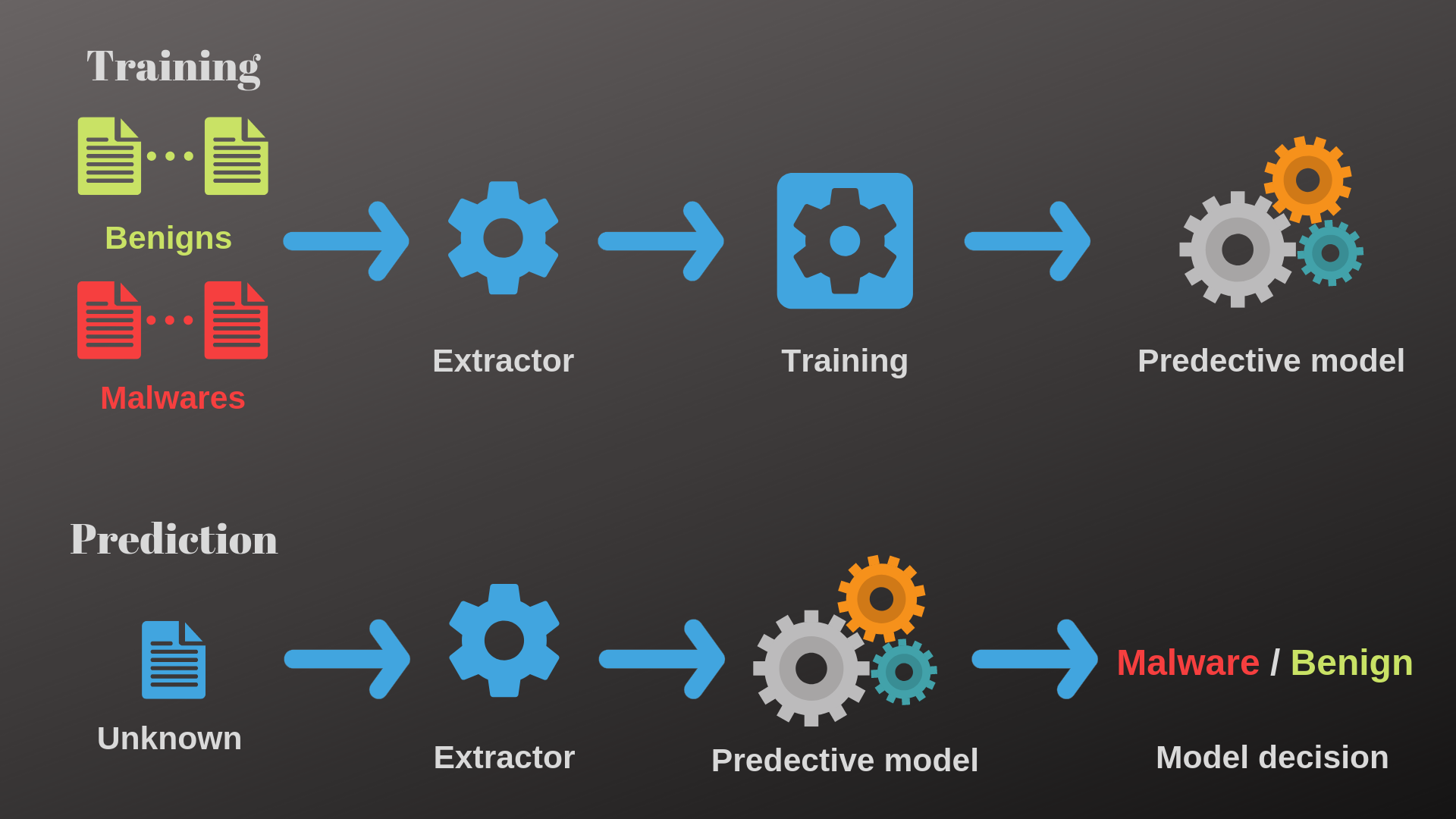
Feature Extraction and Detection of Malwares Using Machine

Behavior-based malware analysis process as conducted by our
Recomendado para você
-
 ScriptPastebin – Roblox Script03 abril 2025
ScriptPastebin – Roblox Script03 abril 2025 -
 Lucky Blocks Battleground Script (2023) - Gaming Pirate03 abril 2025
Lucky Blocks Battleground Script (2023) - Gaming Pirate03 abril 2025 -
![LUCKY BLOCKS Battlegrounds Script Pastebin [SkyHub] - CHEATERMAD](https://cheatermad.com/wp-content/uploads/2022/05/unknown-6-850x530.png) LUCKY BLOCKS Battlegrounds Script Pastebin [SkyHub] - CHEATERMAD03 abril 2025
LUCKY BLOCKS Battlegrounds Script Pastebin [SkyHub] - CHEATERMAD03 abril 2025 -
Buy Hack Roblox page03 abril 2025
-
 The Strongest Battlegrounds Script Pastebin Hacks - December 202303 abril 2025
The Strongest Battlegrounds Script Pastebin Hacks - December 202303 abril 2025 -
death ball roblox script|TikTok Search03 abril 2025
-
 Tripex Scripts03 abril 2025
Tripex Scripts03 abril 2025 -
Blox Hunt Script, PDF, Text03 abril 2025
-
 Millionaire Empire Tycoon script - (Money Farm)03 abril 2025
Millionaire Empire Tycoon script - (Money Farm)03 abril 2025 -
 Universal Script 📌 BUTIF 2 Universal Script Hub — Roblox Scripts03 abril 2025
Universal Script 📌 BUTIF 2 Universal Script Hub — Roblox Scripts03 abril 2025
você pode gostar
-
 Qual é a diferença entre o basquete praticado na NBA e em torneios03 abril 2025
Qual é a diferença entre o basquete praticado na NBA e em torneios03 abril 2025 -
 HURRY* FREE HAIR AND FREE ITEMS NOW IN ROBLOX 2023 🥰😍 - BiliBili03 abril 2025
HURRY* FREE HAIR AND FREE ITEMS NOW IN ROBLOX 2023 🥰😍 - BiliBili03 abril 2025 -
 Watch Liverpool FC target Henrikh Mkhitaryan in action - Liverpool Echo03 abril 2025
Watch Liverpool FC target Henrikh Mkhitaryan in action - Liverpool Echo03 abril 2025 -
 Gtarp Imagens Fotos, vídeos, logotipos, ilustrações e identidade visual no Behance03 abril 2025
Gtarp Imagens Fotos, vídeos, logotipos, ilustrações e identidade visual no Behance03 abril 2025 -
 Erva do Diabo - The Teachings Of Don Juan (Em Portugues do Brasil) : _: Electronics03 abril 2025
Erva do Diabo - The Teachings Of Don Juan (Em Portugues do Brasil) : _: Electronics03 abril 2025 -
 Texas Parks and Wildlife game wardens get new airboat03 abril 2025
Texas Parks and Wildlife game wardens get new airboat03 abril 2025 -
 FORZA HORIZON 5 on XBOX CLOUD GAMING native APP on SAMSUNG TV in03 abril 2025
FORZA HORIZON 5 on XBOX CLOUD GAMING native APP on SAMSUNG TV in03 abril 2025 -
 Key 7010 - Medivia Online Wiki03 abril 2025
Key 7010 - Medivia Online Wiki03 abril 2025 -
 lg-noticias-gra-mio-foot-ball-porto-alegrense-anuncia-ma-rcio-pinto-ramos-como-novo-ceo-do-clube-3441103 abril 2025
lg-noticias-gra-mio-foot-ball-porto-alegrense-anuncia-ma-rcio-pinto-ramos-como-novo-ceo-do-clube-3441103 abril 2025 -
 Pokemon GO'S GREATEST SHINY is here for 3hours ONLY!! #pokemongo #pokemon # lucario #shortvideo03 abril 2025
Pokemon GO'S GREATEST SHINY is here for 3hours ONLY!! #pokemongo #pokemon # lucario #shortvideo03 abril 2025


