Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 30 março 2025

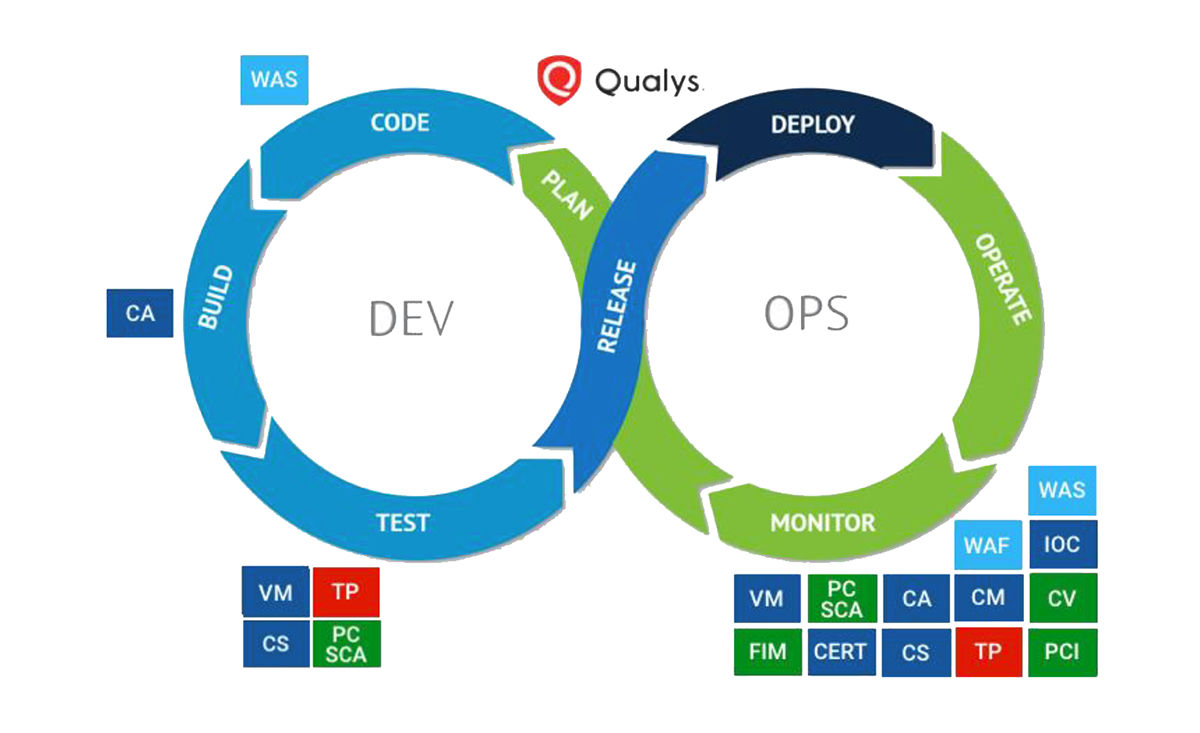
Assess Vulnerabilities, Misconfigurations in CI/CD Pipeline

Vulnerability Scanning in your CI/CD Pipeline - Part Two

CI/CD Vulnerability Scanning - How to begin your DevSecOps journey
CI/CD Security: What is it and How to Protect Your Pipelines
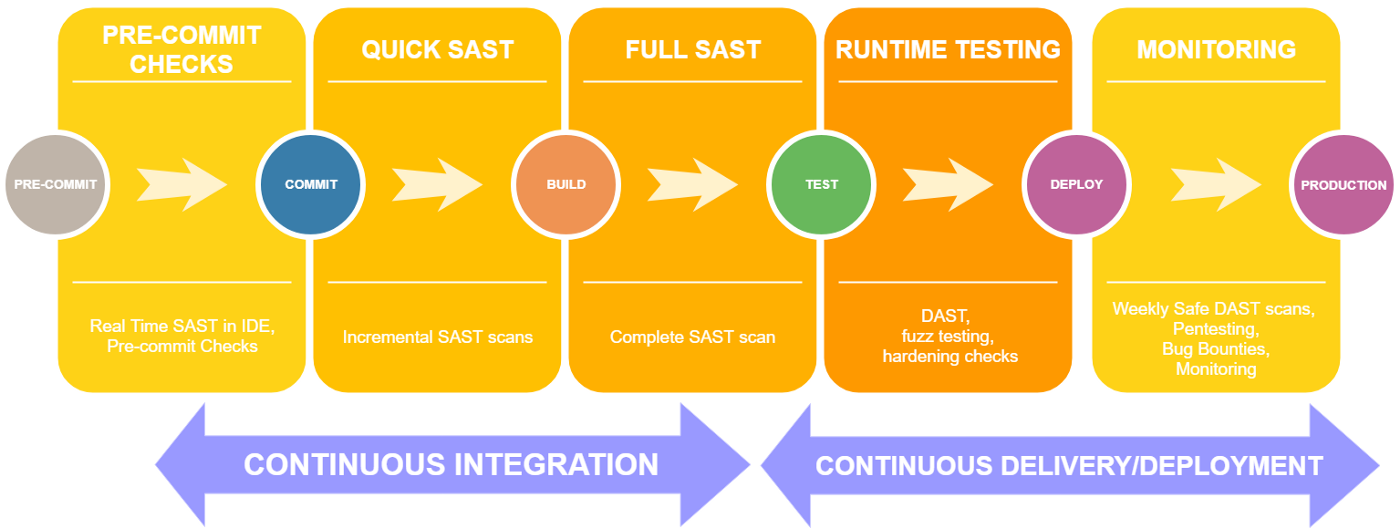
Integrating Web Vulnerability Scanners in Continuous Integration: DAST for CI/CD — Probely
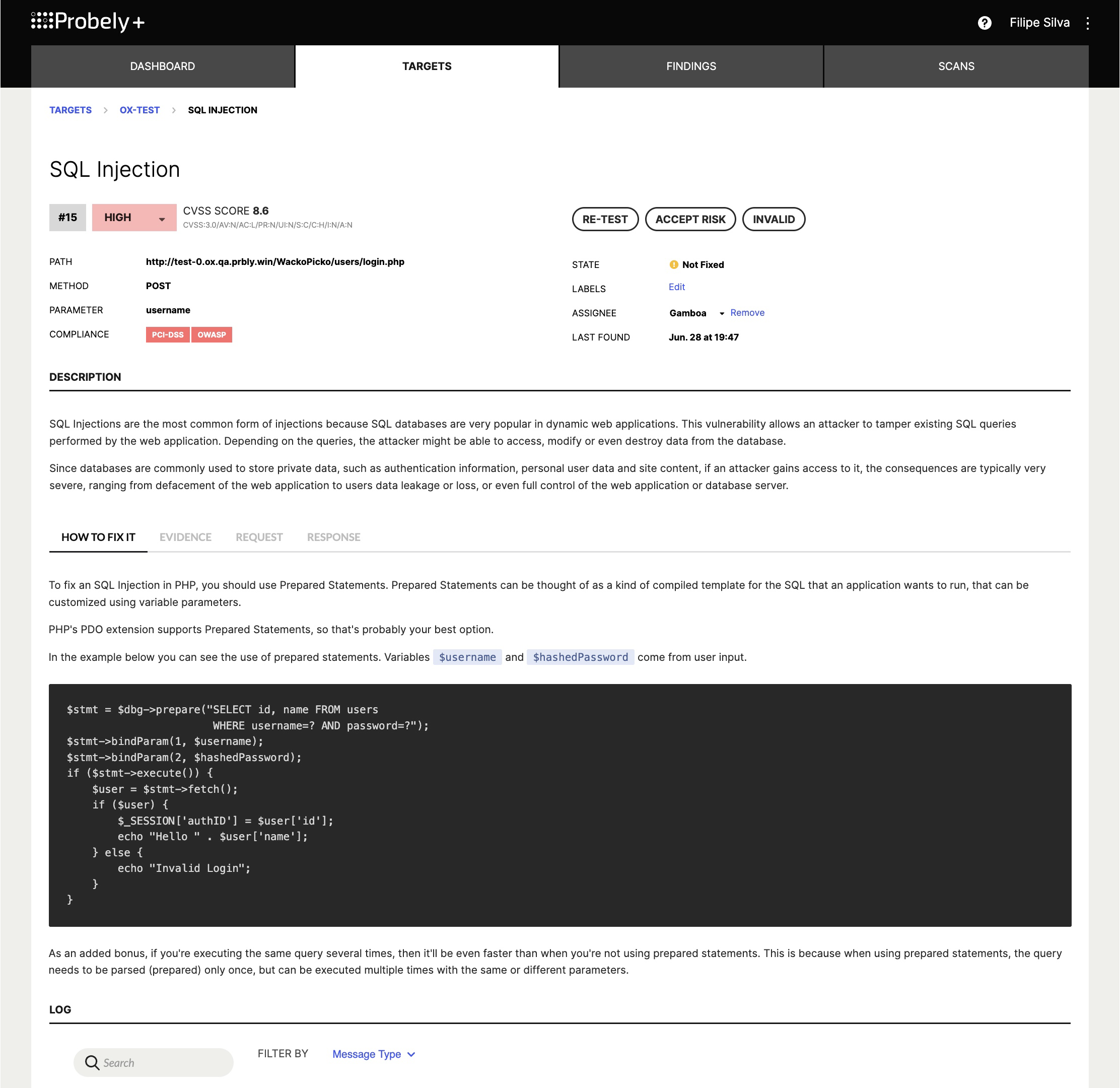
Integrating Web Vulnerability Scanners in Continuous Integration: DAST for CI/CD — Probely

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub

OWASP Top 10 CI/CD Security Risks
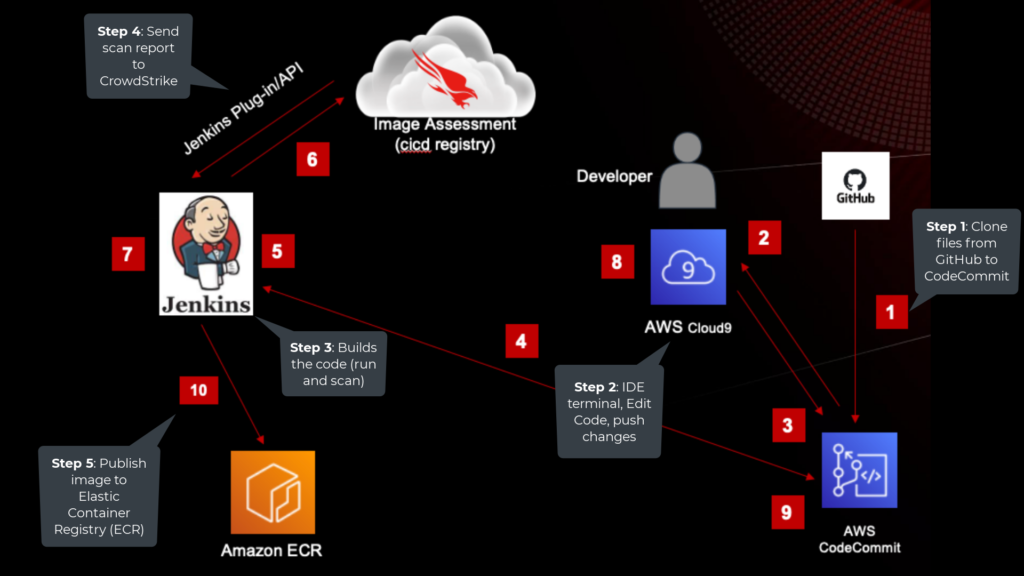
Securing your Jenkins CI/CD Container Pipeline with CrowdStrike
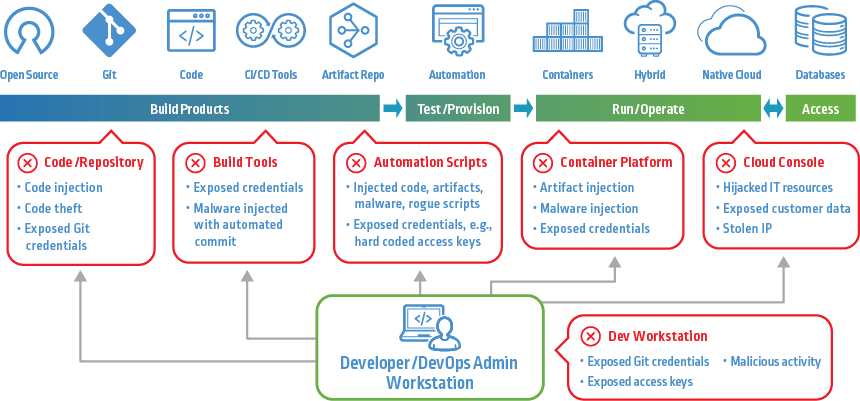
What is CI CD Pipeline? - CI/CD Pipeline Definition

What is CI/CD, and How to Integrate Security? - GuardRails
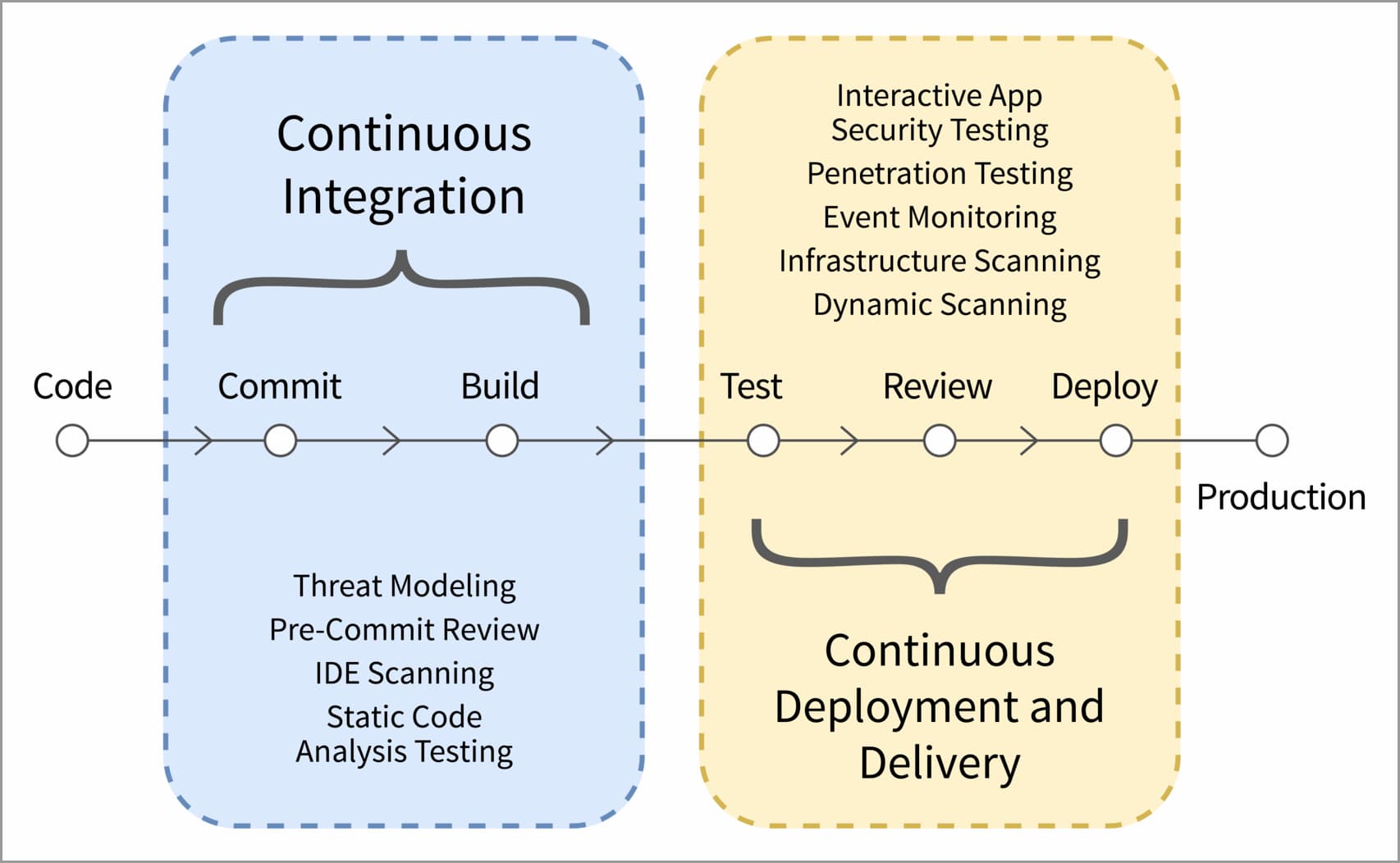
Getting Started With CI/CD Pipeline Security - DZone Refcardz

Integrate Security and Compliance into Your CI/CD Pipeline - The New Stack
Recomendado para você
-
 How the Nexus iOS System Works — Nexus iOS30 março 2025
How the Nexus iOS System Works — Nexus iOS30 março 2025 -
 Tools of the trade: Scan Gauge kits - Bite Magazine30 março 2025
Tools of the trade: Scan Gauge kits - Bite Magazine30 março 2025 -
Nexus iOS (@nexusios_dental) • Instagram photos and videos30 março 2025
-
 Scan app30 março 2025
Scan app30 março 2025 -
 Nexus scanner reference for STO30 março 2025
Nexus scanner reference for STO30 março 2025 -
Nexus iOS Scan Example on Vimeo30 março 2025
-
 DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server30 março 2025
DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server30 março 2025 -
 Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I30 março 2025
Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I30 março 2025 -
 Dr. Effie Habsha Unboxing Nexus iOS Generation 2 Scan Gauges #dentist #dentistry #dentalimplants30 março 2025
Dr. Effie Habsha Unboxing Nexus iOS Generation 2 Scan Gauges #dentist #dentistry #dentalimplants30 março 2025 -
 Resources - ClearEdge3D30 março 2025
Resources - ClearEdge3D30 março 2025
você pode gostar
-
 String-String Fruit showcase on blox piece30 março 2025
String-String Fruit showcase on blox piece30 março 2025 -
 Mob Psycho 100 Divine Tree 3 ~Dimple Is~ (TV Episode 2022) - IMDb30 março 2025
Mob Psycho 100 Divine Tree 3 ~Dimple Is~ (TV Episode 2022) - IMDb30 março 2025 -
 CPUs Intel Core i7-13700K e AMD Ryzen 7 7700X têm desempenhos similares em testes vazados30 março 2025
CPUs Intel Core i7-13700K e AMD Ryzen 7 7700X têm desempenhos similares em testes vazados30 março 2025 -
 Gran Turismo 7 sees gentle 13% boost in PS5 players after film30 março 2025
Gran Turismo 7 sees gentle 13% boost in PS5 players after film30 março 2025 -
 The Dark Occult on Steam30 março 2025
The Dark Occult on Steam30 março 2025 -
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2020/n/F/01bjkoS3q7ciTBxLqo0Q/brasil-1996.png) Derrota de Portugal mantém Brasil como único país a unificar os títulos mundiais de futebol e futsal, mundo do futsal30 março 2025
Derrota de Portugal mantém Brasil como único país a unificar os títulos mundiais de futebol e futsal, mundo do futsal30 março 2025 -
MOUSE! Spotlight on Snapchat30 março 2025
-
 Heroes of the Storm Review - GameSpot30 março 2025
Heroes of the Storm Review - GameSpot30 março 2025 -
 Saiba tudo o que precisa para pegar seu personagem 5 estrelas : r30 março 2025
Saiba tudo o que precisa para pegar seu personagem 5 estrelas : r30 março 2025 -
 Análise de Kimi no na wa (Your Name), by Grupo de Estudo Arte Japonesa Unifesp30 março 2025
Análise de Kimi no na wa (Your Name), by Grupo de Estudo Arte Japonesa Unifesp30 março 2025
