Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Last updated 02 abril 2025
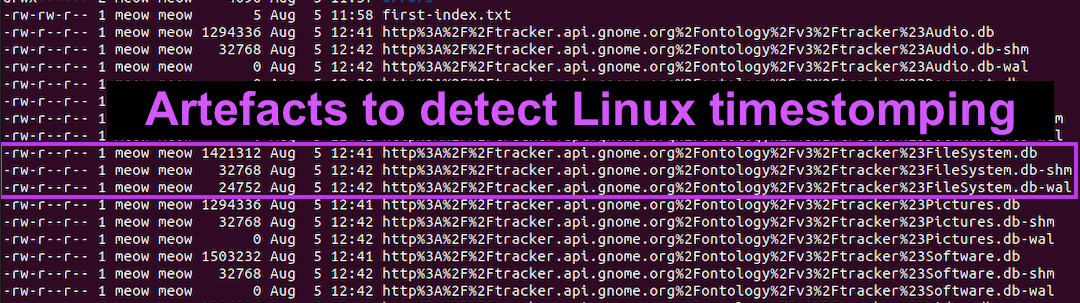
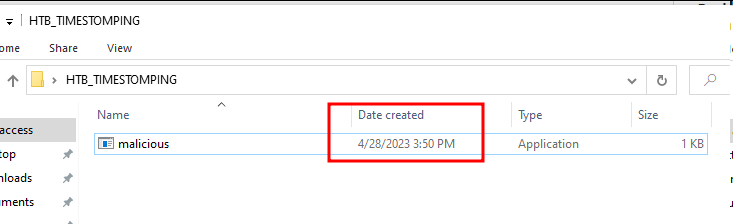
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va

PDF) Three Anti-Forensics Techniques that pose the Greatest Risks

Detecting Linux Anti-Forensics Log Tampering
5 anti-forensics techniques to trick investigators (+ examples

PDF) Artifacts for Detecting Timestamp Manipulation in NTFS on

Detecting Linux Anti-Forensics: Timestomping

Digital Forensics Blog 01 — Anti-Computer Forensics Technique

Defence Evasion Technique: Timestomping Detection – NTFS Forensics

Lina L. en LinkedIn: Detecting Linux Anti-Forensics: Timestomping

A survey on anti-forensics techniques
Recomendado para você
-
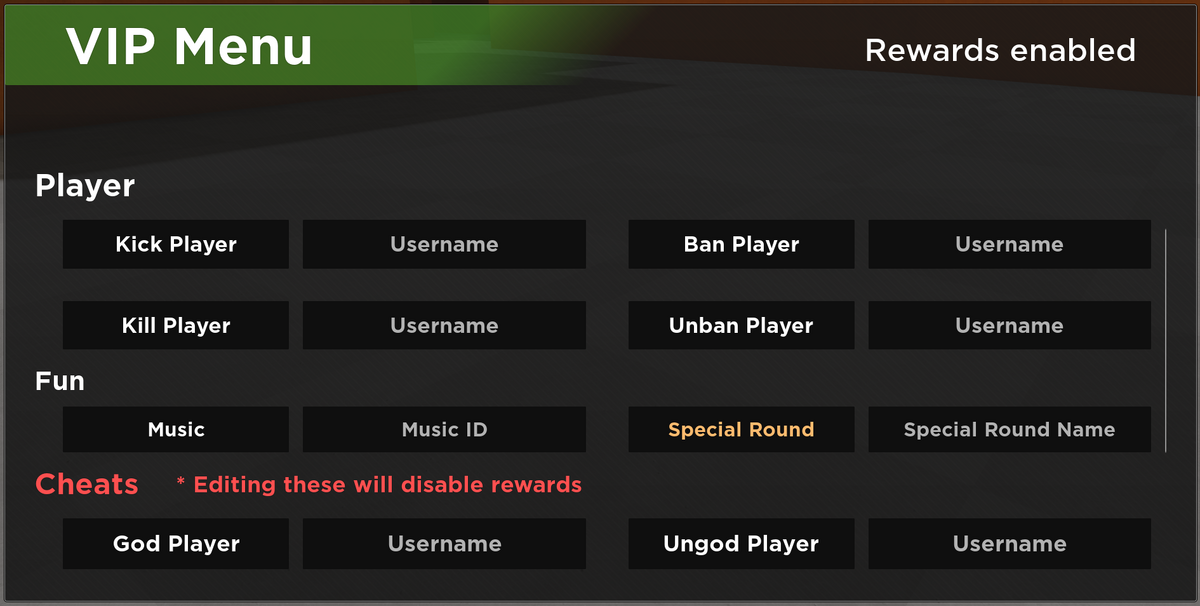 VIP Server Panel, Roblox Evade Wiki02 abril 2025
VIP Server Panel, Roblox Evade Wiki02 abril 2025 -
 TrickGate, a packer used by malware to evade detection since 201602 abril 2025
TrickGate, a packer used by malware to evade detection since 201602 abril 2025 -
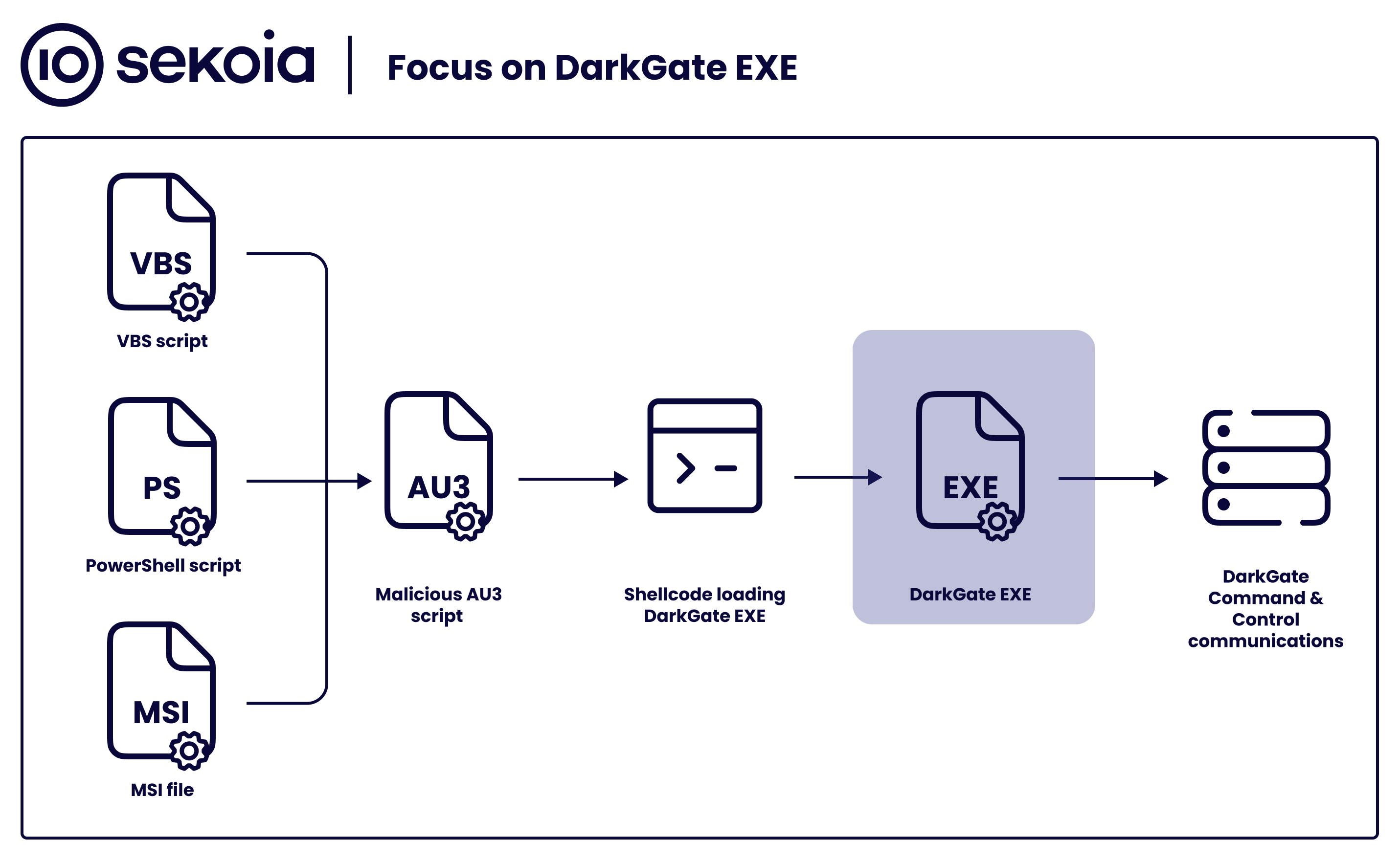
Sekoia.io on X: #DarkGate gained popularity among threat actors02 abril 2025
-
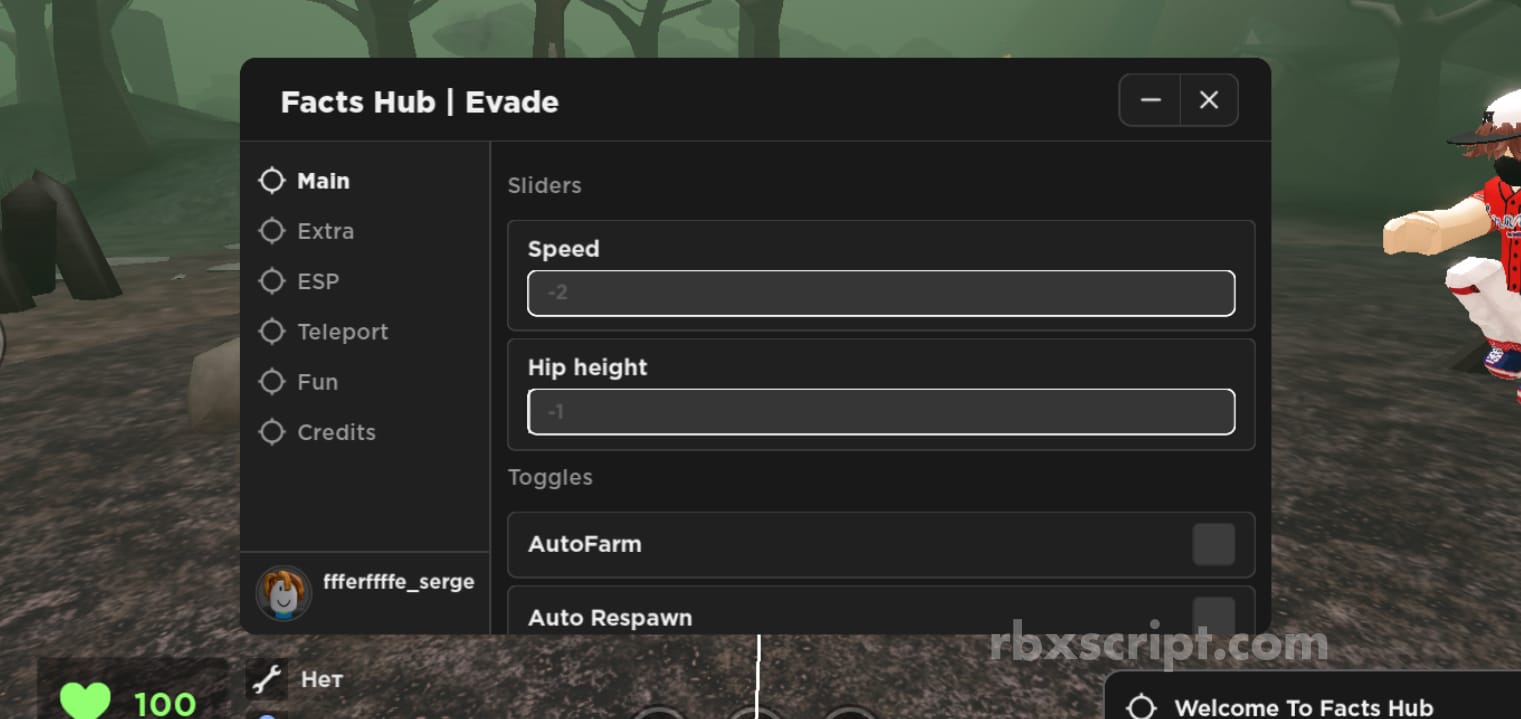 Evade: Walkspeed, Auto Respawn, ESP Mobile Script02 abril 2025
Evade: Walkspeed, Auto Respawn, ESP Mobile Script02 abril 2025 -
 Evade - Script, Fluxus02 abril 2025
Evade - Script, Fluxus02 abril 2025 -
 Evade: Inf Jump, Teleports, ESP Scripts02 abril 2025
Evade: Inf Jump, Teleports, ESP Scripts02 abril 2025 -
How To use WSReborn Evade and TargetSelector !!!02 abril 2025
-
 ToddyCat: Keep calm and check logs02 abril 2025
ToddyCat: Keep calm and check logs02 abril 2025 -
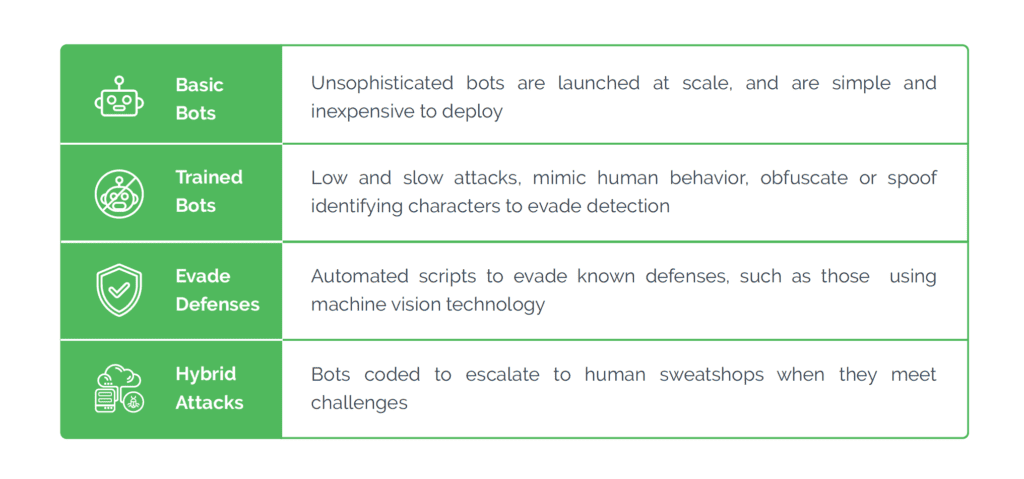 What Is Bot Detection?02 abril 2025
What Is Bot Detection?02 abril 2025 -
 How to Use MSFconsole's Generate Command to Obfuscate Payloads & Evade Antivirus Detection « Null Byte :: WonderHowTo02 abril 2025
How to Use MSFconsole's Generate Command to Obfuscate Payloads & Evade Antivirus Detection « Null Byte :: WonderHowTo02 abril 2025
você pode gostar
-
 What's the Best Show of the Summer So Far? (POLL)02 abril 2025
What's the Best Show of the Summer So Far? (POLL)02 abril 2025 -
pt3 I Auren The Absolute VS SCP 3812 (spin the wheel boundless) #auren02 abril 2025
-
 NEW LIGHTNING ORB IS OP! Renitsu (Zenitsu) + LIGHTNING ORB02 abril 2025
NEW LIGHTNING ORB IS OP! Renitsu (Zenitsu) + LIGHTNING ORB02 abril 2025 -
 ❤️❤️ Momen Romantis ISSEI & AKENO - BiliBili02 abril 2025
❤️❤️ Momen Romantis ISSEI & AKENO - BiliBili02 abril 2025 -
 Genshin Update on X: ✨New code: EA8RWDMBVRTR ▶️Redeem here02 abril 2025
Genshin Update on X: ✨New code: EA8RWDMBVRTR ▶️Redeem here02 abril 2025 -
 Thanksgiving Day - Achieve Languages - POA02 abril 2025
Thanksgiving Day - Achieve Languages - POA02 abril 2025 -
Pieces of a Woman': Filmmakers channel the grief of child loss - Los Angeles Times02 abril 2025
-
 Design PNG E SVG De Língua Da Cabeça Do Alienígena Para Fora Traço02 abril 2025
Design PNG E SVG De Língua Da Cabeça Do Alienígena Para Fora Traço02 abril 2025 -
 TOP 18 MELHORES JOGOS DE LUTA PARA PS2 (JOGOS NOSTÁLGICOS)02 abril 2025
TOP 18 MELHORES JOGOS DE LUTA PARA PS2 (JOGOS NOSTÁLGICOS)02 abril 2025 -
 Episódio 484, One Piece Wiki02 abril 2025
Episódio 484, One Piece Wiki02 abril 2025