Malware analysis Malicious activity
Por um escritor misterioso
Last updated 26 março 2025

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security

Mastering Malware Analysis
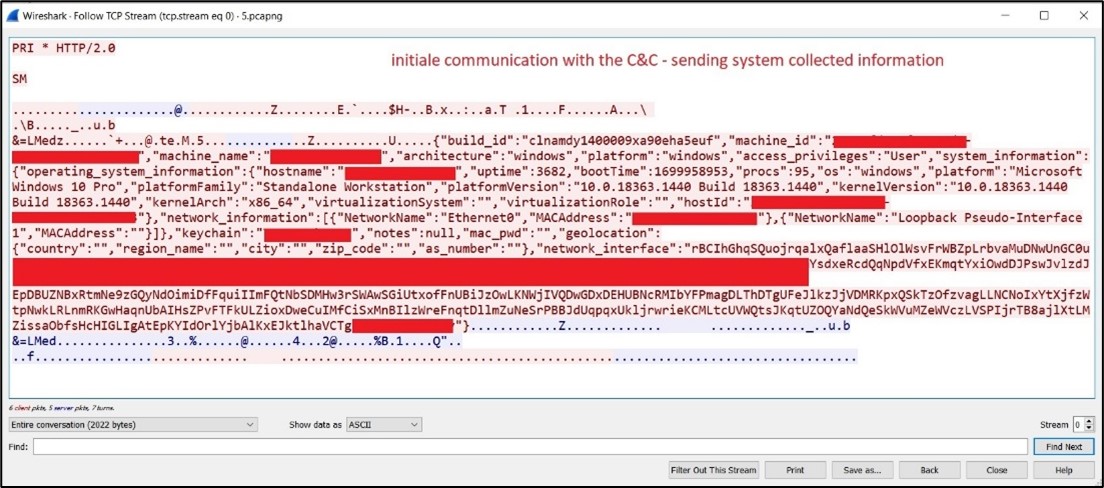
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

What to Include in a Malware Analysis Report

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

What is Malware? Definition, Types, Prevention - TechTarget
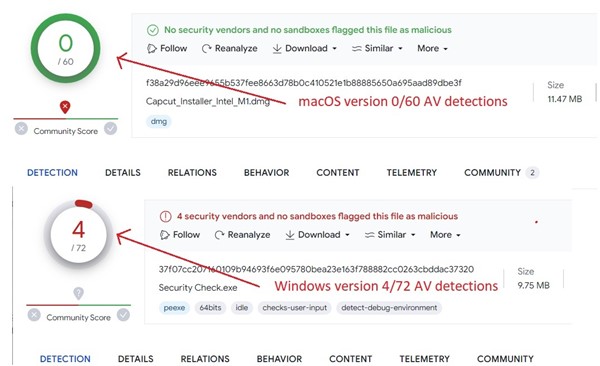
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

AlienVault - Open Threat Exchange

Malware analysis file Malicious activity

Malware Analysis - What is, Benefits & Types (Easily Explained)

Detail procedure of malware analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
Recomendado para você
-
 Make Google Do a Barrel Roll and 6 Other Crazy Tricks!26 março 2025
Make Google Do a Barrel Roll and 6 Other Crazy Tricks!26 março 2025 -
 How to Do a Barrel Roll on Google: 3 Steps (with Pictures)26 março 2025
How to Do a Barrel Roll on Google: 3 Steps (with Pictures)26 março 2025 -
![How to Experience the Google Do A Barrel Roll [2023]](https://hypernia.com/wp-content/uploads/elementor/thumbs/Google-qcml8omivshuwtbowjfsop30aj4snzmp3y9d651s72.png) How to Experience the Google Do A Barrel Roll [2023]26 março 2025
How to Experience the Google Do A Barrel Roll [2023]26 março 2025 -
![Latest*] Google Barrel Roll Trick tips and tricks of google-Do a](https://1.bp.blogspot.com/-4sARYt_pkqw/YLhQthdWCRI/AAAAAAAAHWU/GrchbmHGepwRlXKFxIzTugh1b8d013XHACNcBGAsYHQ/s1280/Do_a_Barrel_Roll_Trick_google.jpg) Latest*] Google Barrel Roll Trick tips and tricks of google-Do a26 março 2025
Latest*] Google Barrel Roll Trick tips and tricks of google-Do a26 março 2025 -
 Why Google Do a Barrel Roll on Type Barrel Roll?26 março 2025
Why Google Do a Barrel Roll on Type Barrel Roll?26 março 2025 -
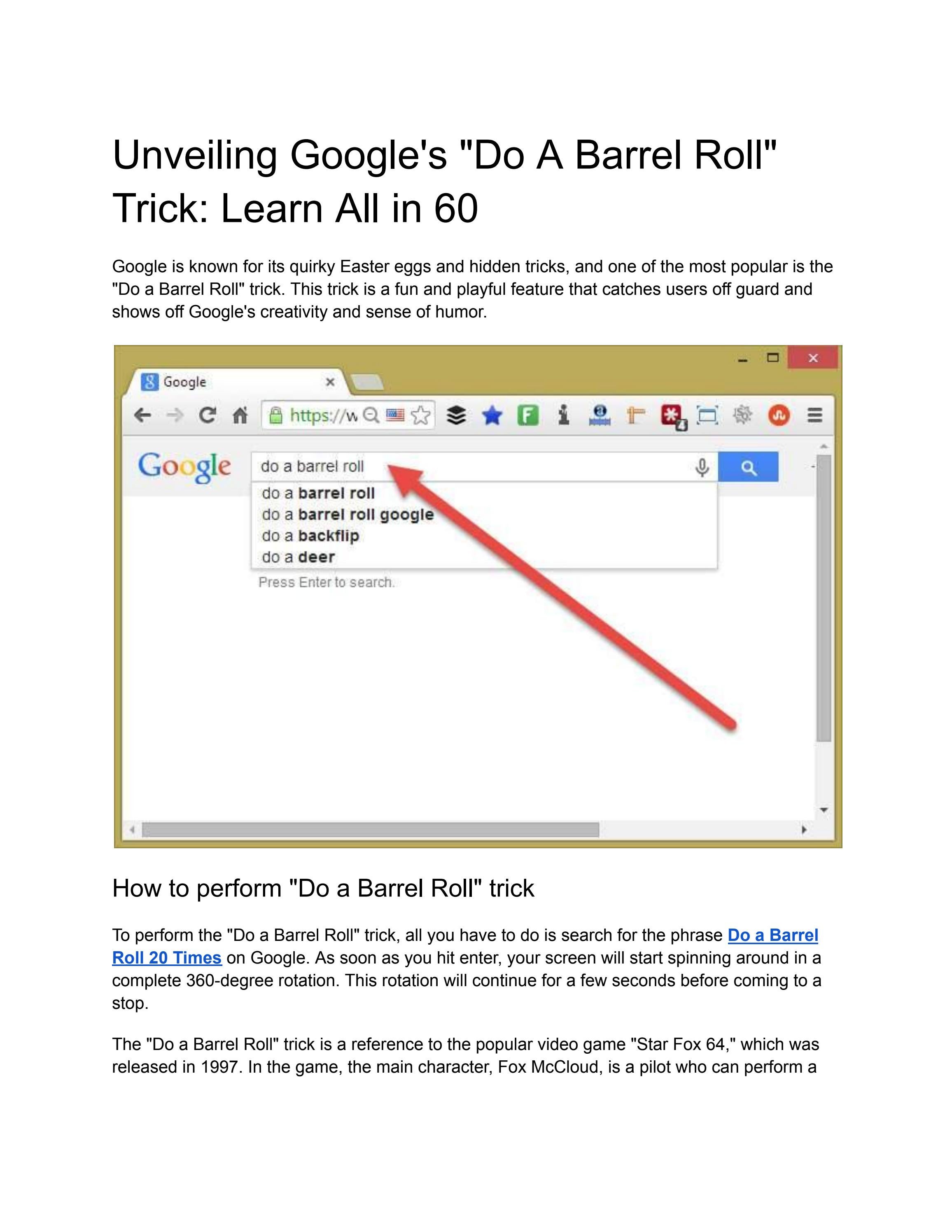 Unveiling Google's Do A Barrel Roll Trick: Learn All in 60 by26 março 2025
Unveiling Google's Do A Barrel Roll Trick: Learn All in 60 by26 março 2025 -
 New do a barrel roll 20 times Quotes, Status, Photo, Video26 março 2025
New do a barrel roll 20 times Quotes, Status, Photo, Video26 março 2025 -
 Friends Blog: Google Do a Barrel Rol Tricks26 março 2025
Friends Blog: Google Do a Barrel Rol Tricks26 março 2025 -
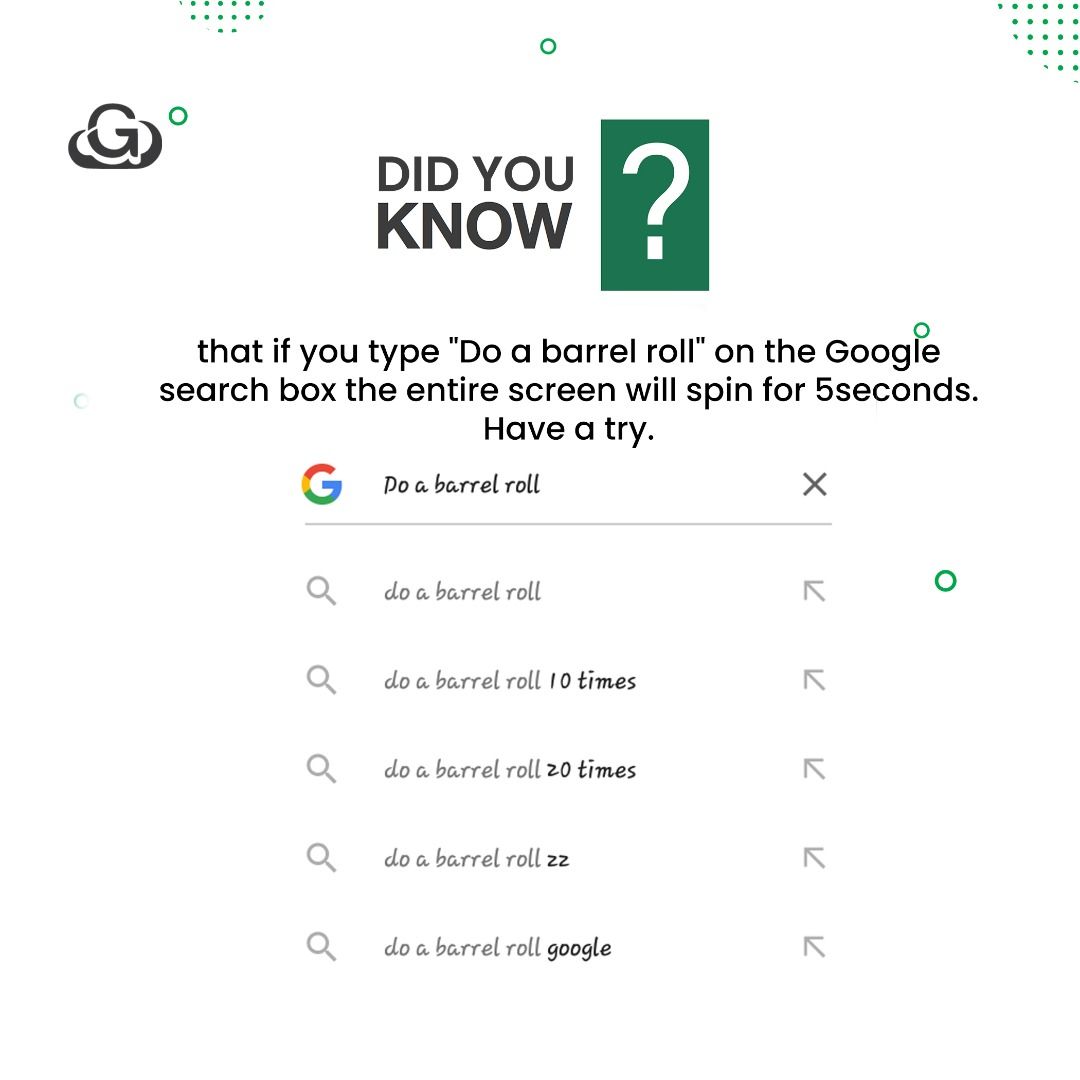 GigaLayer on X: Have a try. / X26 março 2025
GigaLayer on X: Have a try. / X26 março 2025 -
 Google's hidden treasures - The Digital Studios26 março 2025
Google's hidden treasures - The Digital Studios26 março 2025
você pode gostar
-
 Grand Theft Auto IV: Enchanced Edition, Idea Wiki26 março 2025
Grand Theft Auto IV: Enchanced Edition, Idea Wiki26 março 2025 -
 reference anime girl with hair - Anime Bases .INFO26 março 2025
reference anime girl with hair - Anime Bases .INFO26 março 2025 -
Familia Nakamura26 março 2025
-
 Character Maker for Dragon Ball Super & Z26 março 2025
Character Maker for Dragon Ball Super & Z26 março 2025 -
 What Is The 'My Dog Stepped On A Bee' Meme?26 março 2025
What Is The 'My Dog Stepped On A Bee' Meme?26 março 2025 -
 Sonic the Hedgehog on Minecraft Xbox 360 Edition by tjevo9 on DeviantArt26 março 2025
Sonic the Hedgehog on Minecraft Xbox 360 Edition by tjevo9 on DeviantArt26 março 2025 -
 Pokemon Godzilla earth 3 126 março 2025
Pokemon Godzilla earth 3 126 março 2025 -
 11 Quotes About Learning From Your Mistakes26 março 2025
11 Quotes About Learning From Your Mistakes26 março 2025 -
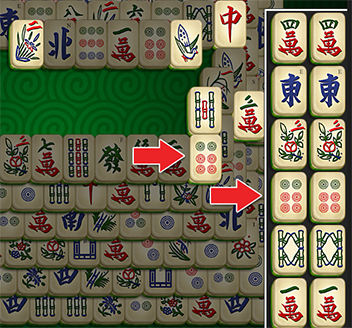 Tips & Tricks in Playing Mahjong26 março 2025
Tips & Tricks in Playing Mahjong26 março 2025 -
 Home · AlphaZero26 março 2025
Home · AlphaZero26 março 2025
