Algorithms, Free Full-Text
Por um escritor misterioso
Last updated 26 março 2025
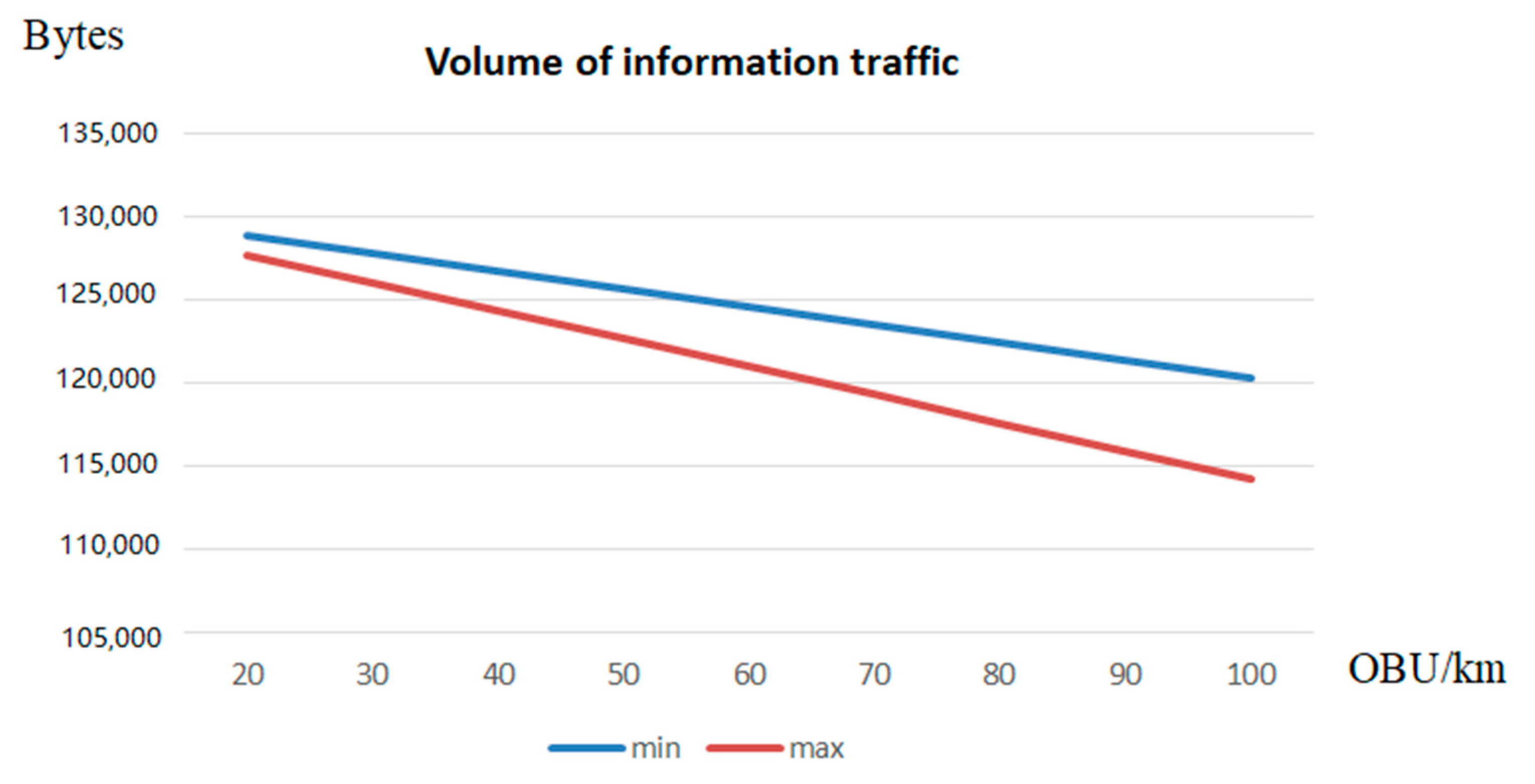
Authentication protocols are expanding their application scope in wireless information systems, among which are low-orbit satellite communication systems (LOSCS) for the OneWeb space Internet, automatic object identification systems using RFID, the Internet of Things, intelligent transportation systems (ITS), Vehicular Ad Hoc Network (VANET). This is due to the fact that authentication protocols effectively resist a number of attacks on wireless data transmission channels in these systems. The main disadvantage of most authentication protocols is the use of symmetric and asymmetric encryption systems to ensure high cryptographic strength. As a result, there is a problem in delivering keys to the sides of the prover and the verifier. At the same time, compromising of keys will lead to a decrease in the level of protection of the transmitted data. Zero-knowledge authentication protocols (ZKAP) are able to eliminate this disadvantage. However, most of these protocols use multiple rounds to authenticate the prover. Therefore, ZKAP, which has minimal time costs, is developed in the article. A scheme for adapting protocol parameters has been developed in this protocol to increase its efficiency. Reductions in the level of confidentiality allow us to reduce the time spent on the execution of the authentication protocol. This increases the volume of information traffic. At the same time, an increase in the confidentiality of the protocol entails an increase in the time needed for authentication of the prover, which reduces the volume of information traffic. The FPGA Artix-7 xc7a12ticsg325-1L was used to estimate the time spent implementing the adaptive ZKAP protocol. Testing was performed for 32- and 64-bit adaptive authentication protocols.
Free Text Redaction - Delphix Masking 6.0.17
Data Structures and Algorithms Online Courses : Free and Paid

The Algorithms Illuminated Book Series

Free Course: Algorithms Course - Graph Theory Tutorial from a

Article recommendation with Personalized PageRank and Full Text

Algorithms, Part I
Genetic Algorithms And Investment Strategies Download - Colaboratory
Listen Free to Automate This: How Algorithms Came to Rule Our
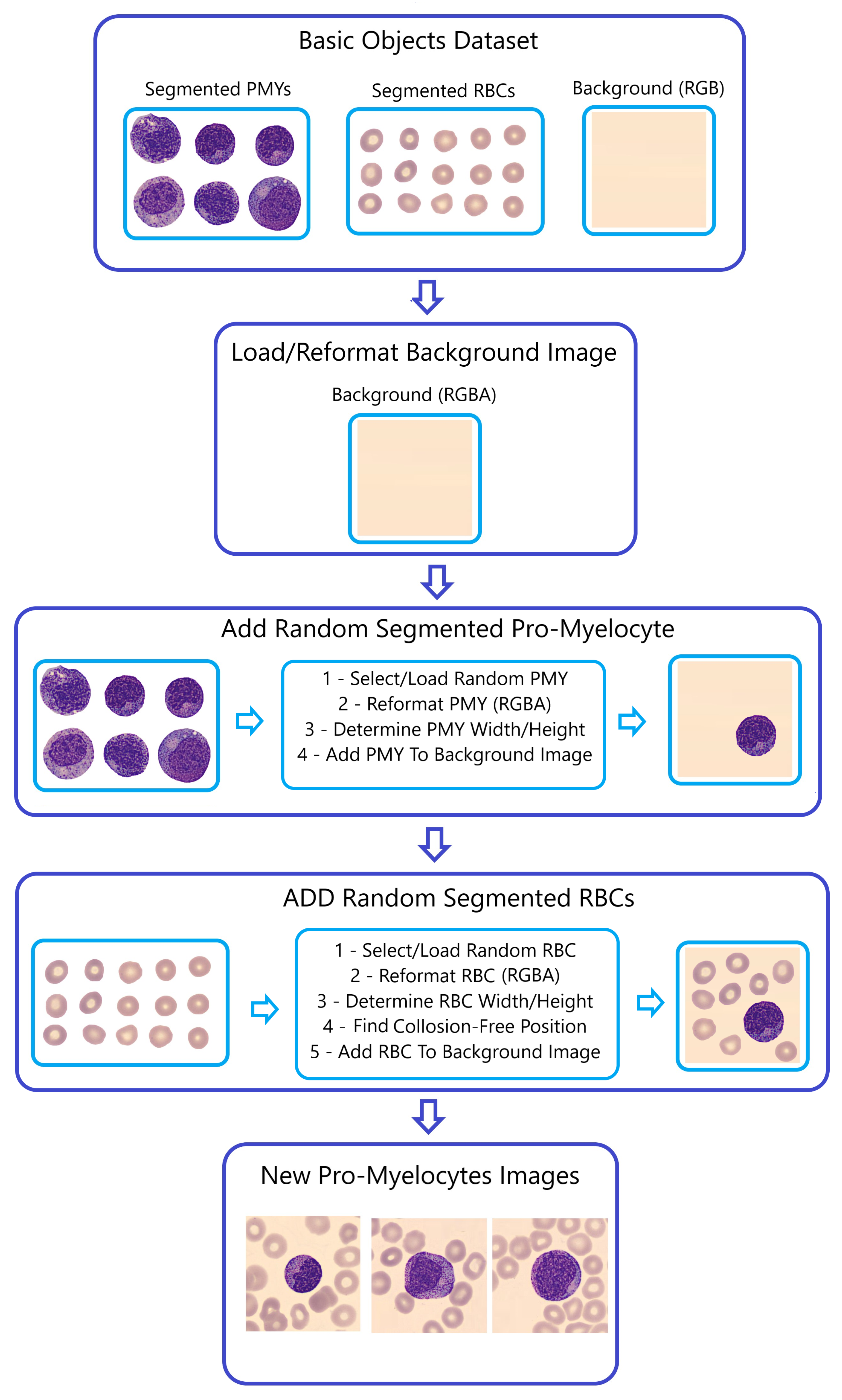
Algorithms, Free Full-Text

PDF] New Projection-free Algorithms for Online Convex Optimization

Free Algorithms Book
Random Structures & Algorithms - Wiley Online Library

Algorithms, 4th Edition by Robert Sedgewick and Kevin Wayne

Algorithms full tutorial

Large Scale Text Search Algorithm with Tries: A Tutorial
Recomendado para você
-
![Project New World Codes Wiki - PNW [New Update] - Try Hard Guides](https://tryhardguides.com/wp-content/uploads/2021/07/featured-project-new-world-codes.jpg) Project New World Codes Wiki - PNW [New Update] - Try Hard Guides26 março 2025
Project New World Codes Wiki - PNW [New Update] - Try Hard Guides26 março 2025 -
 Codes, Project New world Wiki26 março 2025
Codes, Project New world Wiki26 março 2025 -
 FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)26 março 2025
FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)26 março 2025 -
 Roblox - Códigos para o Project New World (julho 2023) - Critical Hits26 março 2025
Roblox - Códigos para o Project New World (julho 2023) - Critical Hits26 março 2025 -
 New World26 março 2025
New World26 março 2025 -
Slave voyages: the transatlantic trade in enslaved Africans26 março 2025
-
Elections in digital times: a guide for electoral practitioners26 março 2025
-
 New video games coming out this week Super Mario Odyssey, Assassin's Creed Origins, Wolfenstein 226 março 2025
New video games coming out this week Super Mario Odyssey, Assassin's Creed Origins, Wolfenstein 226 março 2025 -
The Role of sound groundwater resources management and governance to achieve water security26 março 2025
-
 Top 10 Trending Metaverse Projects of The Week - NFT News Pro26 março 2025
Top 10 Trending Metaverse Projects of The Week - NFT News Pro26 março 2025
você pode gostar
-
 Anime Archives - Page 632 of 671 - Anime Trending26 março 2025
Anime Archives - Page 632 of 671 - Anime Trending26 março 2025 -
 Street Fighter: Duel26 março 2025
Street Fighter: Duel26 março 2025 -
 Human Dream Sans by percilapearljackson on DeviantArt26 março 2025
Human Dream Sans by percilapearljackson on DeviantArt26 março 2025 -
 Split: Why Mental Health Experts Are Critical of the Movie26 março 2025
Split: Why Mental Health Experts Are Critical of the Movie26 março 2025 -
 How to Place an Item in Minecraft26 março 2025
How to Place an Item in Minecraft26 março 2025 -
 Mahjong: Jogo Cerebral26 março 2025
Mahjong: Jogo Cerebral26 março 2025 -
 The last of us part II 1080P, 2K, 4K, 5K HD wallpapers free26 março 2025
The last of us part II 1080P, 2K, 4K, 5K HD wallpapers free26 março 2025 -
Comics Maker Meme Face Maker - Apps on Google Play26 março 2025
-
 Gol quadrado branco rebaixado com roda originais26 março 2025
Gol quadrado branco rebaixado com roda originais26 março 2025 -
 Pin de Maria Eduarda em Instagram Perguntas para amigos, Perguntas e respostas brincadeira, Quiz de perguntas engraçadas26 março 2025
Pin de Maria Eduarda em Instagram Perguntas para amigos, Perguntas e respostas brincadeira, Quiz de perguntas engraçadas26 março 2025


