Jen Easterly🛡️ (@CISAJen) / X
Por um escritor misterioso
Last updated 25 março 2025


Jen Easterly

What a Chinese invasion of Taiwan could look like in cyberspace - The Washington Post

White House Issues Cybersecurity Guidelines for Agencies, Contractors

Cybersecurity, nondefense research may face cuts in debt deal - Roll Call

SEC, CISA push dueling cyberattack incident reporting rules - Protocol

Cyber's role in the Ukraine-Russia crisis remains unclear - The Washington Post

Cyber Attack - GZERO Media

Jen Easterly🛡️ (@CISAJen) / X

Jen Easterly🛡️ on X: Spent the day @KentState Trumbull meeting w/@RepDaveJoyce & local business leaders to discuss @CISAgov's free cybersecurity services. Big thanks to our great partners in Ohio for hosting us

Jen Easterly🛡️ on X: 🇺🇸🇺🇦Such a privilege to meet with our incredible Ukrainian colleagues yesterday to discuss further deepening our cybersecurity collaboration with @dsszzi. Super grateful for the partnership & looking forward
Cybersecurity and Infrastructure Security Agency Director at Government Tech Summit
Recomendado para você
-
 All The Races In Roblox Project New World, Ranked25 março 2025
All The Races In Roblox Project New World, Ranked25 março 2025 -
Elections in digital times: a guide for electoral practitioners25 março 2025
-
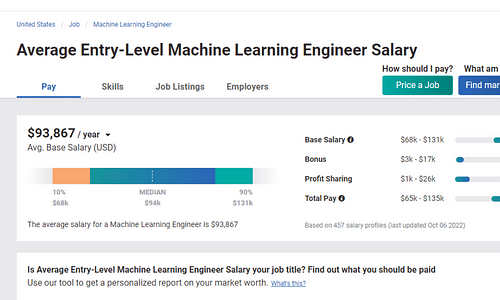 Machine Learning Engineer Salary-The Ultimate Guide for 202325 março 2025
Machine Learning Engineer Salary-The Ultimate Guide for 202325 março 2025 -
 06 New Harmony Project - City Council - City of Davis25 março 2025
06 New Harmony Project - City Council - City of Davis25 março 2025 -
 Will Rogers World Airport - Wikipedia25 março 2025
Will Rogers World Airport - Wikipedia25 março 2025 -
 News/Media Archive - Skender25 março 2025
News/Media Archive - Skender25 março 2025 -
 HCB Magazine May 2019 by Chemical Watch - Issuu25 março 2025
HCB Magazine May 2019 by Chemical Watch - Issuu25 março 2025 -
 E3 2021: Does Xbox and Bethesda's impressive showcase show Microsoft's big gaming bet is paying off?25 março 2025
E3 2021: Does Xbox and Bethesda's impressive showcase show Microsoft's big gaming bet is paying off?25 março 2025 -
Combined Experimental and Mechanoelastic Modeling Studies on the Low-Spin Stabilized Mixed Crystals of 3D Oxalate-Based Coordination Materials25 março 2025
-
 Project New World CODES: veja códigos pra resgatar (outubro 2023) - Mobile Gamer25 março 2025
Project New World CODES: veja códigos pra resgatar (outubro 2023) - Mobile Gamer25 março 2025
você pode gostar
-
 HD wallpaper: anime girl, sad, school uniform, windy, black hair25 março 2025
HD wallpaper: anime girl, sad, school uniform, windy, black hair25 março 2025 -
 Jogo copa/ mesa c/ 8 cadeiras e arca c/ oratório - Móveis - Área25 março 2025
Jogo copa/ mesa c/ 8 cadeiras e arca c/ oratório - Móveis - Área25 março 2025 -
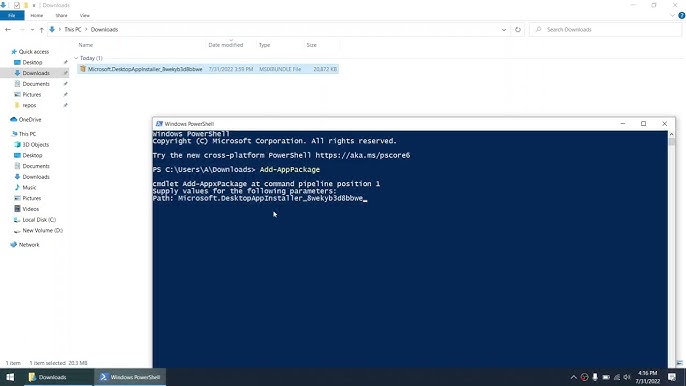 How To Install Msixbundle File In Windows 1125 março 2025
How To Install Msixbundle File In Windows 1125 março 2025 -
/cdn.vox-cdn.com/uploads/chorus_image/image/65497195/zombieland2_sony.0.jpg) Zombieland: Double Tap review: The real monster is 2009-era25 março 2025
Zombieland: Double Tap review: The real monster is 2009-era25 março 2025 -
 Fast & Furious 9 (Velocidade Furiosa 9) - 2021 em 2023 Filmes online grátis, Velozes e furiosos filmes, Séries hbo25 março 2025
Fast & Furious 9 (Velocidade Furiosa 9) - 2021 em 2023 Filmes online grátis, Velozes e furiosos filmes, Séries hbo25 março 2025 -
 Você sabe tudo sobre fnaf? (NÍVEL DIFÍCIL)25 março 2025
Você sabe tudo sobre fnaf? (NÍVEL DIFÍCIL)25 março 2025 -
 Stream 【FNAF UTAU】Fight or Flight Nightmare Chica VS Toy Chica25 março 2025
Stream 【FNAF UTAU】Fight or Flight Nightmare Chica VS Toy Chica25 março 2025 -
 Menacing - Definition, Meaning & Synonyms25 março 2025
Menacing - Definition, Meaning & Synonyms25 março 2025 -
 TIROTEIO DE OVO - shellshock.io25 março 2025
TIROTEIO DE OVO - shellshock.io25 março 2025 -
 Steam recebe cinco novos jogos grátis; conheça e resgate agora25 março 2025
Steam recebe cinco novos jogos grátis; conheça e resgate agora25 março 2025

