Malware analysis Malicious activity
Por um escritor misterioso
Last updated 29 março 2025

Malware Analysis: Steps & Examples - CrowdStrike

PDF] Automated Malware Analysis using Python
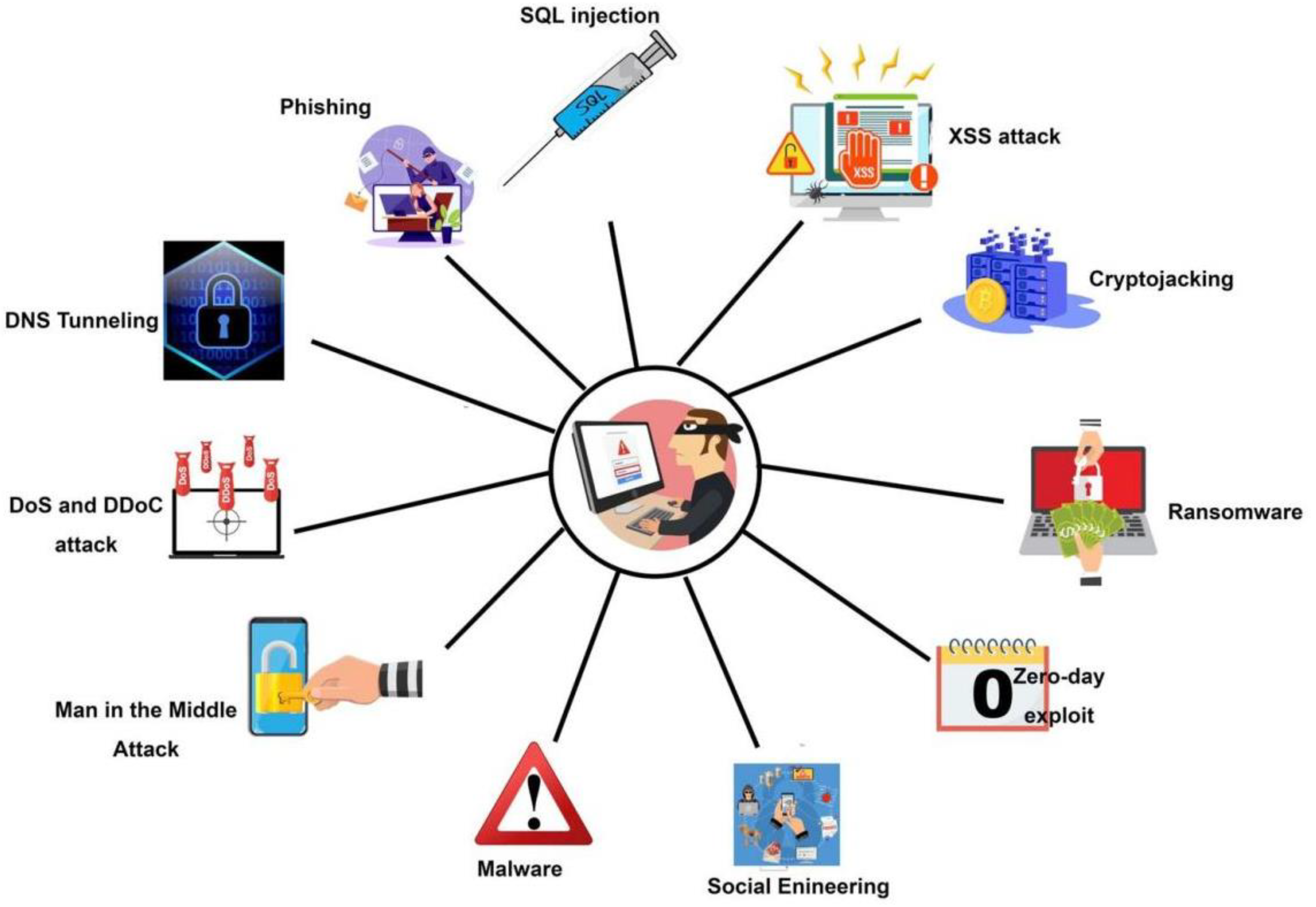
Symmetry, Free Full-Text

Antivirus software - Wikipedia

Malware analysis index.html Malicious activity

A detailed analysis of the Menorah malware used by APT34
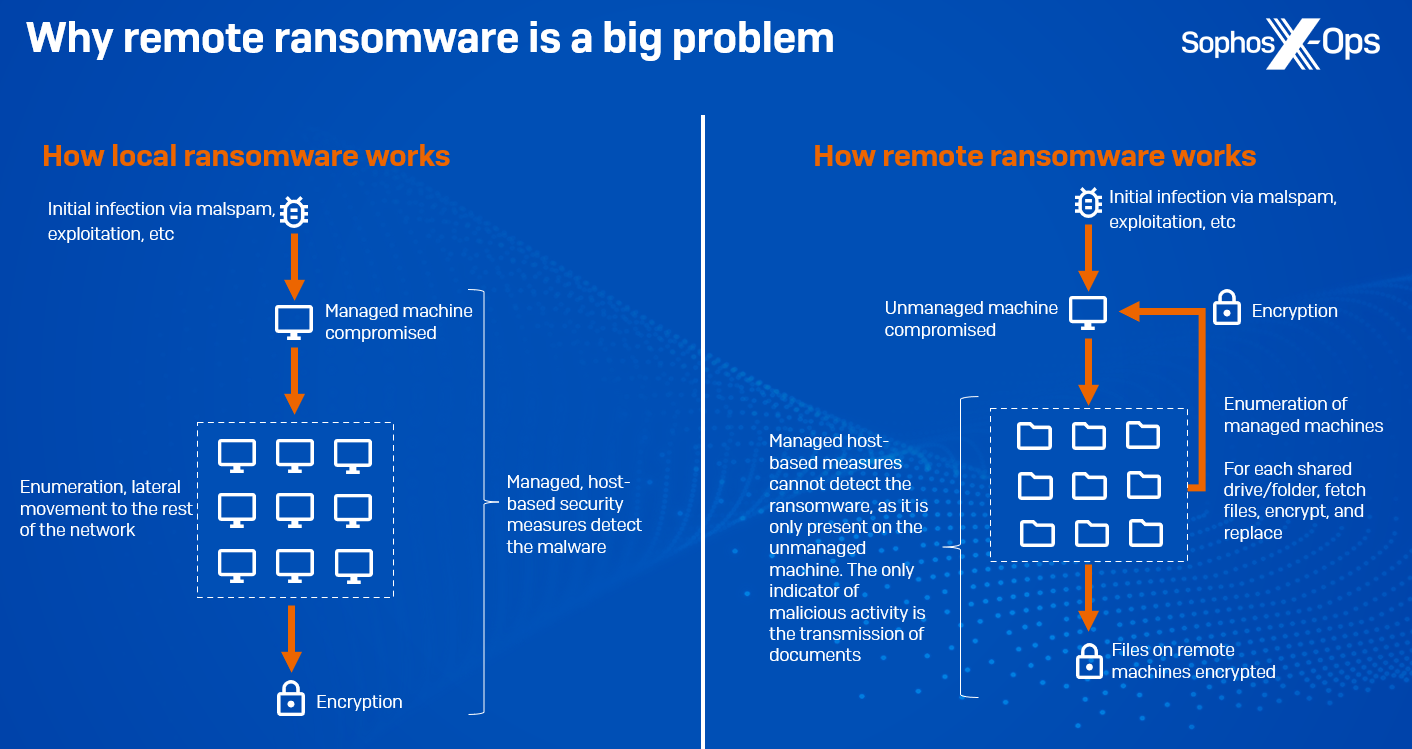
CryptoGuard: An asymmetric approach to the ransomware battle
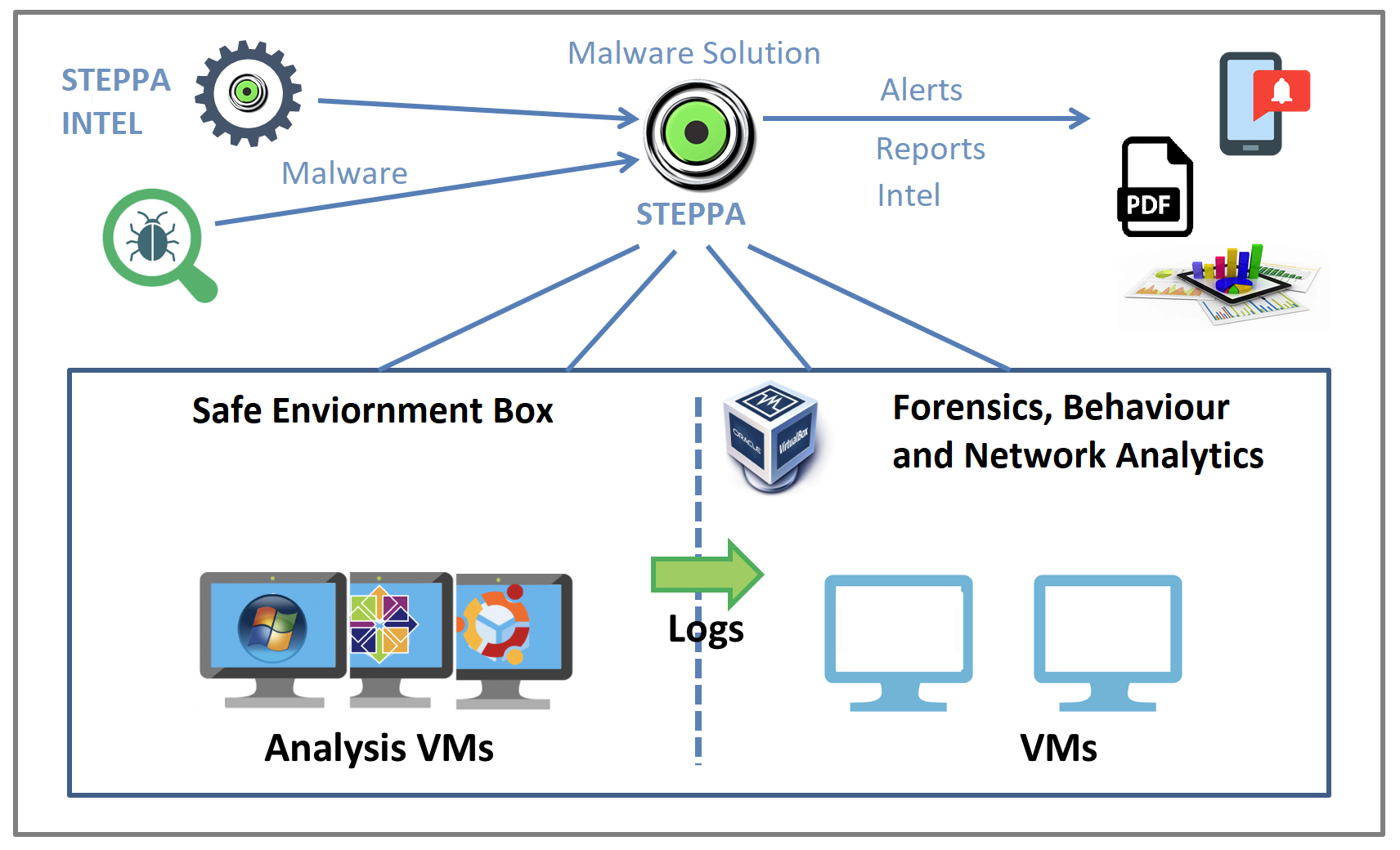
Malware Analysis Solution: Analyze, Detect, and Protect

A classification of malware detection techniques.

Cybersecurity Search Engine
Malware analysis 009E9015BDEF9F869B5F15A526D9A1B1 Malicious

Process of traditional signature-based malware detection. [14

PDF] Basic survey on Malware Analysis, Tools and Techniques
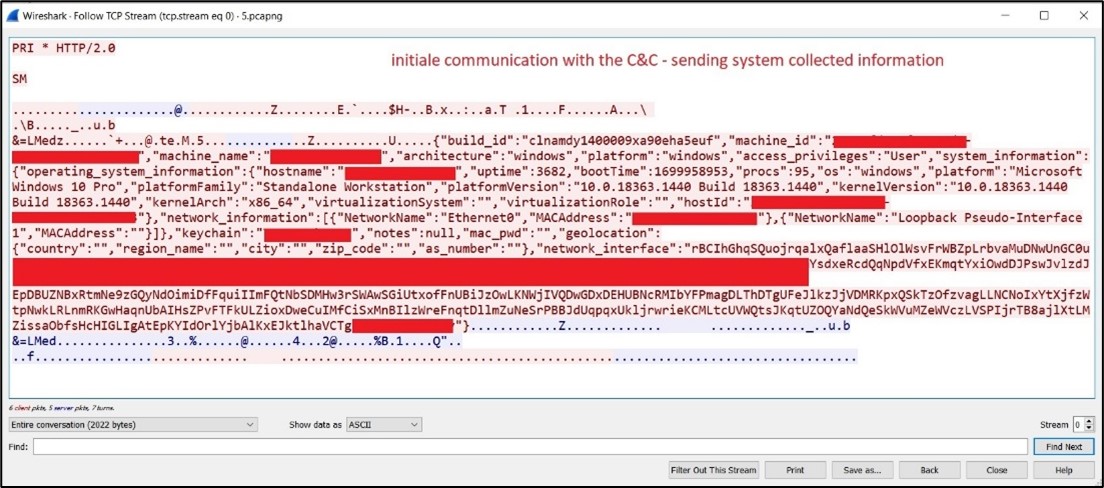
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
Recomendado para você
-
 Roblox Executor Patched, Latest Bypass Byfron29 março 2025
Roblox Executor Patched, Latest Bypass Byfron29 março 2025 -
 Electron Executor 2023, Free Roblox Script Menu29 março 2025
Electron Executor 2023, Free Roblox Script Menu29 março 2025 -
Roblox Test Sites29 março 2025
-
Roblox web executor 2023 november|TikTok Search29 março 2025
-
 Roblox Scripts - The best website for Roblox Scripts & Executors!29 março 2025
Roblox Scripts - The best website for Roblox Scripts & Executors!29 março 2025 -
 Release, Kronos v4, More Powerful Then Fluxus, #1 Keyless Executor29 março 2025
Release, Kronos v4, More Powerful Then Fluxus, #1 Keyless Executor29 março 2025 -
 Get Ahead in Blox Fruits with Hoho Hub Script: Features, Safety29 março 2025
Get Ahead in Blox Fruits with Hoho Hub Script: Features, Safety29 março 2025 -
 Release, Kronos v4, More Powerful Then Fluxus29 março 2025
Release, Kronos v4, More Powerful Then Fluxus29 março 2025 -
 NEW) UNDETECTABLE Roblox Executor Nezur FREE! (Works Web & Microsoft Version)29 março 2025
NEW) UNDETECTABLE Roblox Executor Nezur FREE! (Works Web & Microsoft Version)29 março 2025 -
 TUTORIAL - ROBLOX EXECUTOR 2023 WEB VERSION / BYFRON BYPASS UPDATE29 março 2025
TUTORIAL - ROBLOX EXECUTOR 2023 WEB VERSION / BYFRON BYPASS UPDATE29 março 2025
você pode gostar
-
 Papel de parede : Anime naruto, Akatsuki, Uchiha Itachi, boruto 1600x900 - MariShiny - 1953305 - Papel de parede para pc - WallHere29 março 2025
Papel de parede : Anime naruto, Akatsuki, Uchiha Itachi, boruto 1600x900 - MariShiny - 1953305 - Papel de parede para pc - WallHere29 março 2025 -
 Jogo de sinuca online: conheça os melhores títulos do gênero29 março 2025
Jogo de sinuca online: conheça os melhores títulos do gênero29 março 2025 -
 How to Write A Check: Fill Out A Check29 março 2025
How to Write A Check: Fill Out A Check29 março 2025 -
 14 FREE ITEMS FROM JUST THE LAST 2 WEEKS IN ROBLOX - Get Them While You Can!29 março 2025
14 FREE ITEMS FROM JUST THE LAST 2 WEEKS IN ROBLOX - Get Them While You Can!29 março 2025 -
 NETFLIX CONFIRMA O FIM DO COMPARTILHAMENTO DE CONTAS SEM CUSTO NOS EUA - Soul Brasil Magazine29 março 2025
NETFLIX CONFIRMA O FIM DO COMPARTILHAMENTO DE CONTAS SEM CUSTO NOS EUA - Soul Brasil Magazine29 março 2025 -
 New Small Town Monsters Documentary 'On the Trail of Bigfoot: Last Frontier' Hits 202329 março 2025
New Small Town Monsters Documentary 'On the Trail of Bigfoot: Last Frontier' Hits 202329 março 2025 -
 Jogo Blood Bowl 2 PS4 NOVO - Ri Happy29 março 2025
Jogo Blood Bowl 2 PS4 NOVO - Ri Happy29 março 2025 -
 waveigl on X: Live on!!! RT+COMENT+LIKE=SORTEIO Sawed-Off The Kraken / X29 março 2025
waveigl on X: Live on!!! RT+COMENT+LIKE=SORTEIO Sawed-Off The Kraken / X29 março 2025 -
 What Differ Facebook Metaverse From Microsoft Metaverse?29 março 2025
What Differ Facebook Metaverse From Microsoft Metaverse?29 março 2025 -
 Aussie Trolling Tips29 março 2025
Aussie Trolling Tips29 março 2025
