Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 13 abril 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Sick leave abuse, poor performance and the disciplinary code - Labour Guide South Africa

How to use ChatGPT as a learning tool
GitHub - D4stiny/ExceptionOrientedProgramming: Abusing exceptions for code execution.

Code of Ethics for Government Services Poster

Cabotegravir for the prevention of HIV-1 in women: results from HPTN 084, a phase 3, randomised clinical trial - The Lancet

Abusing Exceptions for Code Execution, Part 2

How to Fix a Toxic Culture

Top 10 secure C++ coding practices - Incredibuild

Writing Exploits for Win32 Systems from Scratch, NCC Group Research Blog

Cybersecurity and digital trade: Getting it right
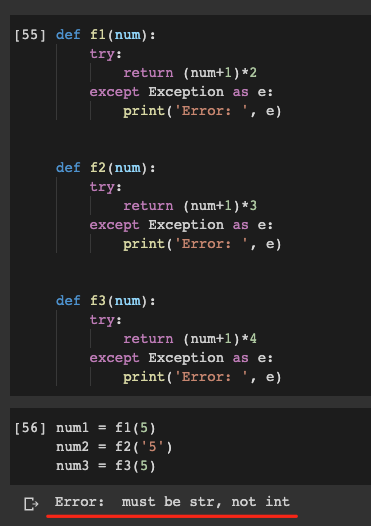
Do Not Abuse Try Except In Python, by Christopher Tao
Blindside: A New Technique for EDR Evasion with Hardware Breakpoints - Cymulate

CVE-2018-8611 Exploiting Windows KTM Part 5/5 – Vulnerability detection and a better read/write primitive, NCC Group Research Blog
Recomendado para você
-
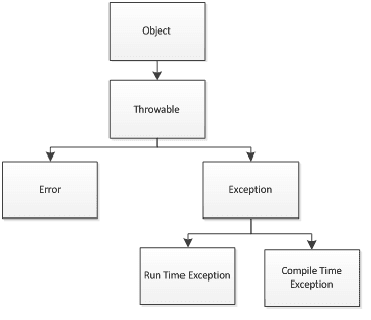 Types of Exceptions - w3resource13 abril 2025
Types of Exceptions - w3resource13 abril 2025 -
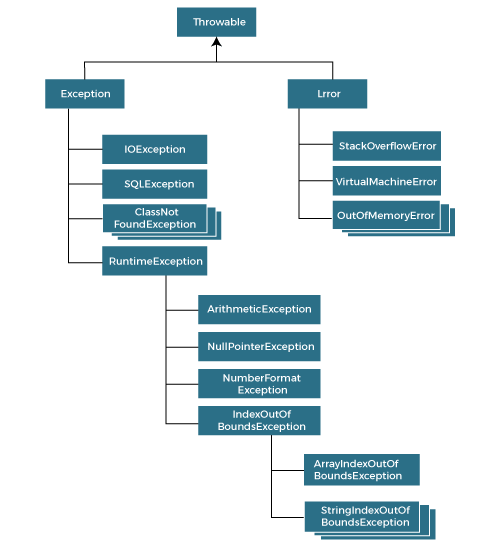 Exception Handling in Java Java Exceptions - javatpoint13 abril 2025
Exception Handling in Java Java Exceptions - javatpoint13 abril 2025 -
 Types of exceptions in Java: checked, unchecked, and custom13 abril 2025
Types of exceptions in Java: checked, unchecked, and custom13 abril 2025 -
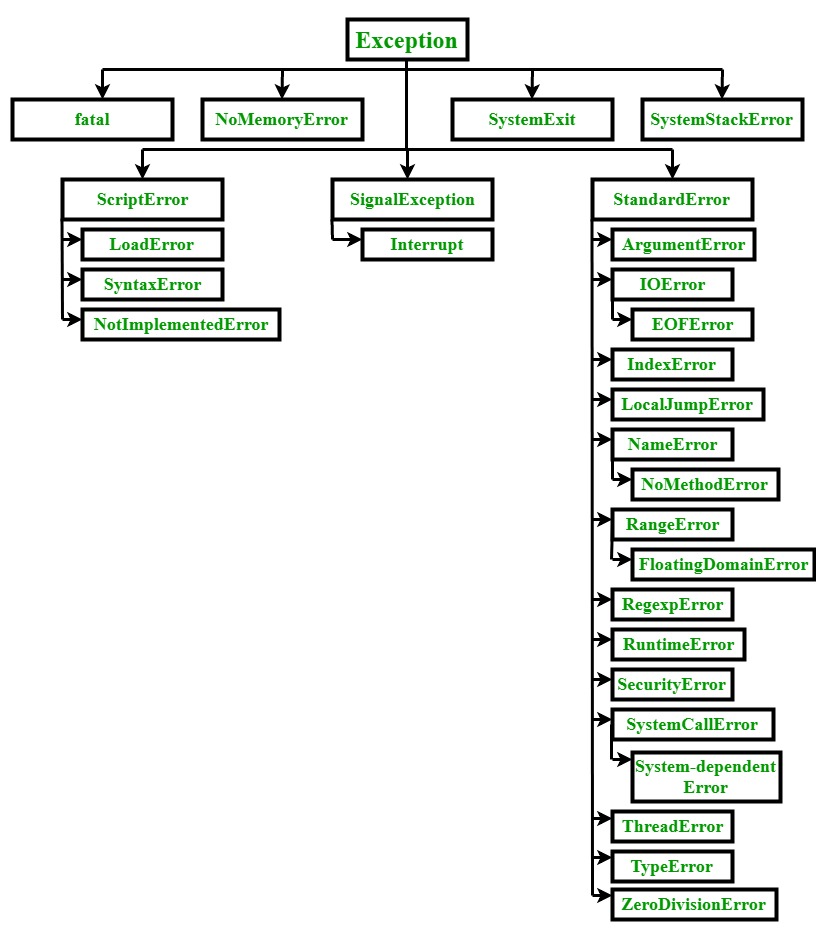 Ruby Exceptions - GeeksforGeeks13 abril 2025
Ruby Exceptions - GeeksforGeeks13 abril 2025 -
 Exceptions in Java - How to Program with Java13 abril 2025
Exceptions in Java - How to Program with Java13 abril 2025 -
 10 Commonplace Exceptions in Selenium WebDriver13 abril 2025
10 Commonplace Exceptions in Selenium WebDriver13 abril 2025 -
 Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow13 abril 2025
Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow13 abril 2025 -
 Resolve Timecard Exceptions - Hourly Timecard13 abril 2025
Resolve Timecard Exceptions - Hourly Timecard13 abril 2025 -
 Invoice Exceptions: Where they come from and how to prevent them13 abril 2025
Invoice Exceptions: Where they come from and how to prevent them13 abril 2025 -
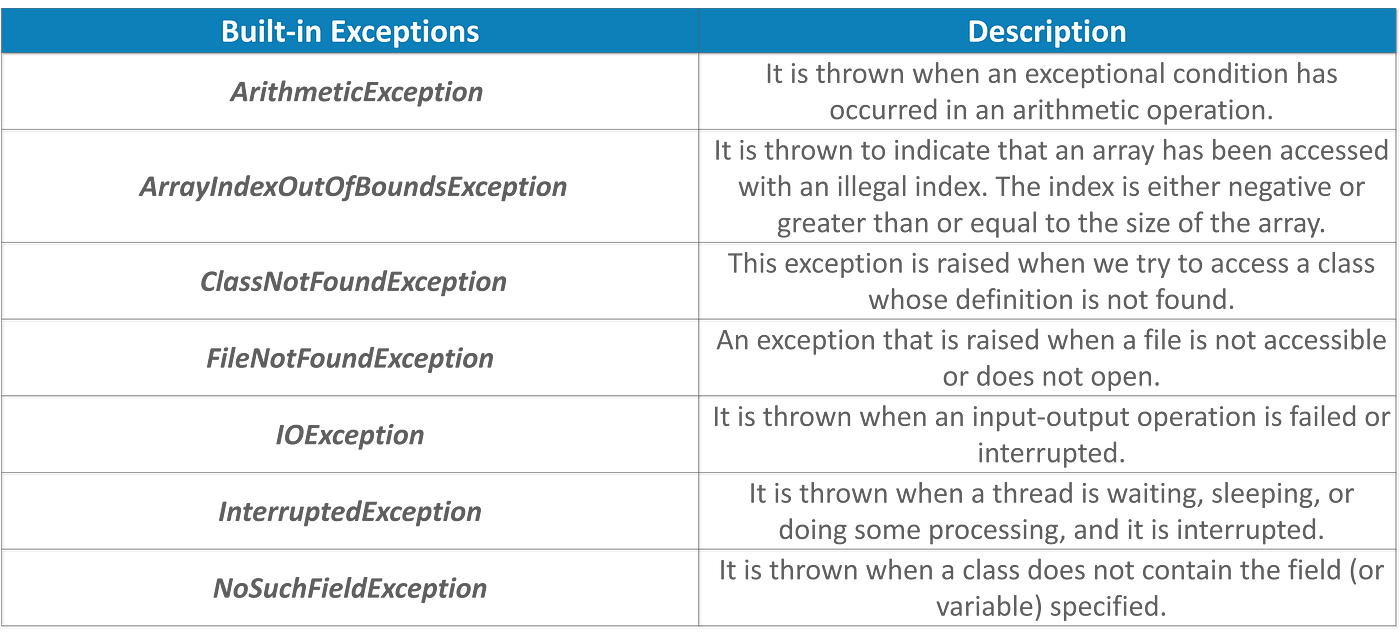 Exception Handling in Java — A Beginners Guide to Java Exceptions, by Swatee Chand, Edureka13 abril 2025
Exception Handling in Java — A Beginners Guide to Java Exceptions, by Swatee Chand, Edureka13 abril 2025
você pode gostar
-
 design de interface de jogo de plataforma 8619671 Vetor no Vecteezy13 abril 2025
design de interface de jogo de plataforma 8619671 Vetor no Vecteezy13 abril 2025 -
connie talbot somewhere over the rainbow|TikTok Search13 abril 2025
-
 Assistir Tondemo Skill de Isekai Hourou Meshi Episodio 6 Online13 abril 2025
Assistir Tondemo Skill de Isekai Hourou Meshi Episodio 6 Online13 abril 2025 -
 RTX 2080 e 16 GB de RAM: requisitos de sistema para Dragon's Dogma 2 revelados13 abril 2025
RTX 2080 e 16 GB de RAM: requisitos de sistema para Dragon's Dogma 2 revelados13 abril 2025 -
 O' Holy Night Die - O' Holy Night -Crafter's Companion US13 abril 2025
O' Holy Night Die - O' Holy Night -Crafter's Companion US13 abril 2025 -
 EvoWorld.io - June 35% exp bonus & 100% special exp bonus13 abril 2025
EvoWorld.io - June 35% exp bonus & 100% special exp bonus13 abril 2025 -
 Doctorkev Does Fate/Stay Night: Part 1: Fate route, by DoctorKev, AniTAY-Official13 abril 2025
Doctorkev Does Fate/Stay Night: Part 1: Fate route, by DoctorKev, AniTAY-Official13 abril 2025 -
 Teenage chess genius could become youngest World Champion - BBC Newsround13 abril 2025
Teenage chess genius could become youngest World Champion - BBC Newsround13 abril 2025 -
 I whatever you — Wei WuXian's Stolen Kiss - Analysing His Emotional13 abril 2025
I whatever you — Wei WuXian's Stolen Kiss - Analysing His Emotional13 abril 2025 -
 Do you know the stories behind the Candy Crush characters?13 abril 2025
Do you know the stories behind the Candy Crush characters?13 abril 2025
