Malware analysis
Por um escritor misterioso
Last updated 24 março 2025
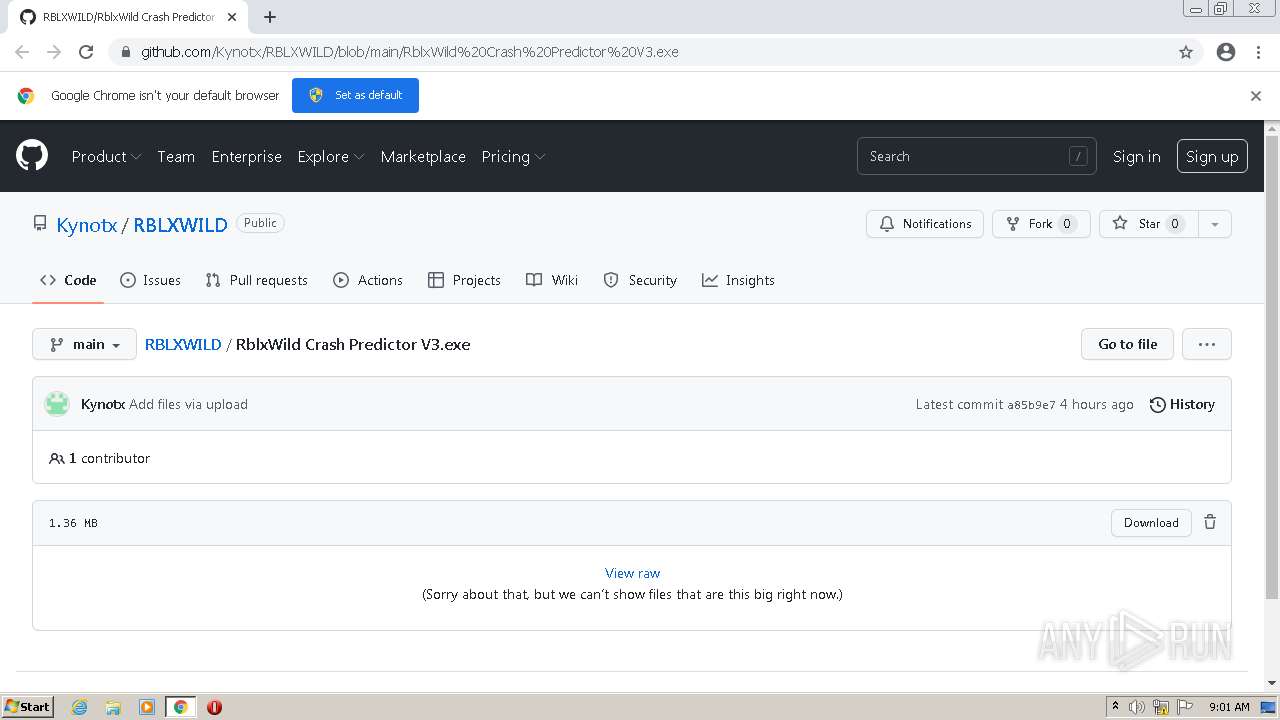

The Role of Malware Analysis in Cybersecurity

Detail procedure of malware analysis
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+

Advanced Malware Detection – Signatures vs. Behavior Analysis - Cyber Defense Magazine

Learn to Analyze Malware - (The Malware Analysis Project 101)

Malware Analysis: Steps & Examples - CrowdStrike

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

How To Set Up Malware Analysis Environment? - The Sec Master
11 Best Malware Analysis Tools and Their Features

Malware Analysis Explained - 's Cybersecurity Blog

GPT's Journey into Malware Analysis - Check Point Blog

What Is Dynamic Malware Analysis?
Highlight, take notes, and search in the book

Malware Analysis Techniques: Tricks for the triage of adversarial software
Automated Malware Analysis with Low-Code Security Automation
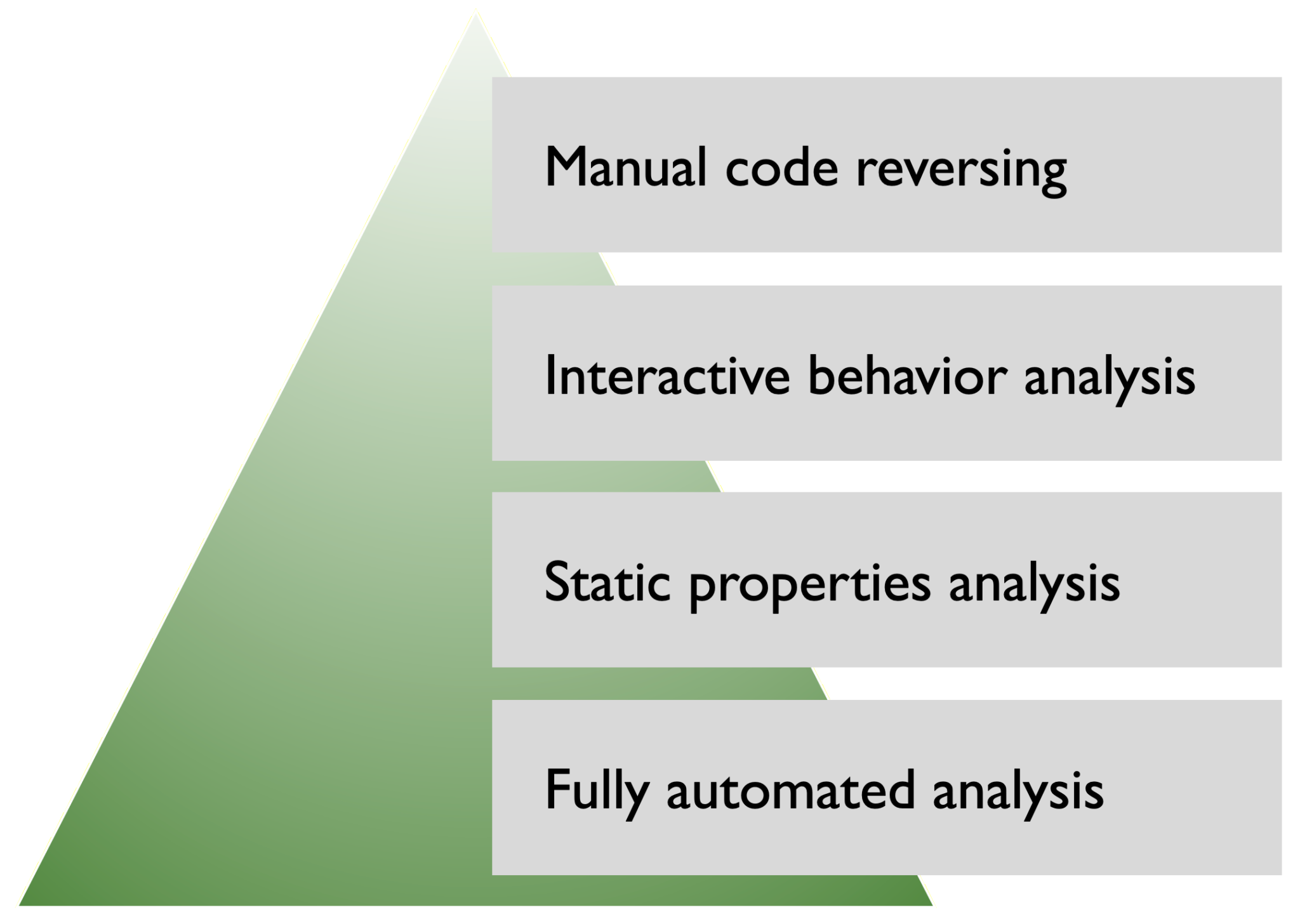
How You Can Start Learning Malware Analysis
Recomendado para você
-
 RBLXWILD - CRASH FAIRNESS - Replit24 março 2025
RBLXWILD - CRASH FAIRNESS - Replit24 março 2025 -
 My Guide To RBLXWild Mines24 março 2025
My Guide To RBLXWild Mines24 março 2025 -
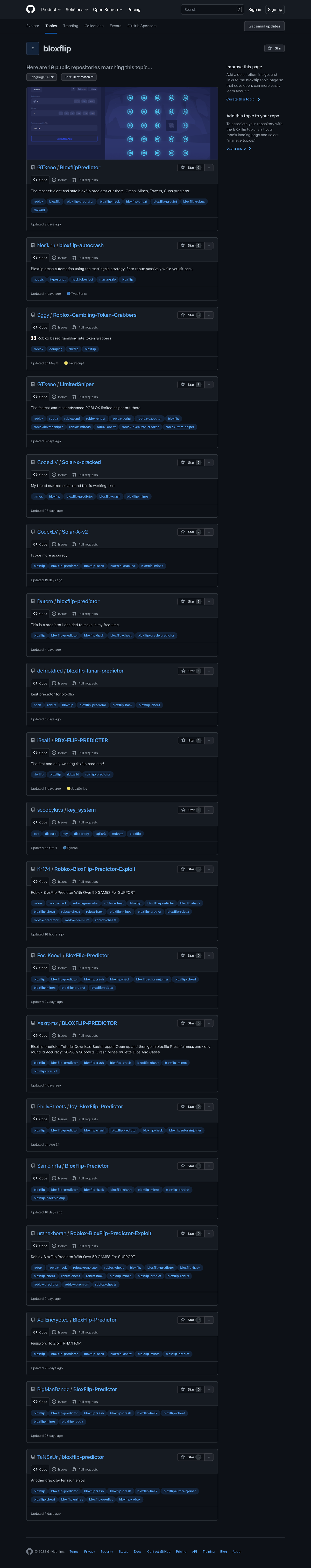 Bloxflip · Git Hub Topics · Git Hub - # bloxflip Here are 1924 março 2025
Bloxflip · Git Hub Topics · Git Hub - # bloxflip Here are 1924 março 2025 -
 Guest Post by ItsBitcoinWorld: Roblox Accused of Enabling Minor Gambling with Robux: Lawsuit Unveils Controversy24 março 2025
Guest Post by ItsBitcoinWorld: Roblox Accused of Enabling Minor Gambling with Robux: Lawsuit Unveils Controversy24 março 2025 -
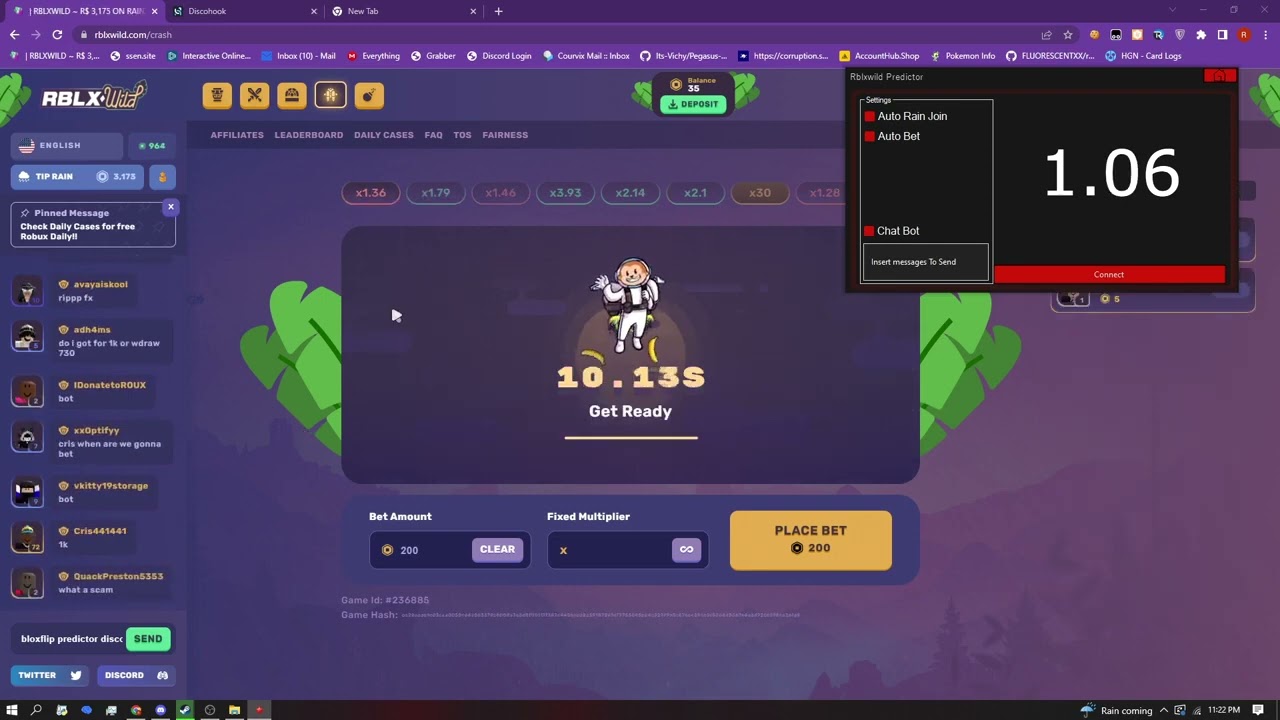 Rblxwild Star Predictor Showcase (ALWAYS WIN CRASH!?!?!)24 março 2025
Rblxwild Star Predictor Showcase (ALWAYS WIN CRASH!?!?!)24 março 2025 -
Best rblxwild predictor|TikTok Search24 março 2025
-
Rblxwild mines predictor|TikTok Search24 março 2025
-
 RBLX WILD CRASH PREDICTOR SHOWCASE! (Always win crash?!)RBLX WILD24 março 2025
RBLX WILD CRASH PREDICTOR SHOWCASE! (Always win crash?!)RBLX WILD24 março 2025 -
 Rblxwild Mines Predictor *Update new* Test Discord Server API v124 março 2025
Rblxwild Mines Predictor *Update new* Test Discord Server API v124 março 2025 -
 ⭐BEST OP + FREE + PREMIUM + LEGIT BLOXFLIP PREDICTOR💸24 março 2025
⭐BEST OP + FREE + PREMIUM + LEGIT BLOXFLIP PREDICTOR💸24 março 2025
você pode gostar
-
 How to Draw Full Body Poses in Procreate (anime art style)24 março 2025
How to Draw Full Body Poses in Procreate (anime art style)24 março 2025 -
Portal R7.com on X: Fim de jogo! Palmeiras reverte a vantagem tricolor, faz 4x0 e conquista o título do Campeonato Paulista ⚽️🏆 #FinalPaulistãoNaRecord / X24 março 2025
-
 News - July, 201524 março 2025
News - July, 201524 março 2025 -
Stands (Habilidades) - №13: Dirty Deeds Done Dirt Cheap D4C24 março 2025
-
 Vetores de Gótica Inscrição Em Inglês Tipo De Letra Para Tatuagem Nunca Desista A Frase É Isolada Em Um Fundo Preto Caligrafia E Lettering Letras De Ouro Logotipo Para Tshirt Slogan Lema24 março 2025
Vetores de Gótica Inscrição Em Inglês Tipo De Letra Para Tatuagem Nunca Desista A Frase É Isolada Em Um Fundo Preto Caligrafia E Lettering Letras De Ouro Logotipo Para Tshirt Slogan Lema24 março 2025 -
 Welcome to your place for Otakus — Date A Live IV DanMachi Collab24 março 2025
Welcome to your place for Otakus — Date A Live IV DanMachi Collab24 março 2025 -
 Abadá Capoeira Búzios Graduado Gafanhoto: Jogos Femininos Abada24 março 2025
Abadá Capoeira Búzios Graduado Gafanhoto: Jogos Femininos Abada24 março 2025 -
Steam Workshop::Sonic 1 Boomed24 março 2025
-
 BOYWITHUKE RELEASES NEW SINGLE “MIGRAINE” TODAY - Umusic24 março 2025
BOYWITHUKE RELEASES NEW SINGLE “MIGRAINE” TODAY - Umusic24 março 2025 -
🔥FOLLOW 4 MORE ANIME CONTENT🔥 * ANIME: My Home Hero Where: TBD24 março 2025






