Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 11 abril 2025

This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Blind SSRF with Shellshock exploitation (Video Solution)

Linux Exploitation – Shellshock exploit and privilege escalation

TryHackMe Advent of Cyber 2 [2020]
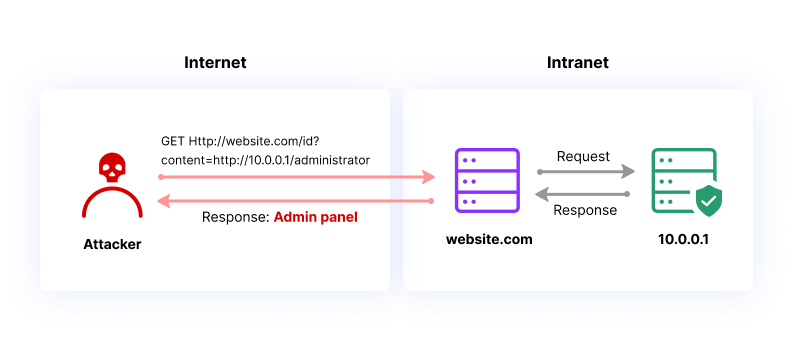
Server-Side Request Forgery (SSRF), Common Attacks & Risks

Shell Shock Lab

PortSwigger - All Labs - Web Security Academy, PDF
A Glossary of Blind SSRF Chains – Assetnote

Free Cybersecurity & Hacking Training
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
Server side request forgery vulnerabilities (SSRF) - Các lỗ hổng
Recomendado para você
-
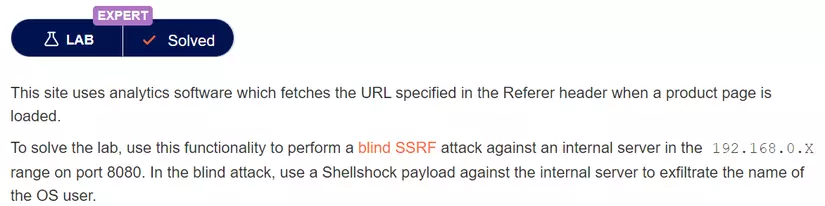
 Shellshock (software bug) - Wikipedia11 abril 2025
Shellshock (software bug) - Wikipedia11 abril 2025 -
Buy ShellShock Live (PC) - Steam Gift - GLOBAL - Cheap - !11 abril 2025
-
 AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems11 abril 2025
AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems11 abril 2025 -
 Shellshock Security Flaw - What is it and how it affects everyone - My Blog11 abril 2025
Shellshock Security Flaw - What is it and how it affects everyone - My Blog11 abril 2025 -
 Kali Linux Web Penetration Testing Cookbook11 abril 2025
Kali Linux Web Penetration Testing Cookbook11 abril 2025 -
 Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog11 abril 2025
Tenable Issues Shellshock Detection Plugins, Wizard, Dashboard - Blog11 abril 2025 -
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek11 abril 2025
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek11 abril 2025 -
 A Georgia election server was vulnerable to Shellshock and may have been hacked11 abril 2025
A Georgia election server was vulnerable to Shellshock and may have been hacked11 abril 2025 -
 Hackers 'already using Shellshock bug to attack victims11 abril 2025
Hackers 'already using Shellshock bug to attack victims11 abril 2025 -
 Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo11 abril 2025
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo11 abril 2025
você pode gostar
-
 Bispos da Diocese – MITRA DIOCESANA DE JACAREZINHO11 abril 2025
Bispos da Diocese – MITRA DIOCESANA DE JACAREZINHO11 abril 2025 -
 💫🌿🌱 — Mbti, inspired by people I know11 abril 2025
💫🌿🌱 — Mbti, inspired by people I know11 abril 2025 -
 Classroom of the Elite Vol.1-12 Comics Set Japanese Ver Manga11 abril 2025
Classroom of the Elite Vol.1-12 Comics Set Japanese Ver Manga11 abril 2025 -
 my name is John Marston at Red Dead Redemption 2 Nexus - Mods and community11 abril 2025
my name is John Marston at Red Dead Redemption 2 Nexus - Mods and community11 abril 2025 -
 Hell's Paradise: motivações e crescimento de Gabimaru11 abril 2025
Hell's Paradise: motivações e crescimento de Gabimaru11 abril 2025 -
 Lista de jogos do Xbox 360 que funcionam no Xbox One - Atualizada11 abril 2025
Lista de jogos do Xbox 360 que funcionam no Xbox One - Atualizada11 abril 2025 -
 Livro O Livro De Colorir Luccas E Gi Na Fazenda de Luccas Neto (Português)11 abril 2025
Livro O Livro De Colorir Luccas E Gi Na Fazenda de Luccas Neto (Português)11 abril 2025 -
Crazy Shopping - Apps on Google Play11 abril 2025
-
 Aprendendo com Música11 abril 2025
Aprendendo com Música11 abril 2025 -
 Simulador de direção para ônibus é mais divertido que videogame de última geração - Carros e motos - Extra Online11 abril 2025
Simulador de direção para ônibus é mais divertido que videogame de última geração - Carros e motos - Extra Online11 abril 2025