Malware analysis Malicious activity
Por um escritor misterioso
Last updated 30 março 2025

StopRansomware: Rhysida Ransomware

How to Remove Windows Defender Security Warning Scam

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging
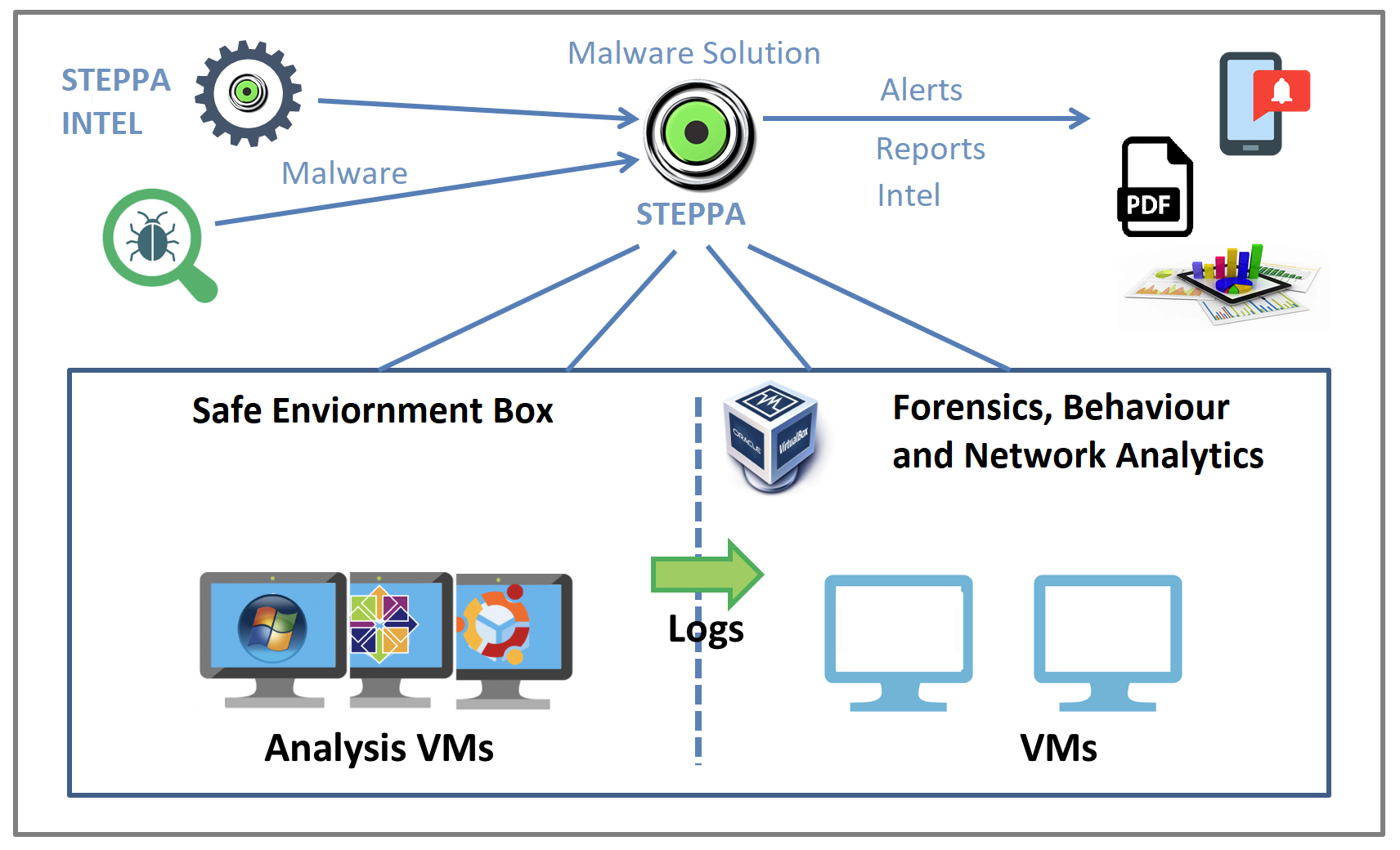
Malware Analysis Solution: Analyze, Detect, and Protect

GitHub - mesquidar/ForensicsTools: A list of free and open

Playbook of the Week: Malware Investigation and Response - Palo

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis mykey_.rar Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

ReversingLabs Malware Lab: Detect, classify, analyze, and respond

Top 10 Types of Information Security Threats for IT Teams
Recomendado para você
-
0505 Pdf Coffee Connoiseur Cookbook : Free Download, Borrow, and Streaming : Internet Archive30 março 2025
-
PDF Coffee, PDF, Microcomputer Software30 março 2025
-
![Stream episode Download Book [PDF] Coffee at The Beach House Hotel by Bryantdominguez podcast](https://i1.sndcdn.com/artworks-JvULsU5McFRwOVG6-l5SG7w-t500x500.jpg) Stream episode Download Book [PDF] Coffee at The Beach House Hotel by Bryantdominguez podcast30 março 2025
Stream episode Download Book [PDF] Coffee at The Beach House Hotel by Bryantdominguez podcast30 março 2025 -
 Coffee Lover SVG PNG JPG Pdf Coffee Quote Coffee Digital - Norway30 março 2025
Coffee Lover SVG PNG JPG Pdf Coffee Quote Coffee Digital - Norway30 março 2025 -
 pdfcoffee.com_skyfall-adele-pdf-free Pages 1-7 - Flip PDF Download30 março 2025
pdfcoffee.com_skyfall-adele-pdf-free Pages 1-7 - Flip PDF Download30 março 2025 -
 Printable Mug Cozy Template Cup Cozy Printable PDF Coffee30 março 2025
Printable Mug Cozy Template Cup Cozy Printable PDF Coffee30 março 2025 -
 cross stitch pattern PDF Coffee and Plant Cart30 março 2025
cross stitch pattern PDF Coffee and Plant Cart30 março 2025 -
 Pdfcoffee - Livro - Bioprocess Engineering Shuler Kargi Solution Manual As recognized, adventure as - Studocu30 março 2025
Pdfcoffee - Livro - Bioprocess Engineering Shuler Kargi Solution Manual As recognized, adventure as - Studocu30 março 2025 -
 Printable Mug Cozy Template Cup Cozy Printable PDF Coffee - Sweden30 março 2025
Printable Mug Cozy Template Cup Cozy Printable PDF Coffee - Sweden30 março 2025 -
 Coffee the Essence of Life T Shirt Graphic by RR DESIGN STUDIO · Creative Fabrica30 março 2025
Coffee the Essence of Life T Shirt Graphic by RR DESIGN STUDIO · Creative Fabrica30 março 2025
você pode gostar
-
 Desenhos de árvores de Natal para colorir e pintar30 março 2025
Desenhos de árvores de Natal para colorir e pintar30 março 2025 -
 Vampire: The Masquerade - Bloodhunt, development has ended30 março 2025
Vampire: The Masquerade - Bloodhunt, development has ended30 março 2025 -
 Kappei Yamaguchi - IMDb30 março 2025
Kappei Yamaguchi - IMDb30 março 2025 -
Cat Lover30 março 2025
-
 Bifes de perú estufados com legumes - Receita Petitchef30 março 2025
Bifes de perú estufados com legumes - Receita Petitchef30 março 2025 -
 AnimesFlix – Assistir Animes Onlines Grátis30 março 2025
AnimesFlix – Assistir Animes Onlines Grátis30 março 2025 -
 G1 - The Pirate Bay adota seis novos endereços após perder '.se30 março 2025
G1 - The Pirate Bay adota seis novos endereços após perder '.se30 março 2025 -
 COMO CONSEGUIR FICAR RICO DE FRUTAS MÍTICAS, DOUGH SEM ROBUX NO BLOX FRUITS (ROBLOX)30 março 2025
COMO CONSEGUIR FICAR RICO DE FRUTAS MÍTICAS, DOUGH SEM ROBUX NO BLOX FRUITS (ROBLOX)30 março 2025 -
 moldes de roupas de bonecas para imprimir - Pesquisa do Google30 março 2025
moldes de roupas de bonecas para imprimir - Pesquisa do Google30 março 2025 -
 Relógio BEN10 digital azul bebê com luzes E musica infantil em30 março 2025
Relógio BEN10 digital azul bebê com luzes E musica infantil em30 março 2025

